CCAT is on the prowl for backdoors in container environments
The convenience of containerization has generated a lot of buzz in the DevOps world, but that still leaves the need to build security into application development.
Citing a lack of tools in the marketplace, researchers have developed a new utility that enables developers to test their container environments for vulnerabilities.
Cloud containers began their rise in popularity with the launch of Docker in 2013 and the Kubernetes orchestration tool in 2014.
The technology allow developers to bundle their applications with all their requirements, such as libraries and other dependencies, and ship them as a single package, ensuring that the application will run on various virtual machines with different settings and configurations.
Over the past few years, containers have become an attractive option for companies and organizations that want to run applications without becoming engaged in the complexities of managing the technical details of their cloud infrastructure.
Gartner estimates that by 2022, more than 75% of organizations will run containerized apps, as opposed to 30% today.
But in a recent survey by StackRox, 40% of respondents were worried that their company didn’t adequately invest in container security. Even more concerning is that some organizations don’t even take container security threats seriously.
Look what the CCAT dragged in…
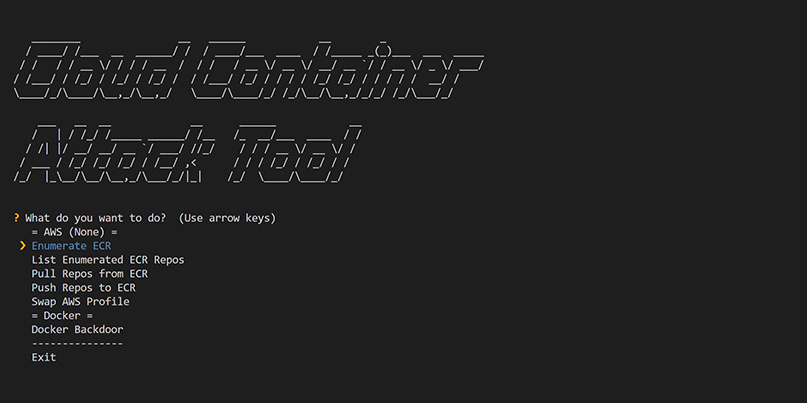
To help improve container security, Jack Ganbold, associate cloud penetration tester at Rhino Security Labs, has developed Cloud Container Attack Tool (CCAT), an open source tool for testing the security of cloud container environments.
“It is possible to attack a container environment from host to container, container to host or both ways,” Ganbold told The Daily Swig.
“To prevent that from happening, we need a secure CI/CD (continuous integration/continuous delivery) pipeline and an infrastructure. Container environments are also very dynamic, which makes their security unique.”
CCAT helps developers and pen testers find possible exploits and backdoors that might allow malicious container images to gain illegal access to their hosting environment.
In an accompanying blog post, Ganbold shows how the tool can be used to create a reverse shell backdoor that gives a malicious Docker image access to Amazon’s Elastic Container Registry.
“We built CCAT to help the community better understand the security implications of container-based services, especially due to containers’ increasing popularity and the lack of offensive tools in the space,” Ganbold said.
Trust, but verify
Ganbold also warned against other poor security practices, such as trusting unverified base images when using containers.
“Since a base image is a starting point for creating custom images, it is super-important to use a trusted base image for many security reasons,” Ganbold told The Daily Swig.
“Also, we do not see companies using signed images. If an image is signed by the provider, consumers can check the image’s proof of origin.”
For the moment, CCAT only support Amazon’s Elastic Container Service but has nonetheless been well-received by the cybersecurity community.
In a recent Twitter thread, Nathan Peck, a developer at AWS, discussed CCAT and how developers can protect their containers against the backdoor exploits it might expose.
Looking ahead, Ganbold said his team was working to integrate support for other major cloud vendors.
“At the moment, we are extending CCAT to Google Cloud Platform (Cloud Run, GKE, GCE, and GCR),” he said.
RECOMMENDED Hack and Slash: Cloud-based video games model opens up fresh security risks