Charges against China over Equifax; the Swiss break their neutrality; and the hackers that continue to shape cybersecurity

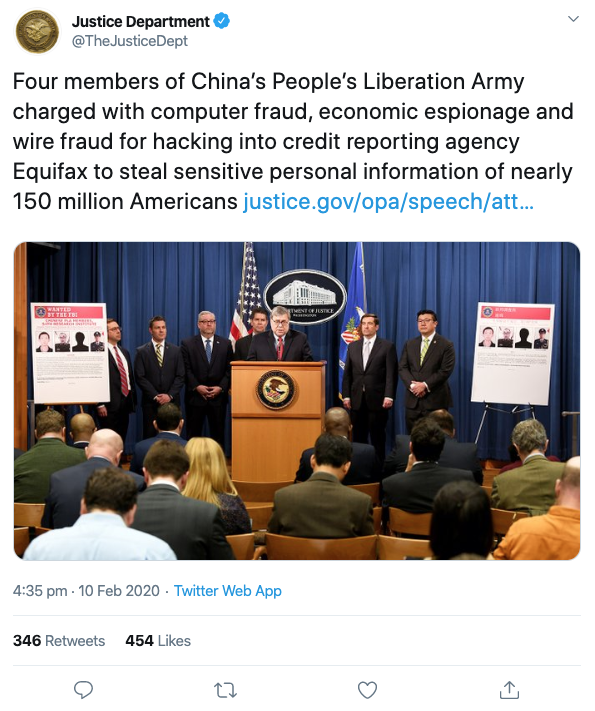
US prosecutors dropped a legal bombshell this week (Feb 10) with charges against four members of the Chinese military over the 2017 Equifax hack.
The accusations – strenuously denied by the Chinese authorities – calls into question the widely held assumption that one of the most high-profile data breaches in history was the work of profit-motivated cybercriminals.
Personal information of around 145 million Americans, along with the records of a much smaller number of British and Canadian citizens, were exposed by the attack against the credit reference agency.
Attackers were able to take advantage of Equifax’s failure to apply a March 2017 security patch to Apache Struts, the open source web application framework, to break into the company’s systems through its vulnerable dispute portal, The Daily Swig reported.
This compromised access was used to selectively siphon off data between May and July 2017, when the breach was uncovered. Equifax disclosed the breach in September of that year.
The four accused by the DoJ are members of the PLA’s 54th Research Institute, a component of the Chinese military.
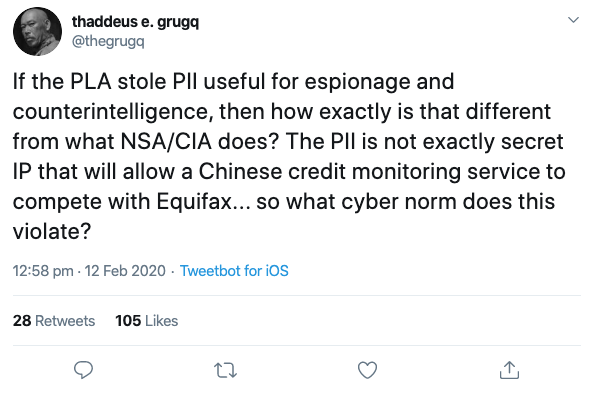
Infosec Twitter was abuzz with reaction to the charges, with some arguing that China’s alleged actions would be better categorised as cyber-espionage rather than criminal malfeasance.
News also broke this week that Swiss firm Crypto AG, a supplier of electro-mechanical encryption devices to scores of governments worldwide, was jointly corrupted by the CIA and the German Federal Intelligence Service (BND).
This control gave Western spies backdoor access to the secret communications of Iran, India, and Italy, among others, through an operation codenamed ‘Thesaurus’ and later ‘Rubicon’, according to an investigation by The Washington Post.
The reports confirmed long held suspicions that Crypto AG’s devices were rigged. Earlier rumours were fueled by US justifications for bombing Libya in the 1980s that it had irrefutable evidence through interception of diplomatic communications that the Arab country had bombed a disco in West Berlin back in 1986, among other incidents.
Neither Russia nor China ever trusted Crypto AG devices, the BBC reports.
The legacy of Crypto AG was taken by some as a rationale for why the US is so much more fearful than its European allies about backdoors in the 5G equipment supplied by market leader Huawei.
Other experts were quick to suggest that cooperation between Crypto AG and the NSA has been an open secret since 1995, after the Baltimore Sun broke news of the covert arrangement.
On a more positive front, PortSwigger’s own James Kettle was recognized this week for his many contributions to web security with a place on a list of the Top 20 ‘Hackers’ Who Helped Shape the Cybersecurity Landscape Forever published by Forbes.
Kettle was recognized alongside ATM and medical device hack pioneer Barnaby Jack, likely Russian military intelligence front Guccifer 2.0, and the “entire ethical hacker community”, among other entries. Nominations were made by individual figures in the cybersecurity community.
The list generated a fair amount of comment on infosec Twitter with some noting the lack of diversity in the Top 20, which features only one woman.
Finally, an important root certificate signing ceremony had to be postponed this week.
The delay was necessary because the Internet Assigned Numbers Authority (IANA) couldn’t open a physical safe containing hardware security modules at the center of a regular digital key signing process, The Register reports.
Every three months a group of trusted cybersecurity engineers meet up at one of two US-based secure facilities to cryptographically sign the digital key pairs used to secure the internet’s root zone, the system that underpins the security of Domain Name System (DNS) lookups.
Without the hardware modules the process can't be completed. Hence the delay, and call out to a locksmith in Los Angeles.