Have I Been Pwned founder’s keynote offered a sobering counterpoint to the well-meaning ‘World Password Day’

Imagine a parent’s terror when the geolocation of their child’s smart watch suddenly switches from tennis practice to the middle of the ocean.
This was precisely the scenario simulated by Ken Munro of UK infosec firm Pen Test Partners via exploitation of an insecure direct object reference (IDOR) vulnerability in an IoT device, and with help from Troy Hunt, creator of data breach record index Have I Been Pwned, and his daughter.
This was one of many eye-opening tales of shoddy security behind the “endless flow of data” into Have I Been Pwned recounted today (May 6) during Hunt’s keynote address at the all-virtual Black Hat Asia 2021.
Another API flaw in the TicTocTrack kids watch meant Munro’s colleague, Vangelis Stykas, successfully compromised another user's account and initiated a voice call through the device with zero interaction required from the wearer.
Logged into his own account, Munro also compromised other ‘family’ accounts by simply changing an identifier parameter. A subsequent security patch created an even more egregious regression bug.
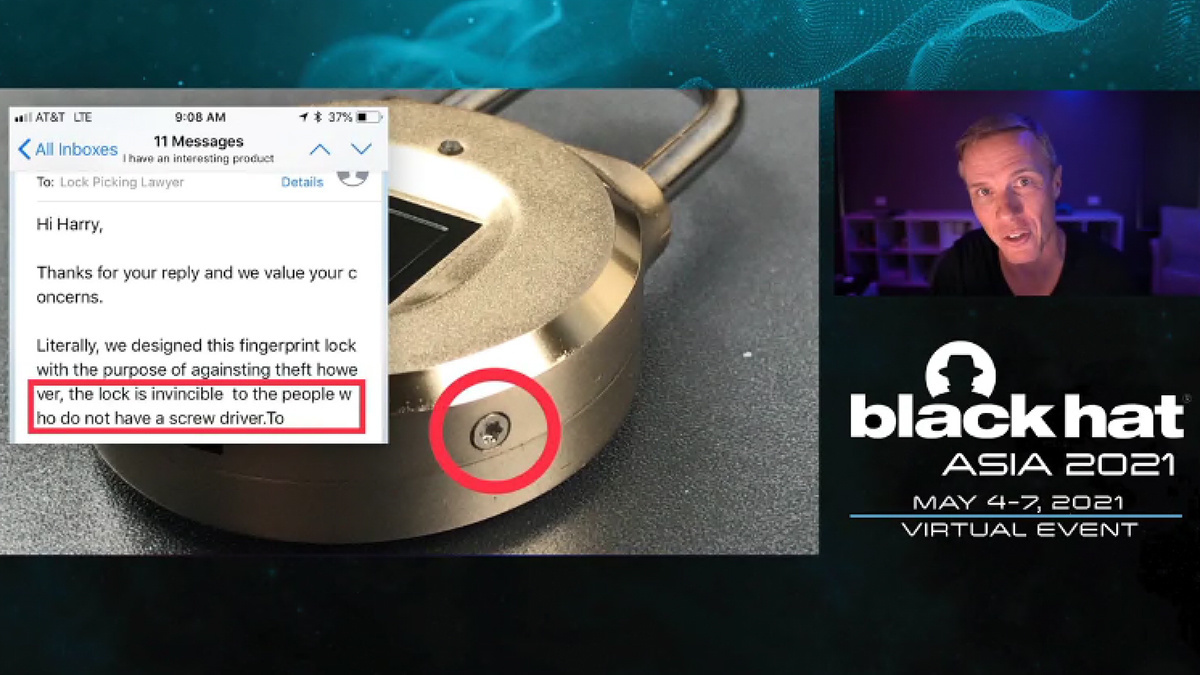
Hunt also cited a purely physical intrusion that nevertheless “perfectly illustrates” his digital insecurity theme.
Having notified the vendor that he had dismantled their $47.99 biometric lock, a popular YouTube lock-picker was told the contraption was “invincible to people who do not have a screwdriver”.
Phishy email marketing
During his keynote, Hunt noted that even supposedly security-conscious organizations are “making it very difficult for people to make good security decisions”.
The infosec pro cited a ‘phishy’ email he received from Australia’s ANZ Bank featuring a suspicious, HTTP URL that redirected to another suspicious URL: ‘c00.adobe.com’.
The email turned out to be a genuine ANZ communication.
“Over and over again”, lamented Hunt, we see “legitimate organizations sending legitimate communications that are indistinguishable from phishing attacks”.
 Australian infosec pro Troy Hunt delivered the Black Hat Asia 2021 keynote
Australian infosec pro Troy Hunt delivered the Black Hat Asia 2021 keynote
Publicly accessible databases
Founded in 2013, Have I Been Pwned has now indexed more than 11 billion records of personal data harvested not just from compromised websites but also publicly accessible databases.
The service was recently updated to include phone numbers from the explosive Facebook mega-breach and data courtesy of the recent takedown of the Emotet botnet.
While most would consider 11 billion breached datapoints to be nothing more than a demoralizing milestone, this seemingly never-ending avalanche of security incidents has served to give Hunt powerful insight into the underlying causes of data breaches.
Read more of the latest security research news from around the world
In 2016, for example, Hunt was alerted by a purportedly good-faith hacker to one such database, inadvertently exposed by the Australian Red Cross Blood Service, comprising personal data belonging to 550,000 blood donors.
Scorning the notion that minimizing your ‘digital footprint’ is remotely practical, Hunt pointed out that he was among those victims having submitted his details with a pen and paper.
“The fruit is [often] so low hanging” for attackers, he said, that a 17-year-old hacker (not, after all, the purported “Russian Islamic cyber Jihadis”) was able to cause the TalkTalk data breach that cost the UK telco £77 million ($107 million).
The unfathomable volumes of data harvested during such compromises was appearing in enormous credential stuffing lists posted not just on dark web markets, but on Twitter too.
The problem with password complexity criteria
The doyen of data breach research also charted the painful evolution of password security over the decades.
In the 1980s, Hunt said, around 90,000 UK homes were given access to a ‘Prestel’ system, through which user’s could dial into a central location and authenticate to a server.
However, a pair of good-faith hackers found that administrative accounts had the password ‘1234’, a discovery that led to their prosecution and eventual acquittal, and the UK’s first – and current – computer crime law.
Fast forward to the noughties and the introduction of password complexity criteria.
Stringent rules – mandating periodic password updates with minimum lengths and comprising lower case, upper case, numerical, and non-alphanumerical characters – foundered on the fact “that humans are not automated random number generators with password managers in their heads”.
Faced with ever-growing friction, “people follow very predictable patterns and take shortcuts to memorizing the password”, such as using post-it notes and numerically incrementing ‘MySafeP@ssw0rd1!’ to ‘MySafeP@ssw0rd2!’ and so on with every 90-day prompt, said Hunt.
Belatedly, the industry is changing tack with multi-factor authentication and user-behavior analytics offering alternative, lower friction solutions, he concluded.
YOU MIGHT ALSO LIKE Passwordstate credentials potentially ‘harvested’ after malicious software update injected into password manager






