The Offensive Security CEO discusses a busy first 12 months at the helm of Kali maintainer and pen test certifications giant

If offense is the best defense, then penetration tests are the ultimate indicator of an organization’s security posture.
And as companies around the world look to bolster their cyber resilience by proactively asking security pros to test their systems for vulnerabilities, this has underscored the need for companies like Offensive Security.
Founded in 2006, Offensive Security offers a range of ethical hacking certification courses, while also funding and maintaining Kali Linux, the popular Debian-based Linux distribution designed for digital forensics and pen testers.
The Daily Swig caught up with Ning Wang, Offensive Security’s CEO since January 2019, to find out about her eventful first year at the helm.
Wang, who has a physics PhD and joined the company from bug bounty platform HackerOne, also discusses the recent update to Kali Linux, countering improvements in defensive tools, and dispelling myths around what it means to be a ‘hacker’.
 Offensive Security CEO, Ning Wang
Offensive Security CEO, Ning Wang
How has your first year as CEO of Offensive Security gone?
Ning Wang: I am humbled and touched by the journey our company has taken over the past year.
Our staff grew more than 50%, and we trained more infosec and IT professionals, and granted more certifications, than any other year. Over 60% of Fortune 100 companies now employ Offensive Security-trained professionals.
I’ve heard from more and more CISOs and security leaders that they now use Offensive Security certification as a baseline standard. They are rewarding their teams by offering our training and certification as a benefit.
More individuals than ever recognize the advantage the Offensive Security ‘try harder’ mindset gives them in their careers.
We’re very focused on fulfilling the demand by making more courses and content available for students, and providing more flexible ways for organizations to invest in training.
As an example, we just launched a major update to our flagship ‘Penetration Testing with Kali Linux (PWK)’ training product, which includes a [doubling of] curriculum content and an overhauled and expanded virtual lab. Students who pass the final exam receive the Offensive Security Certified Professional (OSCP) certification.
In March 2019, we made one of the industry’s most in-demand live training courses, Advanced Web Attacks and Exploitation (AWAE), generally available online. Students who pass the AWAE final exam receive the Offensive Security Web Expert (OSWE) certification.
Also last year, we introduced OffSec Flex, a new program for enterprises to purchase blocks of Offensive Security’s training, certification, and virtual lab offerings in order to proactively offer training and educational opportunities to new hires and non-security team members alike.
Has your three-year stint as HackerOne’s COO and CFO helped you in your latest role?
NW: My time at HackerOne helped ensure that I truly understand the dynamics, mindset, and needs of the ethical hacker community and the kind of skills development they need to succeed.
HackerOne – and Eucalyptus Software prior to that – also provided invaluable experience in building and maintaining a passionate open source community.
You recently launched a major update to Kali Linux. What are the most notable improvements, and how has the launch been received by the Kali community?
NW:
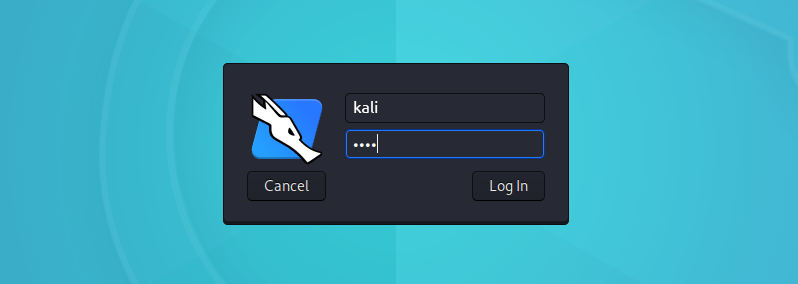
The latest update changes the default ‘root/toor’ credentials to ‘kali/kali’ – a big change as root has been the default since its inception.
After auditing the images that are downloaded most [frequently], we completely restructured and simplified the images that will be released going forward.
There is now an installer image, a live image, and a network installer image, allowing for easier selection of the right image for each user while also increasing flexibility. There will no longer be separate images for every desktop environment.
Kali’s mobile pen-testing platform, Kali NetHunter, will no longer require users to root their phone in order to run it.
While Kali is a rolling distribution and therefore users don’t need to wait for the next release for updates, the team has added several new tools since Kali 2019.4, including ‘cloud-enum’, ‘emailharvester’, ‘phpggc’, ‘sherlock’, and ‘splinter’.
The last several releases have been very well received by the community. We are in the middle of a really exciting stage of the Kali development process, where a lot of behind-the-scenes items have been going public, with more on the way.
What factors influence the Kali platform’s development? Do you keep an eye on what other major Linux distributions are doing?
NW: In the end, we make Kali for us. We do training, penetration tests, security research, and so on. All the standard use cases that others use Kali for, we do internally.
So you could say we are our own focus group. Of course, there is community feedback, requests, and so on – and we listen to them – but we also think that there is often a difference between what people want and what they need.
As for other Linux distributions, they are often targets in our assessment work, but we are a focused niche, and what happens in a general purpose operating system often has little bearing on what we decide to do with Kali.
How important are security certifications when it comes to progressing a career in infosec?
NW: In an age when software is in everything we touch and use, it’s now a matter of when, not if, it will be breached, because adversaries are organized and talented.
For companies to best defend themselves, they need to work with well-trained security professionals with the same offensive skillset.
That said, the most successful security professionals possess not only technical skills, but also the proper mindset – the ‘try harder’ mindset.
We encourage students to be persistent and perceptive in the search for creative solutions. OffSec certificate holders have proven that they understand that hard work is part of the process. They know how and when to step back, see the big picture, and manage themselves and their time.
Our certifications are based on real-world, practical training, which makes infosec professionals better equipped to defend their organizations.

