Fraudulent emails ask for sensitive personal data and include malicious links and attachments

UPDATED The World Health Organization (WHO) has warned that it is being impersonated by cybercriminals in a phishing campaign that exploits anxieties surrounding the latest coronavirus outbreak.
In a recently posted security alert, the WHO said the offending emails ask recipients to hand over sensitive information like usernames or passwords, and include malicious links and attachments that trigger the installation of malware.
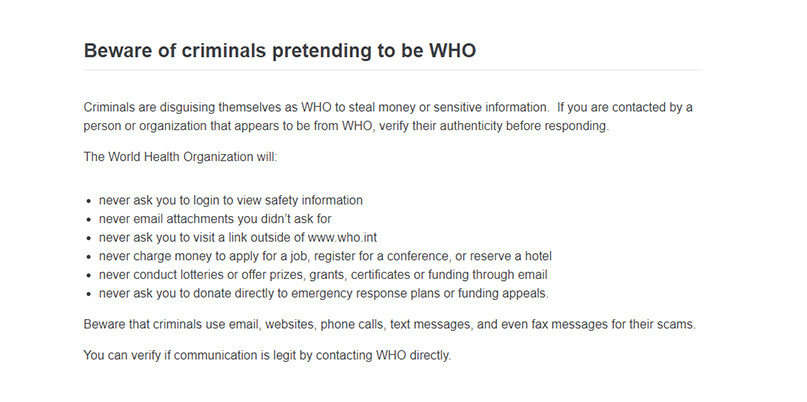
“Criminals are disguising themselves as WHO to steal money or sensitive information,” the alert reads. “If you are contacted by a person or organization that appears to be from WHO, verify their authenticity before responding.”
Email recipients can verify the sender’s authenticity, as well as report scams, by contacting the WHO directly, the organization said.
The WHO, which declared the outbreak of the unique coronavirus pathogen Covid-19 a global public health emergency on January 30, also advises recipients to check the sender’s email address.
Legitimate emails from WHO employees always follow the ‘person@who.int’ format, while web links will always start with ‘https://www.who.int’, the Geneva-based health agency confirmed.
Disaster fraud
Christian Lindmeier, spokesperson for the WHO, told The Daily Swig that the agency had “received specific information from the WHO Threat Intelligence service” about fraudulent emails flagged by Sophos on February 5. The emails, purporting to come from the WHO, asked users to download measures for avoiding the now notorious coronavirus strain.
Kaspersky has discovered a similar campaign that hijacked the US Centers for Disease Control and Prevention’s identity in an attempt to trick people into clicking a malicious link.
Unscrupulous cybercrooks have also used Covid-19, which has now claimed more than 1,800 lives, to spread Emotet malware in Japan.
Although the WHO’s latest warning may go some way to helping internet users be on their guard, this latest campaign is by no means an isolated incident.
Major global crises, such as health scares, natural disasters or terror attacks, have long been a favored target for so-called ‘disaster fraud’ phishing campaigns, which exploit fear, confusion, and, in the case of phony donation requests, compassion.
Kelvin Murray, senior threat researcher at Webroot, said such global crises helped to fuel a 640% rise in phishing URLs reported in the 2020 Webroot Threat Report, which was released today.
“It’s unsurprising that the World Health Organization is currently being impersonated at scale, as scams based off current news are always going to be more effective, especially when tied to emotive topics in the public interest,” he told The Daily Swig.
“Whereas in the past we have seen fake stories about Conor McGregor or Elon Musk driving click-through to malicious twitter links, today we see coronavirus emails driving click-through to threats such as Emotet.”
Javvad Malik, security awareness advocate at security training provider KnowBe4, added: “We’ve seen several variations of phishing emails under the guise of warnings, to charitable donations, to flight and travel updates.
“Many of these phishing emails don’t contain any malicious attachments which can be scanned, so they have a high success rate in reaching the user’s desktop.”
Mitigation measures
Murray recommends that risk mitigation measures should include email filtering, antivirus protection, strong password policies, security awareness training, and backing up data to a secure location.
Both Facebook and Twitter have issued statements explaining their own measures for combating the spread of misinformation and scams that exploit the coronavirus crisis.
The WHO is also urging the public to not be rushed into handing out personal information, and to be suspicious of requests for usernames and passwords in order to access what should be freely available information.
Scammers can request such information not just through emails but websites, phone calls, text messages, and even fax messages too, the alert warns.
Anyone who believes they may have given sensitive data to cybercriminals are advised to immediately update their relevant login credentials.
Christian Lindmeier of the WHO told The Daily Swig that they had “received almost daily reports of phishing attempts reported by WHO users.”
He added: “Phishing campaigns have frequently happened in multiple forms and topics (examples: HR, sales or financial opportunity, and health outbreaks).
“Some campaigns are very convincing when content quality is good and there are no English mistakes.”
This article has been updated with comments from the WHO.
RELATED Black Hat Asia 2020 postponed due to coronavirus epidemic






