Western governments tell Facebook to forgo encryption; a new data sharing treaty is signed; and another data breach impacts millions

The battle for encryption reared its ugly head yet again this week, as high-ranking officials from the UK, US, and Australia called on Facebook to put the brakes on its previously announced plans to implement end-to-end (E2E) encryption across its services.
Concerns that the use of E2E on Facebook Messenger, Instagram, and WhatsApp would hinder public safety and the investigations of law enforcement was expressed in an open letter, first obtained by BuzzFeed News.
“Risks to public safety from Facebook’s proposals are exacerbated in the context of a single platform that would combine inaccessible messaging services with open profiles, providing unique routes for prospective offenders to identify and groom our children,” the letter reads.
Facebook responded with a short statement reiterating that it opposed building what would effectively be backdoors into its services for government access, The Guardian reported.
The news has reignited debates on encryption, digital safety, and privacy at a time where the world is ever more connected – an all too familiar dance, known in infosec circles as the ‘Crypto War’.
Others think it's outright shameful to force consumers to choose between two crucial pillars of human existence: privacy and security.
The battle continues.
In other tech policy news this week, Britain has signed an agreement with the US to allow data transfer between the two nations under a somewhat controversial treaty called the Cloud Act.
Having passed silently last year, the Cloud Act, or the Clarifying Lawful Overseas Use of Data Act, has marked a significant cornerstone in the fight for access to digital evidence and electronic communications by law enforcement internationally.
The bill, which was created, in part, on the back of an overseas drug trafficking investigation, is aimed at streamlining the process in which government agencies can request access to data held by a US tech company – such as Microsoft, Google, Apple, Facebook, or Oath – no matter where the data in question is stored.
In a statement published on Thursday by the US Department of Justice, Attorney General William Barr said: “This agreement will enhance the ability of the United States and the United Kingdom to fight serious crime – including terrorism, transnational organized crime, and child exploitation – by allowing more efficient and effective access to data needed for quick-moving investigations.
“Only by addressing the problem of timely access to electronic evidence of crime committed in one country that is stored in another, can we hope to keep pace with twenty-first century threats. This agreement will make the citizens of both countries safer, while at the same time assuring robust protections for privacy and civil liberties.”
The Cloud Act has been largely well received by American tech companies, with many welcoming the modernization of the international warrant process and use of such legislation to pre-empt any backdoor requests made by governments.
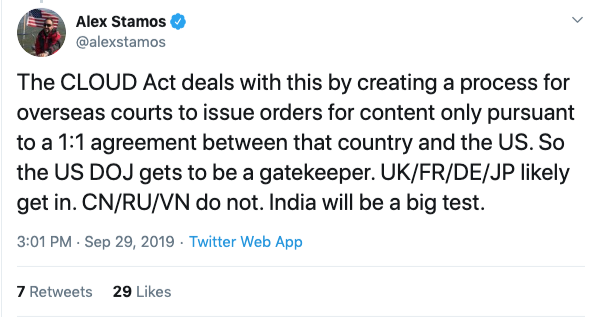
A thread on Twitter from computer scientist and Stanford lecturer Alex Stamos debunks the backdoor concerns and explains more about what the legislation will mean in practice.
And in other news, more than 200 million individuals discovered that their personal information had been exposed in a massive data breach.
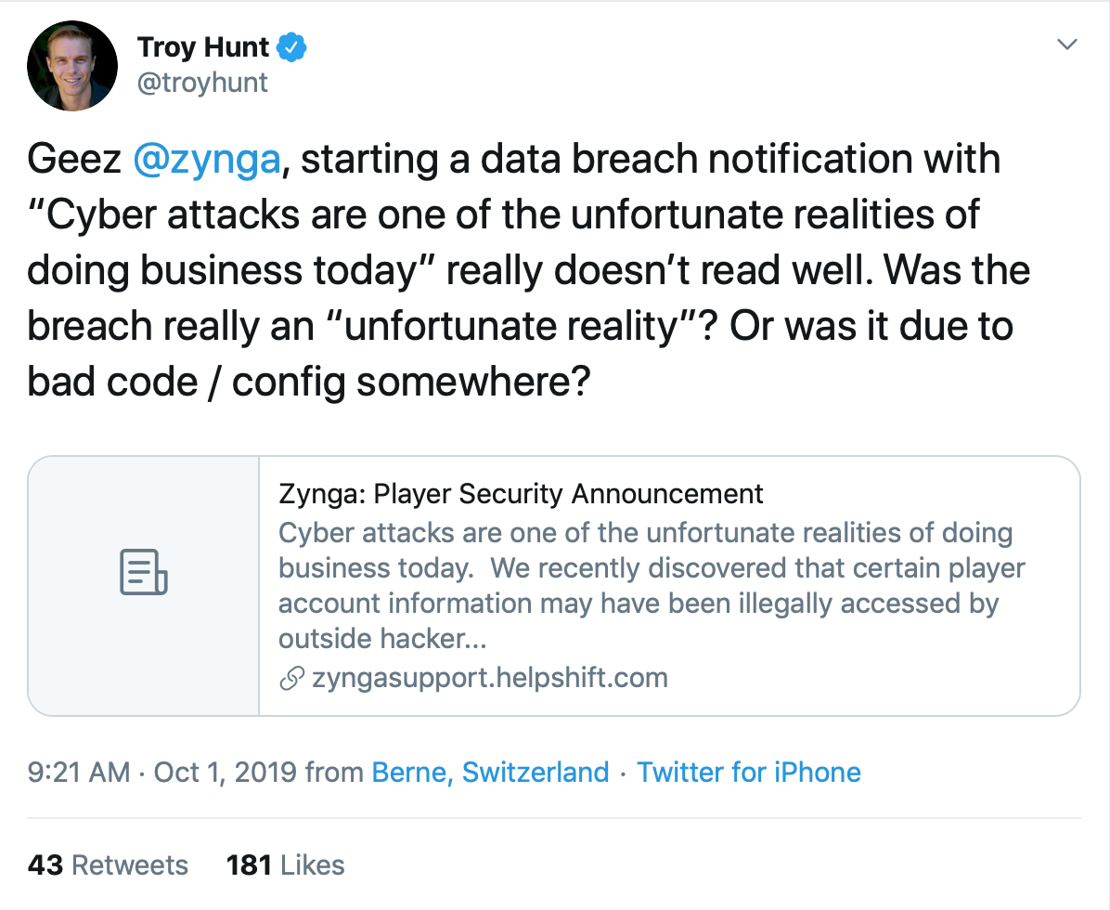
Zynga, the developer behind popular puzzle game ‘Words With Friends’, announced that it had experienced a data breach impacting 218 million users’ names, email addresses, phone numbers, and other credentials.
We weren’t impressed when we found out.
While having occurred back in September, the infamous cybercriminal Gnosticplayers – the alleged culprit of other data security incidents – told Hacker News on Tuesday that it was responsible for the breach at Zynga.
The security incident impacted both Android and iOS users of the popular word-building game.
And finally; if you’re looking for some weekend reading to kick off the National Cybersecurity Awareness Month, check out this Medium post by offensive security engineer Adam Toscher, ‘A Red Team Guide for a Hardware Penetration Test’.