Top infosec trends in the social media spotlight this week

UPDATED Black Friday is here again, with shoppers across the world battling it out to get their hands on bargains before the Christmas season kicks in.
This morning, the usual chaos ensued – crowds rushing into Walmart for cut-price TVs and the very real possibility of a punch up over a pair of Beats headphones.
If you’re shopping online today, make sure you protect yourself against hackers looking to cash in on the sales.
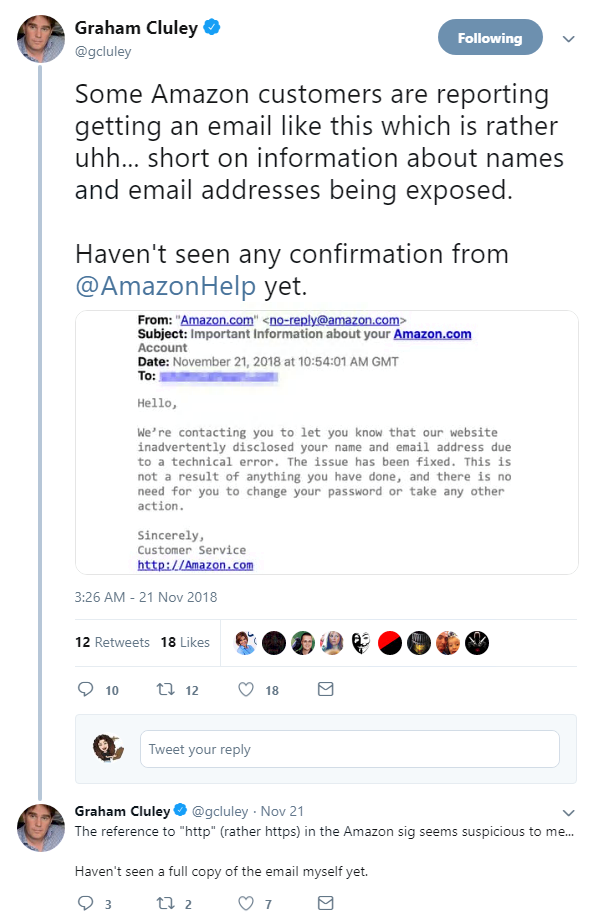
And if you’re an Amazon customer, you might be one of the unlucky few to have had their details disclosed by a ‘technical error’ this week.
Amazon, one of the largest Black Friday retailers online, exposed the details of some customers just days before its annual discounts launch.
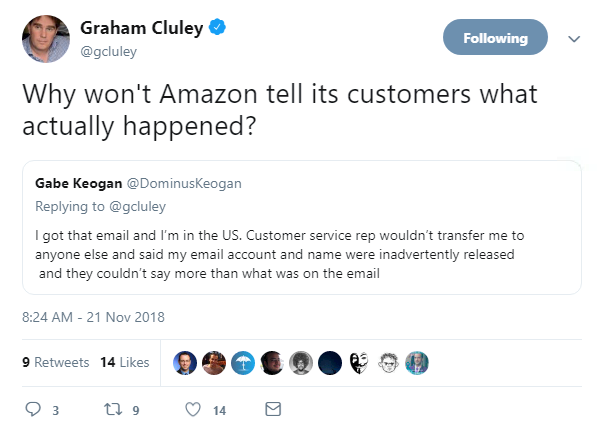
In an email to those affected, the company admitted it had disclosed the names and email addresses of an unknown number of customers.
It also linked to a http (rather than a https) address, leading some to question whether it was a phishing email.
The incident turned out not to be a breach of Amazon’s website or systems, but was due to an error which has now been fixed.
An Amazon spokesperson told The Daily Swig: “We have fixed the issue and informed customers who may have been impacted.”
In other Black Friday-related news, US delivery service USPS reported a vulnerability in its site which allowed account holders to view the data of its 60 million users, and in some instances modify their accounts.
The incident stemmed from an authentication weakness in the USPS website’s API, according to security researcher Brian Krebs.
It led to the exposure of near real-time data concerning packages sent by USPS as well as personal data such as names, email addresses, phone numbers, and deliver addresses.
