Affiliate-based ransomware model means malware architects are likely to remain at large
ANALYSIS Earlier this month, an alleged distributor of the infamous GandCrab ransomware was arrested in Belarus on charges of extorting more than 1,000 victims around the world.
The unnamed 31-year-old man is said to have distributed the file-encrypting malware between 2017 and 2018, demanding up to $1,500 in bitcoin for the return of victims’ data.
According to prosecutors, the man was an affiliate of the GandCrab cybercrime operation.
They allege he didn’t create the ransomware, but acted as a distributor who rented access to an admin panel and sent out customized malware campaigns in return for a cut of any ransom payments.
The arrest comes more than a year after GandCrab’s creators announced they were heading into retirement.
Since that time, another arguably more dangerous ransomware strain dubbed ‘REvil’ has come to the fore, with many alleging the two pieces of malware share the same architects.
While it’s often the case that one arrest can send cybercrime operations tumbling to the ground, experts have warned that, given the affiliate-based model of both GandCrab and REvil, the creators are likely to remain at large.
GandCrab declawed
GandCrab first surfaced in January 2018. The malware, which targets Microsoft Windows devices, encrypts victims’ files and demands payment in order for them to recover stolen data.
BitDefender estimates that the campaign targeted more than 1.5 million victims worldwide, while GandCrab operators themselves claimed to have made more than $2 billion in ransom payouts.
Little is known about the criminal gang behind GandCrab, however the ransomware’s code had specific language-based rulesets to ensure it would not infect machines in Russia and former Soviet Union countries, suggesting that the author could be from this area.
Multiple sources have supported this theory, including investigative reporter Brian Krebs who suggested that the author is of Russian origin.
Due to GrandCrab’s distribution model, however, identifying those behind the campaign is extremely difficult.
 GandCrab ransomware is thought to have infected more than 54,000 devices globally
GandCrab ransomware is thought to have infected more than 54,000 devices globally
GandCrab operated under what’s known as a Ransomware-as-a-Service (RaaS) model. This means that the authors sell access to the malware to clients, often via a customizable admin portal, who are then able to conduct their own cybercrime campaigns.
The campaign didn’t escape the attention of Europol’s No More Ransom project, which continued to develop decryption tools for each new-and-improved version of GandCrab.
In June 2019, after a 17-month-long reign of terror that’s thought to have resulted in more than 54,000 devices being infected around the world, the developers announced they were closing the operation for good.
REvil rises from the shadows
Months before GandCrab closed its doors, a new ransomware campaign was quickly gathering pace.
Dubbed ‘REvil’, or ‘Sodinokibi’, high-profile victims included the Travelex cyber-attack that took place on New Year’s Eve 2019.
The currency exchange was forced offline by hackers who demanded $6 million in return for the customer data being restored.
RELATED What is Sodinokibi? The ransomware behind the Travelex attack
REvil also crippled local governments throughout the state of Texas in August 2019. And later that month, the ransomware infected a remote data backup service used by dental practices across the US.
In December last year, a New York Airport was targeted by the ransomware, the same month that major US data center provider Cyrus One fell victim.
Data, apparently stolen from US IT staffing organization Artech Information Systems, was also published online in January 2020 after Sodinokibi/REvil attackers claimed it failed to pay the ransom.
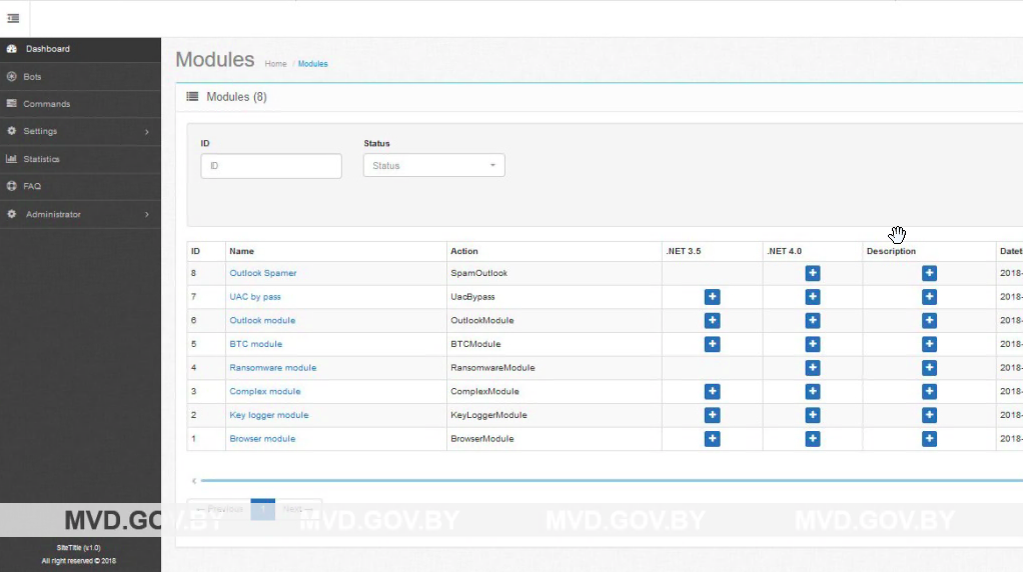 A screenshot of the GandCrab administrator dashboard used to conduct ransomware campaigns
A screenshot of the GandCrab administrator dashboard used to conduct ransomware campaigns
Risky businesses
After being scrutinized by security experts, it was discovered that GandCrab and REvil shared remarkable similarities in their source code.
The announcement that GandCrab was shutting down added fuel to the rumors that REvil was, in fact, a direct replacement to the ransomware strain that was attracting far too much undesirable attention from law enforcement.
But while the two pieces of ransomware certainly appear to be based on the same code, one expert has warned that it’s unlikely that this latest GandCrab arrest will have any material impact on the ongoing REvil campaign.
Tamas Boczan, a senior threat analyst at VMRay who has been tracking GandCrab and REvil/Sodinokibi since their inception, told The Daily Swig: “As far as we know, Sodinokibi operations are not affected by the recent arrest.”
“GandCrab was sold as ransomware-as-a-service, a popular business model which separates the developer of the malware from its affiliates who distribute the malware.
“Sodinokibi is the successor of GandCrab in a sense – we can confirm that it is very likely based on the same source code, and in late 2019 the Sodinokibi operators themselves claimed in a forum post that they purchased the GandCrab source code, after being its affiliates.
“Though the codebase is likely the same, Sodinokibi attackers mostly focus on targeted attacks, unlike GandCrab attackers, who usually attempted large-scale attacks during most of the malware’s lifetime.”
Crab phishing
While victims of GandCrab will no doubt welcome the arrest of an alleged culprit, only time will tell when – if ever – the source code masterminds will be put behind bars.
Unfortunately, no free decryptor tool is currently available to remedy Sodinokibi/REvil infections. But with phishing attacks being a principal vector, remaining alert to unsolicited emails is one form of defense.
For those who do fall victim to the malware, there are some steps you can take to reduce the impact across your network.
“The recommended remediation is to close the gap in defense so the malware doesn’t reinfect the system, then reinstall the infected machine and restore the files from backup if there is any,” suggests Boczan, adding: “Paying the ransom is usually not advised.”
Additional reporting by James Walker
READ MORE GandCrab closure will lead to power vacuum in ransomware market






