Plugin library bug is exploitable with no more than the opening of a malicious file
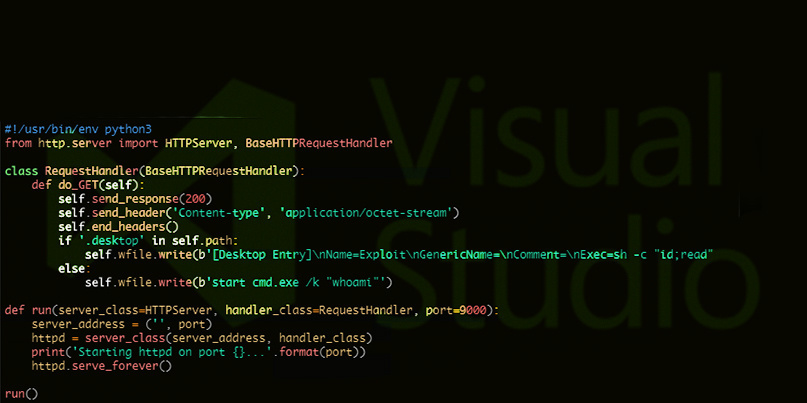
XML Language Server (LSP4XML), a popular library used by XML plugins, has been patched to resolve a severe vulnerability that can be exploited to remotely execute code on a victim’s device.
The security flaw, tracked as CVE-2019-18213, is an XML External Entity (XXE) issue that can be triggered merely by opening a malicious file, leading to a further RCE vulnerability via path traversal, CVE-2019-18212.
LSP4XML is used to parse XML files in integrated development environments (IDEs) such as Visual Studio Code via extensions including RedHat’s XML Language Support extension (VSCode-XML), Eclipse’s wildwebdeveloper and Theia’s XML extension. Other extensions may also be affected.
Cybersecurity researchers from Italian IT company Shielder disclosed the existence of the vulnerability last week.
Strange behavior
In a blog post, Shielder team members under the names ‘thezero’ and ‘zi0black’ said that a penetration test using a standard XXE payload uncovered strange default behavior in how Visual Studio Code handled HTTP requests.
Spotted “by chance”, the researchers found that VSCode-XML, a recommended installation when users open an XML file for the first time in the software, was the source of the problem.
“It turned out that the XXE vulnerability [was] in LSP4XML itself: when opening an XML file inside Visual Studio Code with VSCode-XML installed, every time the file is edited or saved, LSP4XML parses the file locally and reports any error(s) in the VS Code interface,” the researchers said.
Once a malicious XML file is opened, it is possible to force a path traversal while a cache file is being saved due to how URLs are retrieved and cached.
This resulted in the ability to write an arbitrary remote file in an arbitrary local directory, according to the team.
Check out the latest security vulnerability news from The Daily Swig
However, the attack chain does have limits – it is not possible to write over existing files and attacks can only occur within the confines of user privilege. The exploit chain also requires a restart or log off/log on.
Proof-of-concept code has been published for both Windows and Linux systems.
The vulnerability was discovered on September 20 and reported to RedHat Security a week later.
The issue was then forwarded to the VSCode-XML developer team, who acknowledged the bug on October 1 and managed to develop a patch suitable for review six days later.
On October 17, the fix was included in version 0.9.1 and made available to the public.
Speaking to The Daily Swig, co-CEO of Shielder Abdel Adim said the likely scenarios using the attack chain would involve software developers and their IDEs.
“The average victim would be a software developer who opens an XML file in her IDE and the attacker gains control over her computer,” Adim commented.
“Development nowadays involves a lot of third-party code and XMLs are almost everywhere, so it’s common for a developer to open an XML file coming from an untrusted source.”
YOU MIGHT ALSO LIKE Shhgit hits the fan: Watch users leak secrets in real-time