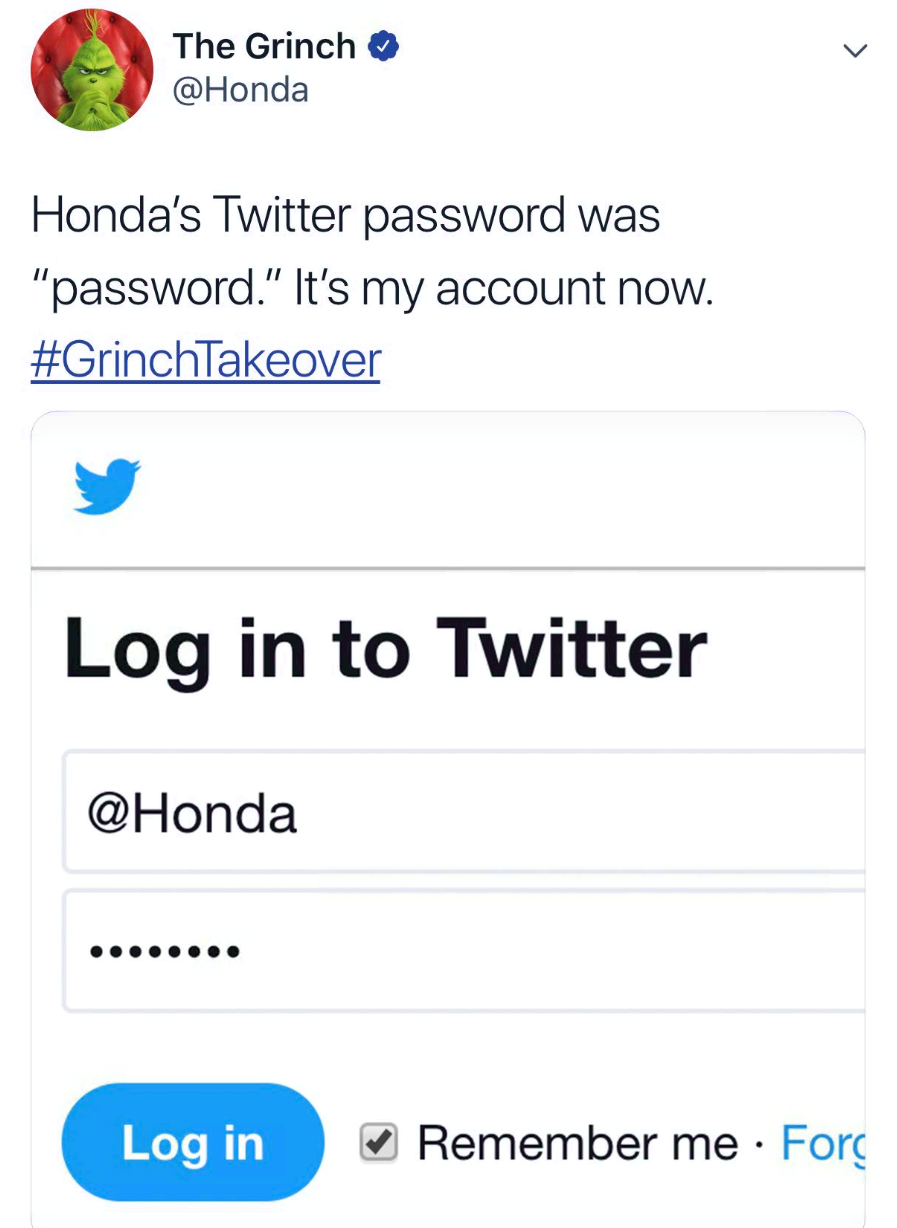
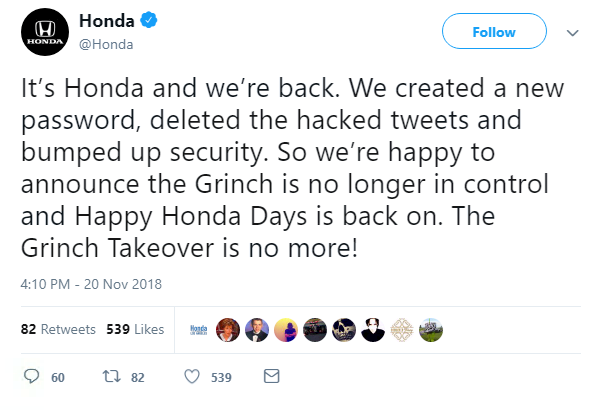
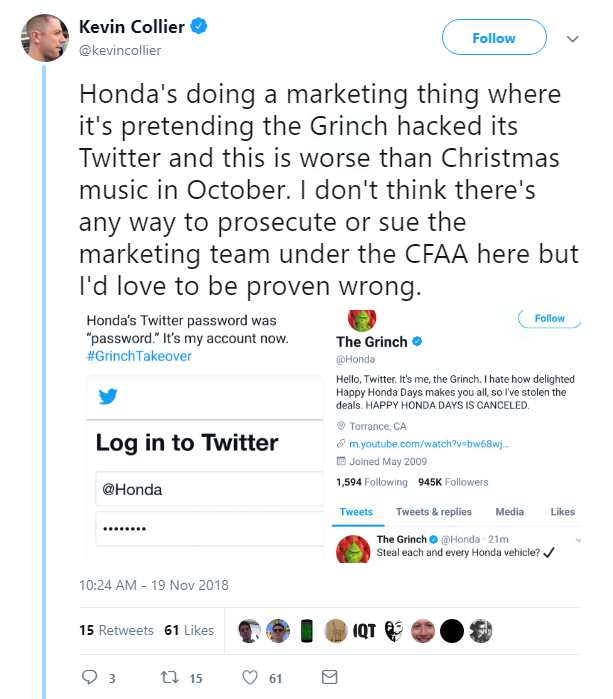
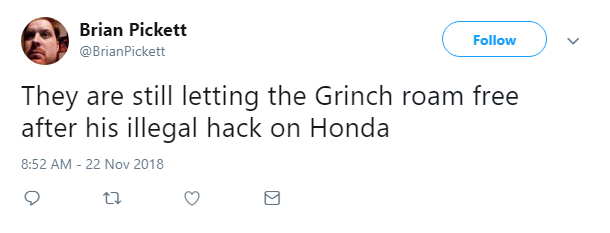
Honda tried to fool Twitter into thinking it had been hacked this week – but it soon became clear the pwnage by a ‘troll’ was actually a marketing stunt.The car manufacturer’s account was temporarily overtaken by Christmas character The Grinch.