Infosec is a fast-moving field. Can you give me an example of how you’ve adapted your syllabus to a notable recent security trend?
NW: One of the biggest is the increasing capabilities of defenders’ toolsets. There has been a capabilities differential where attackers had better tools. Over the last few years, that has been shifting.
You have to give credit to the improvements Microsoft and other organizations have been making, the quality of real-time monitoring solutions, white-listing solutions, and so on.
Properly deployed, these defensive tools make the skill level required to successfully attack the targets without being detected much harder.
To keep up with these changes, we do a limited number of assessments per year in high security environments. We bring various staff members into these jobs to give them a chance to see what tools, tactics, and techniques are effective.
This becomes our R&D, and keeps everyone’s hands dirty. It’s critical that we don’t fall into the ‘ivory tower’ trap so many educational organizations fall into.
Kali Linux’s tweet in response to a poster from a UK police force urging parents to call them if they catch their children using Tor, Discord, or Metasploit, was applauded by the security community. How are you helping to change negative preconceptions of ‘hackers’?
NW: Our chief content and strategy officer, Jim O’Gorman, had a perfect response, which I think reflects Offensive Security’s viewpoint: whether it’s ‘hacking tools’, rock music, video games, and so on, these are terrific opportunities for parents to engage with their children, find common interests, and spend time together while helping the child learn skills that will help them later in life.
To help counter misconceptions of hackers, we started a student spotlight series on our blog, which shares stories about their journeys to OffSec certification.
One of my favorites is the story of Mihai, a 16-year-old OSCP holder from Romania who approached me personally for special permission to take our PWK course because the minimum age for an OffSec student is 18.
There are many inspiring takeaways [but] one thing stands out: don’t let age deter you from pursuing your passions.
[Another] one of Offensive Security’s goals is to make the cybersecurity industry more inclusive, with focuses on gender norms, age differences, and ethnic backgrounds.

Finally, what's on the agenda for the rest of 2020?
NW: We will continue to invest in our content: update some courses, and create new content, including labs-only products.
We plan to improve the learning experience and deepen our involvement with the community of active students.
RECOMMENDED Knowledge transfer: Casey Ellis on IoT bug bounties and live hacking events






