Exploit Prediction Scoring System uses machine learning to help security teams prioritize patches
With thousands of vulnerabilities being discovered and filed every year, one of the greatest challenges security teams face is knowing which threats to deal with first. And untimely responses can result in irreversible security incidents.
A new open source utility released by Kenna Security last week aims to help security teams decide which vulnerabilities will cause a greater threat to their organization and need urgent attention.
The Exploit Prediction Scoring System (EPSS) tool uses machine learning to predict the likeliness that a vulnerability will be exploited in the first 12 months after its discovery.
“EPSS is best at predicting in-the-wild exploitations 12 months after vulnerability publication,” Michael Roytman, chief data scientist at Kenna Security, told The Daily Swig.
What’s the score?
Currently, most organizations assess risks and determine security priorities based on the Common Vulnerability Scoring System (CVSS).
CVSS determines the severity of vulnerabilities based on their characteristics and the confidentiality, integrity, and availability impact they will have on information systems.
But the CVSS system is said to be lacking in several areas. For instance, hackers tend to target popular software more often, but CVSS doesn’t take into account whether the target software is highly specialized or installed in millions of machines across the world.
Added to this is the notion that, given their limited resources, organizations can only address a fraction of the vulnerabilities they face on a daily, weekly, and monthly basis.
“Our research shows that, on average, the typical enterprise can only remediate one out of 10 vulnerabilities per month, as more come out every day,” Roytman says.
“That 10% is critically important and shouldn’t be wasted on false alarms and vulnerabilities that pose limited or no risk.”
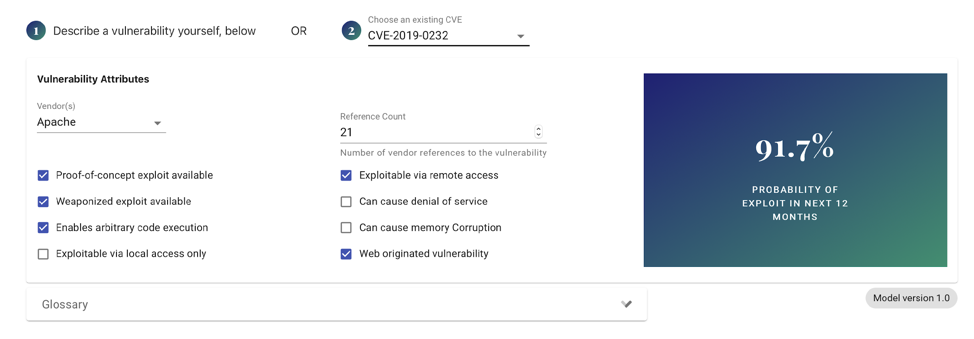 EPSS predicts the likelihood of a vulnerability being exploited within a year of its discovery
EPSS predicts the likelihood of a vulnerability being exploited within a year of its discovery
“The current CVSS system for measuring cyber risk and prioritizing vulnerabilities is inefficient,” Jay Jacobs, co-founder of Cyentia Institute, a security research firm, told The Daily Swig.
“Security teams have the unenviable task of being held responsible for remediating vulnerabilities when they only have the ability to address a small percentage of them.”
He added: “We developed EPSS to help security practitioners make more well-informed decisions, and address threats more efficiently. We expect that organizations using EPSS will be able to improve their security posture and better manage resources.”
Open source ML model
Roytman and Jacobs developed EPSS in collaboration with data scientists and IT professionals from Rand Corporation and Virginia Tech.
The system uses a machine learning model trained in data from over 25,000 vulnerabilities and billions of security events collected over five years to predict which vulnerabilities pose a greater threat based on their similarities to historical records.
“Using data science and machine learning to prioritize vulnerabilities based on risk reduces the average time to patch the riskiest vulnerabilities by more than 40 days compared to other strategies,” Roytman says.
Roytman and Jacobs presented EPSS for the first time at BlackHat USA 2019 in August and released it for public use in late October.
YOU MIGHT ALSO LIKE Using AI to make human security teams great again
The researchers tested the platform on BlueKeep (CVE-2019-0708), a nasty bug found in Windows Remote Desktop Services that allowed remote code execution.
Before there were any reports of BlueKeep attacks, EPSS is said to have correctly predicted with a probability of 95% that it would be exploited within 12 months of its publication. The first BlueKeep exploit surfaced in early November.
“We tested the model on data that we withheld from it,” Roytman says. “The efficiency and coverage metrics we present in the white paper are all based on data the model wasn’t aware of when we trained it.” Roytman also added that several organizations are currently looking into using EPSS in-house.
EPSS builds on previous similar efforts to create exploit prediction models. The researchers hope the free and open source nature of EPSS will make it accessible to a wider audience.
“EPSS itself is commercially open source, and uses only free, publicly available data and is designed to be as simple as possible – a student can implement EPSS in an excel spreadsheet – which means organizations of any maturity level can take advantage immediately, for free,” Roytman says.
READ MORE CVSS update addresses vulnerabilities in critical infrastructure sectors






