Critical Windows 10 flaw brings NSA out of the shadows; Magecart his Australia bushfire donation site; and a phisher gets well and truly phished

When the usually secretive US National Security Agency (NSA) publicly discloses a vulnerability – and the vendor sends a patch to government agencies before general release – then something unusual is surely afoot.
This “exceptionally rare, if not unprecedented” move – the words of Tenable CEO Amit Yoran – was prompted by discovery of a spoofing flaw in the crypt32.dll module of Windows 10, which handles certificate and cryptographic messaging functions in the CryptoAPI.
Microsoft’s first Patch Tuesday of the new decade was suitably seismic, The Daily Swig reported – fixing a bug that could be abused to disguise malicious code as trustworthy, or to mount man-in-the-middle attacks. Even HTTPS connections were vulnerable.
OS dominance gives Microsoft an Edge
A busy week for Microsoft also saw support ended for Windows 7 and the launch of a revamped version of its Microsoft Edge web browse based on Chromium.
If the re-fitted browser can come close to matching Google Chrome’s performance – and both are built on Google’s open source Chromium code – then Microsoft could reap dividends from its OS dominance since Edge will be bundled with all new Windows PCs – to the dismay of Mozilla Firefox fans.
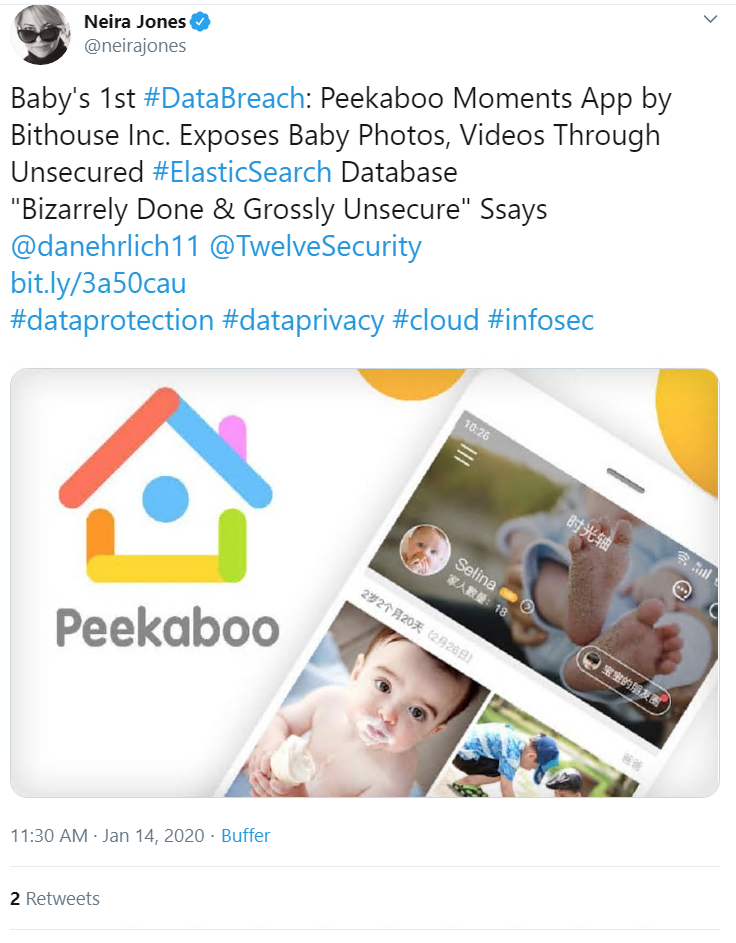
Baby’s first data breach
A mobile app that records “baby’s every precious moment” has deposited an unsecured Elasticsearch database of images, videos, email addresses, and detailed device data on Alibaba Cloud-hosted servers, it was revealed this week.
“I’ve never seen a server so blatantly open,” Twelve Security architect Dan Ehrlich, who discovered the exposed Peekaboo Moments database, told BankInfo Security.
“Everything about the server, the company’s website and the iOS/Android app was both bizarrely done and grossly insecure.”
The app’s Google Play page, incidentally, says “data privacy and security come as our priority” and that data “will be stored in [a] secured space.”
