Google’s Password Checkup add-on raises privacy hackles

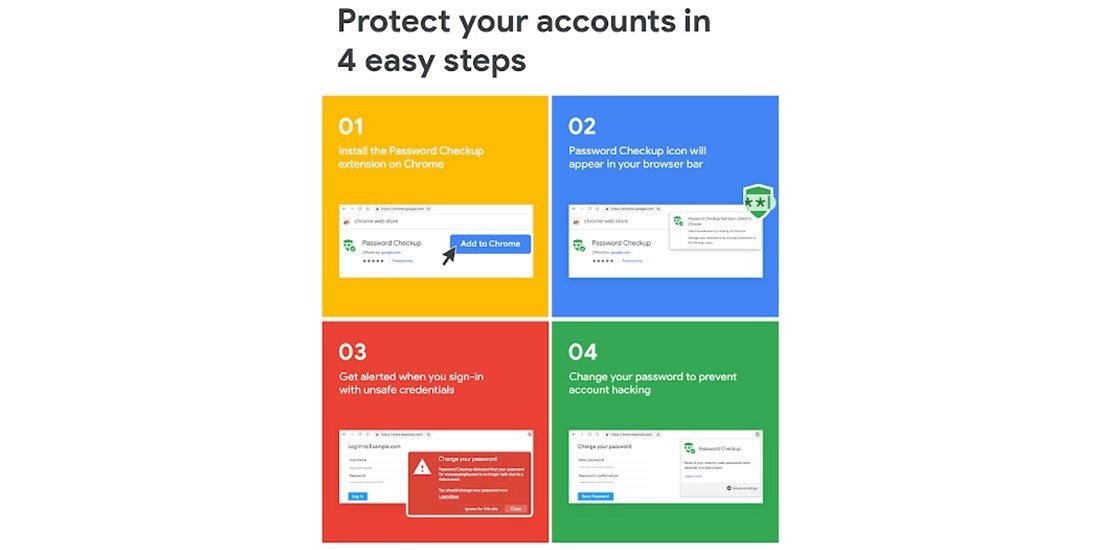
Google has released a browser extension designed to alert users if they are using passwords that have been compromised.
Password Checkup, released for Chrome as an early beta on Tuesday, checks a user’s password against a database of four billion stolen credentials and triggers a warning if it has been compromised.
This technology is designed to help consumers to identify and re-secure accounts affected by data breaches before their at-risk accounts are abused.
The alerts will focus on actionable warnings about unsafe usernames and passwords, rather than flagging up instances where phone numbers or mailing addresses have been exposed.
Warnings will trigger only when both a user’s current username and password appear in a breach.
The extension won’t flag up weak passwords, such as “password” or “123456”, or in cases where a user’s outdated passwords, which have since been reset, were breached.
Google partnered with computer scientists at Stanford University in developing the protocol behind the technology – which Google candidly admits is still experimental and therefore potentially subject to shortcomings.
The tech giant plans to further refine the technology over the coming months, for example by improving site compatibility and username and password field detection.
An unusually large group of Google engineers and research scientists are behind Password Checkup, more than 30 of whom are credited for assisting in the creation of the extension.
Google and its academic partners said they have developed new privacy-preserving techniques, which means that Google will never access a user’s username or password, and that any breach data stays safe from wider exposure.
“Password Checkup needs to query Google about the breach status of a username and password without revealing the information queried,” Google states.
“At the same time, we need to ensure that no information about other unsafe usernames or passwords leaks in the process, and that brute force guessing is not an option.
“Password Checkup addresses all of these requirements by using multiple rounds of hashing, k-anonymity, private information retrieval, and a technique called blinding. Our approach strikes a balance between privacy, computation overhead, and network latency.”
Despite these efforts, some privacy advocates remain wary about the technology.
Paul Moore, an infosec consultant and CISO, warned: “Google’s new PasswordCheckup logs *every* web address you login to. So your passwords are stronger, but your privacy is busted.”
Martijn Grooten, the editor of industry journal Virus Bulletin and occasional security researcher, is more upbeat.
“Chrome is adding a HaveIBeenPwn-like check for insecure passwords. Good move: let password security be sorted by browsers and servers and just tell users not to choose ‘123456’,” Grooten tweeted.
Google appears to have developed a comparable technology to Mozilla’s Firefox Monitor, a built-in breach alert service released last November.
The tool, developed in partnership with Troy Hunt, checks users’ email addresses against the breach notification database Have I Been Pwned, developed by Hunt.
Both technologies address the growing problem of high profile data breaches, exacerbated by credential-stuffing attacks – a popular black hat tactic.