Many of the tweets were an obvious promotion of the company’s ‘Happy Honda Days’ campaign, but Honda played along with the so-called hack.
Which also led to some mocking…
It’s not quite clear whether the Honda PR team were inspired by the slew of fake Elon Musks taking over popular accounts to scam users into buying handed over cryptocurrency for non-existent rewards.
Either way, the clever campaign divided Twitter users. Some loved it, some hated it…
… and others were questioning whether Honda could be prosecuted under the Computer Fraud and Abuse Act.
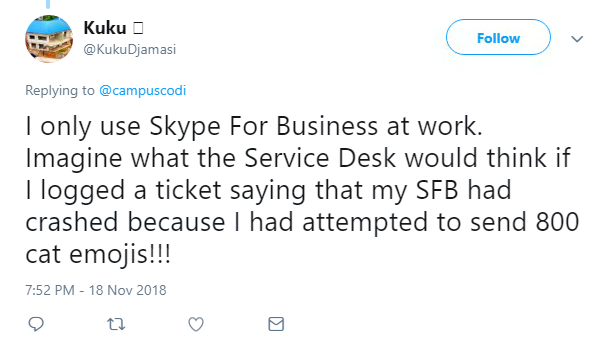
A vulnerability in the Skype for Business instant messenger service allowed a denial of service attack to be launched after flooding the chat window with cat emojis.
When a large number of emojis were sent via the platform, for example 800 kittens, it caused the program to freeze for a few seconds.
This could then be exploited to perform DoS attacks against Skype for Business users.
The flaw (CVE-2018-8546) was accompanied by a proof of concept detailing how it was proven using hundreds of cat emojis.
Finally, two long-reads surfaced online this week which give an interesting insight into the work of pentesters.
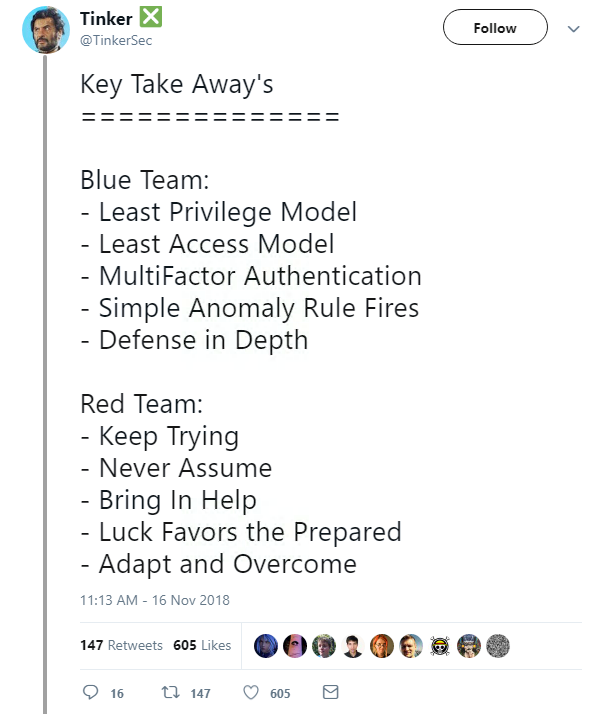
First up, @TinkerSec detailed the difficulties of carrying out an insider threat against an unnamed company, after he posed as ‘Jeremy from Marketing’ for a week to try and gain access.
He eventually failed, but not for lack of trying. The week-long attempt involved multiple attempts, including ‘borrowing’ 30 end-of-life laptops from the IT department’s office and being caught by ‘mean’ staff.
You can read all about it here.
Dropbox also offered insights into its security mindset, with a blog post about how it protects its networks.
In the post, Dropbox detailed how it uses pentesting to find flaws, both in-house and through third-party partners such as Syndis.
The company also released details of three vulnerabilities found by Syndis, which could be used in a chain exploit to allow remote code execution (RCE).
After downloading Dropbox as an Apple disk image (.dmg), these bugs – (CVE-2017-13890), (CVE-2018-4176), and (CVE-2018-4175) – could be exploited to hack into vulnerable systems.
The post read: “Our third-party partner, Syndis, found vulnerabilities in Apple software we use at Dropbox that didn’t just affect our macOS fleet, it affected all Safari users running the latest version at the time — a so-called zero-day vulnerability).
“When chained together, these vulnerabilities resulted in the ability for an attacker to run arbitrary code on a victim’s computer by having the victim simply visit a maliciously crafted web page.
“We notified Apple of these issues, and they were quick to acknowledge our report. Apple released fixes for the issues in about a month, which is much better than the industry norm of ‘within 90 days’.”
This article has been updated to include comment from Amazon.