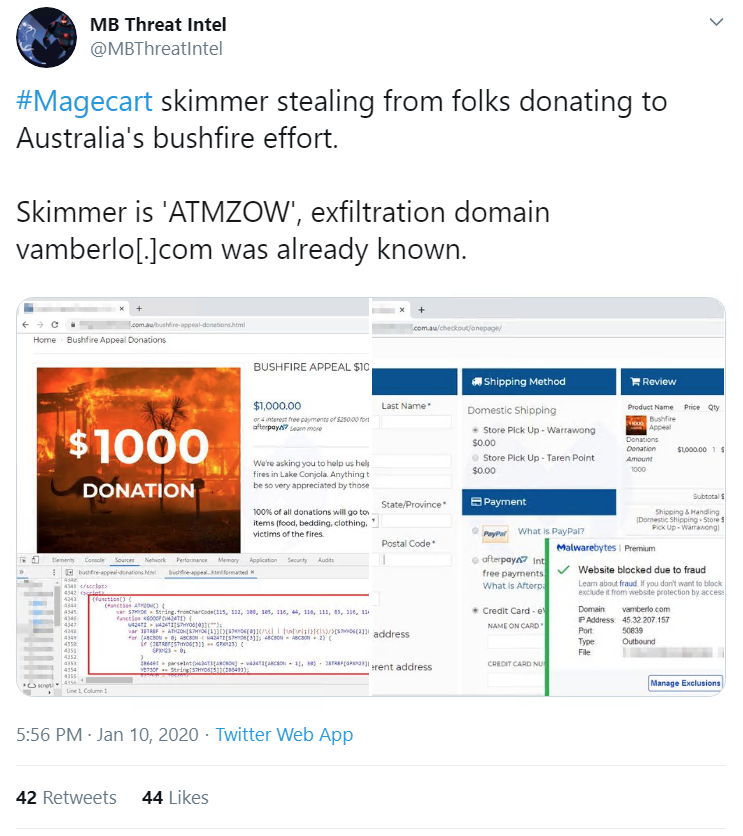
Magecart hits Bushfire donations site
Magecart – the JavaScript-based credit card skimming code – has struck again, this time compromising a website collecting donations for victims of the bushfires engulfing Australia.
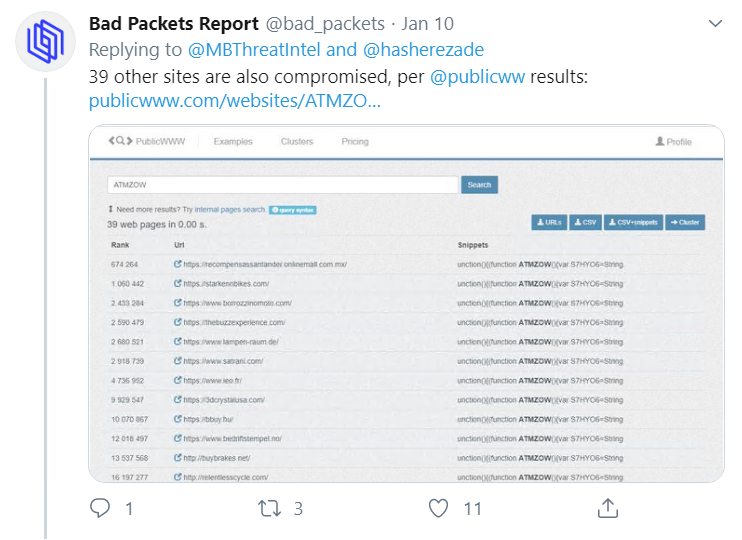
The Malwarebytes Threat Intelligence Team discovered that the cybercrime syndicate had injected the site’s checkout area with a malicious script – the unpronounceable ATMZOW – which stole and relayed payment information to vamberlo.com.
Malwarebytes’ director of threat intelligence, Jérôme Segura, told BleepingComputer that they’d succeeded in getting the malicious drop site shut down but that the script still lurked within the donation site’s code, ready for later modification, reactivation, and redirection to another domain.
The Daily Swig recently reported on techniques for detecting when websites are infected with Magecart-style malware, which was also the subject of our most recent SwigCast.
Potentially pwnd porn stars
Another unlocked treasure trove of data discovered by researchers might have left porn stars at risk of ID theft and extortion.
The vpnMentor researchers who discovered the open folder on PussyCash's Amazon web server, told BBC News that 875,000 files, relating to around 4,000 individuals, included everything from names, addresses and social security numbers to photos, videos and body measurements, scars, and tattoos.
The live webcam porn network said that it had now secured the folder, adding that it had failed to uncover any evidence that the data had been accessed by unauthorized parties.
