Top infosec trends in the social media spotlight this week

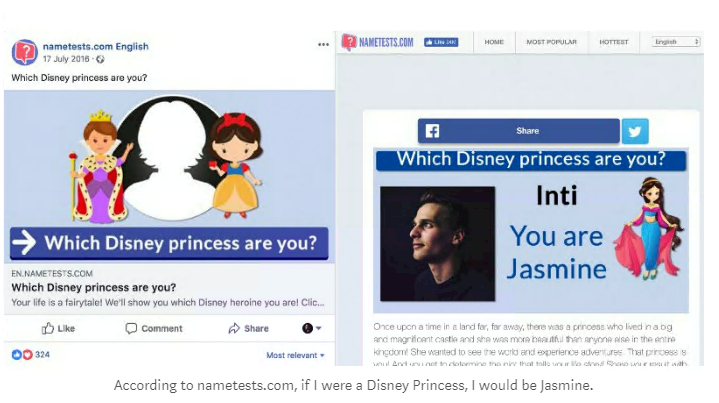
Just months after the Facebook/Cambridge Analytica scandal revealed social media users’ data was being scraped and sold to third parties, another personality quiz app has exposed the data of 120 million people.
Popular quiz app Nametests, developed by a company called Social Sweethearts, contained a vulnerability that allowed the data to be viewed by anyone.
This flaw was addressed via Facebook’s bug bounty program and was discovered by researcher Inti de Cuekelaire.
Cuekelaire, who described the issue in a blog post, said that a flaw in the JavaScript coding meant that the information of users who gave permissions to the app was available for any third-party to see.
This latest find is one of the first vulnerabilities made public by Facebook’s data abuse bug bounty program, which launched in the wake of the Cambridge Analytica case.
In other data privacy news, UK-based digital rights campaigners Open Rights Group has launched a tool for users to check what an organization does with their data.
The Data Rights Finder contains a list of companies, including PayPal and various British banks, and explains how each entity collects and shares an individual’s data.
It comes as greater pressure is being put on businesses to practice transparency, through legislation such as GDPR and other data misuse policies like Facebook’s recently expanded bug bounty scope.
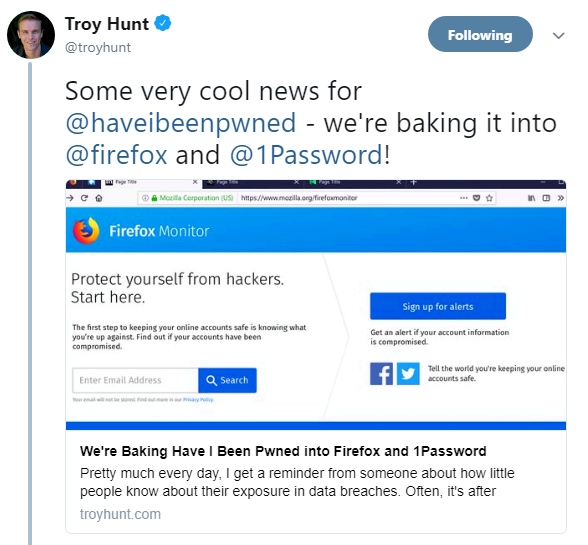
Popular web database Have I Been Pwned? was integrated into Mozilla Firefox and 1Password this week, offering users an easier way to check their OpSec.
The service, created by security researcher Troy Hunt, currently contains a list of 5.1 billion email addresses known to have been stolen in reported data breaches.
It has now been integrated into Firefox via a new tool called Firefox Monitor, which will allow users to keep a check on whether their email address has been lifted.
Password manager 1Password has also released a new tool which allows users to check whether they have been pwned by searching within the web-based version of the app.
The announcement was warmly welcomed by the security community, especially given the ever-increasing number of data breaches reported on week after week.
A researcher this week said that he had pwned Apple by discovering a brute force password hack – but backtracked when the company spat back at his claims.
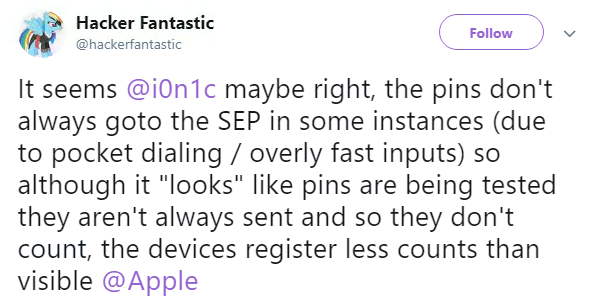
Matthew Hickey tweeted a video of an exploit he said can be used to bypass Apple’s Secure Enclave feature and guess the device’s password.
Secure Enclave unlocks the device when a correct passcode or biometric is given – and locks the device after a certain number of attempts.
Hickey claimed that when passing data through a Lightning cable, he was able to send every possible combination as one continuous number, meaning he was able to execute an infinite number of tries.
But when Apple came out to say the hack was down to incorrect testing, Hickey confirmed the test results were down to an error, and that the device was only counting limited passcode attempts, contrary to what he previously believed.
As you probably know, Apple is launching a new USB Restricted Mode to better protect its devices from password-hacking hardware – though the makers of the GrayKey cracking kit may have already found a workaround.
Finally, Experian embarrassed itself this week when it offered a ‘triple dark web scan’ to customers, promising advanced protection against malicious hackers.
The scanner, the company claims, can search records across the dark web and find any trace of a user’s personal details online.
But the idea was panned online by the infosec community, who had a good laugh about the impossibility of the overly-dramatized advert.
This video also features Trump’s lawyer Rudy Guiliani explaining how this software is supposed to work…