Trustwave’s Shawn Kanady on the evolution of ransomware attacks, why the public sector appears to be taking the biggest hit, and whether organizations should pay the ransom
After something of a lull in 2018, ransomware is on the rise once again.
Just this month, for example, mailing and shipping services company Pitney Bowes confirmed it had been hit by a major ransomware attack, disrupting client access to its services.
Indeed, Europol has identified ransomware as the dominant form of cybercrime this year, while a report from cyber insurance firm Chubb indicates that it accounts for more than 40% of cyber claims.
Shawn Kanady, director of digital forensics and incident response at Trustwave, says the company has seen a “wave of activity” this year, following something of a quieter period in 2018.
We chat to him about the growing ransomware threat.
How is ransomware evolving?

Shawn Kanady: The bad guys are getting smarter. The new school is that it’s not just a ransomware hit: what they do is employ a banking trojan with a small payload. And this malware is now modular, so the attackers are sending back data to the command and control server; and based on what they’re finding, they’re making the determination on what malware they deploy. So that’s malware being used as a loader for other malware.
And what we’re seeing also, a new sort of twist, is the supply chain attack. We’ve seen this all the time in credit card breaches, but this type of attack is also being used to deploy ransomware now.
What are the attackers’ preferred targets?
SK: We’re talking about hospitals or city government-type places. They don’t have the IT, they have limited budgets, they have legacy systems, they’re really crippled when it comes to the ransomware, so they’re in a position where they don’t have time to come up with a strategy to recover. The attackers know that.
READ MORE Ransomware still dominates the cyber threat landscape in 2019 – Europol report
What are the most common mistakes?
SK: We need to be patching better. Every month, Microsoft is doing Patch Tuesday. But when they release their patches, what happens next is Hack Wednesday, because the attackers are looking at the list of vulnerabilities and devising exploits for them on day one, because they know that organizations can’t patch on day one.
And we’ve had some clients where they focused on the ransomware, decided that they were not going to pay, recovered some backups and everything was good; but they didn’t sanitize their data. Systems were backed up – and so was the banking trojan. While they recovered all their data, they also recovered the bad guys’ way in.
Also, I think a lot of clients are surprised at how long it actually takes to get a full recovery from backup. Then when you’re trying to sanitize the data, that takes a long time, and you need to be prepared for that.
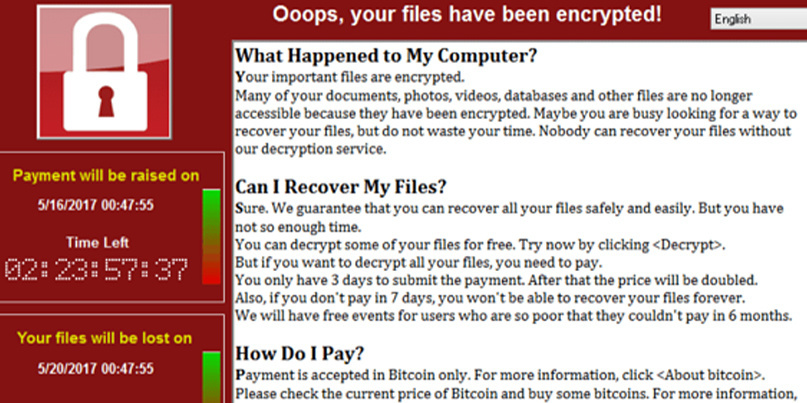
Should victims pay up?
SK: Trustwave would say that you don’t pay the ransom because that’s enabling the attackers. But in a hospital, there may be lives on the line. It’s a different question depending on what’s at stake.
What we do recommend is that there is a plan. This is not a decision that you want to make the day you’re faced with it. Secondly, if there’s a decision to pay, do you know how to set it up?
Though funnily enough, of the people deploying ransomware, some have a whole customer service department where you can call in and they’ll walk you through the process. It’s really ridiculous.