Spyware gagging order
In privacy news, on Thursday an Israeli court granted a gagging order requested by the country’s Ministry of Defense in a case concerning the export of phone-hacking software created by NSO Group, an Israeli tech company.
Amnesty International, which filed the case after claiming Pegasus spyware was used to spy on its officials, wants the NSO Group’s export licence revoked to prevent its product from being used by repressive regimes to snoop on dissidents and journalists.
Pegasus, which has been described by researchers as the most sophisticated ever seen on any endpoint, is also subject to a lawsuit brought by WhatsApp.
The chat app has also accused the NSO Group of helping government spies breach the phones of 1,400 WhatsApp users across four continents, including activists and journalists.
NSO Group insists Pegasus is a legitimate and vital surveillance tool in the fight against terror and organized crime.
Phishing the phisher
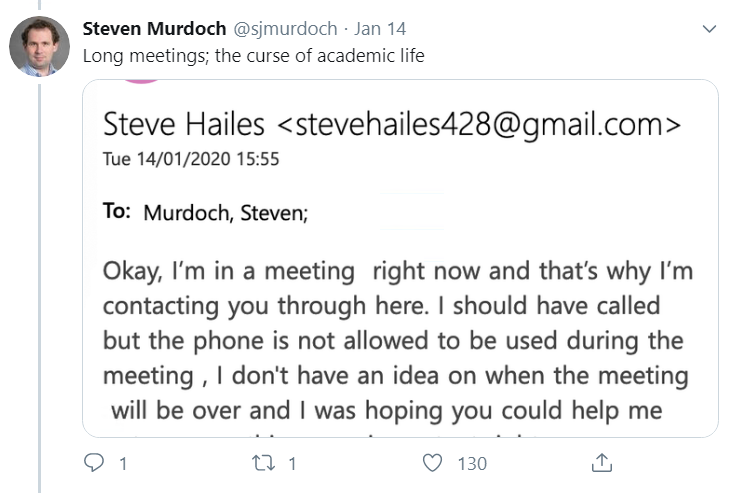
Infosec experts are naturally suboptimal targets for scams, as demonstrated in an email exchange with a con artist, which was documented on Twitter by Dr. Steven Murdoch of University College London’s (UCL) computer science department.
Affecting puzzlement that his department head was emailing him from a Gmail address, Murdoch proceeded to waste the scammers’ time, as well as getting the email addresses they were using banned by Google.
Many hallmarks of the standard email scam were present: poor grammar and tugs on the heart strings (“it’s one of my best friend birthday and going through cancer”) as well as, of course, requests for cash or, in this case, vouchers.
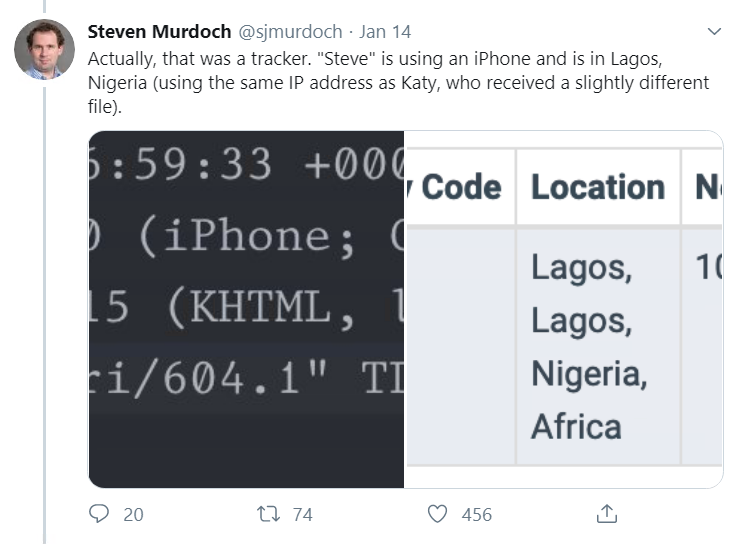
Murdoch sent ‘Steve’ and his afflicted friend, ‘Katy’, a tracking file that traced the pair to an IP address in Lagos, Nigeria, as well as a fake Amazon voucher whose code failed to work – much to the frustration of the scammer.
‘We are all in this together’
In other feel good infosec community news, security consultant Bob Diachenko tweeted a letter he had received from automotive giant Daimler thanking him fulsomely for his vulnerability disclosure work.
That this post drew such attention, however, must attest to it being something of an outlier.
“The literal opposite of a legal threat. how very rare,” riffed one Twitter user.