SAMMv2, Juice Shop, and testing guide among topics covered during 24-hour security event

An improved software assurance maturity model (SAMM) and a new tutorial tool for the Juice Shop were among the OWASP insights shared at today’s All Day DevOps event.
The free 24-hour conference for software developers included a raft of presentations dedicated to various OWASP (Open Source Web Application Security Project) tools and projects.
Seba Deleersnyder, CEO and co-founder of the infosec consultancy Toreon, discussed the OWASP SAMMv2 (non-HTTPS link) – a model designed to help embed security throughout the development lifecycle.
Deleersnyder, who leads the project, said the model continued to offer a measurable, actionable, and versatile means of improving the software security posture of all types of organizations.
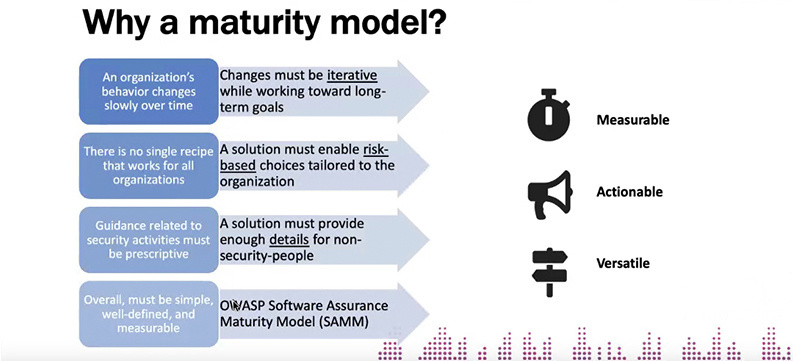 Seba Deleersnyder discussed OWASP SAMMv2 at today's All Day DevOps
Seba Deleersnyder discussed OWASP SAMMv2 at today's All Day DevOps
Launched in early 2019, the second version is “much more iterative” than its predecessor (v1.5), Deleersynder said. This is because changes added to GitHub are now “automatically propagated to the website”.
The new version also adds a new business function to the security lifecycle, taking the total of steps in the process to 15.
The implementation phase will now comprise secure build, secure deployment, and defect management, and come alongside the already established phases of governance, design, verification, and operations.
SAMM2 assessments are meant to assist organizations with self-assessing their risk profile and alignment with these practices, resulting in a scorecard and roadmap.
A focus on community and faster, more iterative improvements, will continue to underpin further developments. Additional OWASP references, process and technical guidance and assessment benchmarking are also in the pipeline.
Beginner? There’s a hacking challenge for that
The OWASP Juice Shop, the JavaScript-coded web app deliberately riddled with vulnerabilities – including the entire OWASP Top 10 – was showcased by Björn Kimminich, a German OWASP chapter board member.
Kimminich, who is project leader for the hacking challenge, demonstrated Hacking Instructor, a new tutorial mode aimed primarily at beginners.
A ‘Juice bot’ guided him through an attempt to implement an SQL injection via an administrator login.
For instance, one query yielded the prompt: “Mhh… The query is still invalid? Can you see why from the new error in the console?”
Suitable for both beginners and experts the Juice Shop’s 89 (and counting) hacking challenges are split across six difficulty levels.
The challenges are gamified, with progress triggering feedback that is tracked on a scoreboard.
Accelerating to limit false positives
The limitations of SAST and DAST tools were also addressed by sibling penetration testers Glenn and Riccardo ten Cate in their talk on the OWASP Security Knowledge Framework.
These tools can only reliably find 20% of vulnerabilities through the use of the 280 security controls outlined in ASVS (application security verification standard), said Glenn, who is the security chapter leader for ING Belgium.
A vulnerability management system like DefectDojo, meanwhile, can accelerate the laborious manual verification work created by false positives.
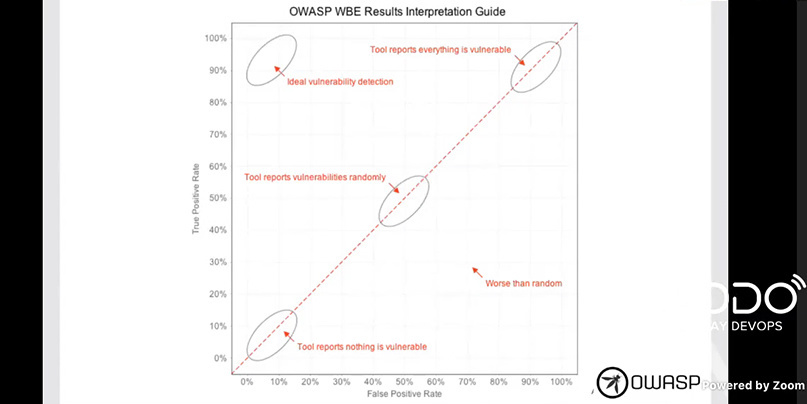
“We are living in the era of insecure software”, said Matteo Meucci, CEO and co-founder at Minded Security, adding how the security efforts of software developers are currently being stymied by time constraints, complexity, and deployment frequency.
Discussing the OWASP Testing Guide (PDF), launched in 2004, Meucci said the timeline for reporting and fixing critical vulnerabilities – up to one month to share, up to six months to fix – remains unacceptably long.
“We need instant security feedback,” said Meucci, who has been in charge of the OWASP Testing Guide since 2006.
Key to achieving a fix within hours of discovery are new standards, more automation, and promptly sharing vulnerability information internally, he said.
Sharing is caring
The conference, which is still ongoing, also saw the presentation of DevSlop – a collaborative space for making, sharing, and learning from mistakes found in DevSecOps.
Tanya Janca, co-founder and CEO of Security Sidekick, walked viewers through the seven steps of ‘Patty the Pipeline’ – verify third party components, SAST, DAST, infrastructure, security hygiene, Secret Store, and scanning for secrets and credentials.

And Simon Bennetts, OWASP Zed Attack Proxy (ZAP) project leader and member of Mozilla’s cloud services security team, proclaimed ZAP HUD as effective in automating within DevOps.
He also explained how ZAP UIs aid automation setup and why the HUD is ideal for manual testing.
Broadcast through YouTube, All Day DevOps is pegged as the world's biggest DevOps conference. The virtual event started at 08:00 UTC and features more than 150 speakers over 24-hours.
OWASP sessions still to come on the schedule include John Melton on the OWASP AppSensor, Chaim Sanders and Franziska Buehler on the OWASP Core Rule Set, and Caroline Wong with an OWASP top 10 overview.
RELATED OWASP reveals top 10 security threats facing API ecosystem






