Security mishandling – we haz it

2018 has proved to be a vintage year for connoisseurs of inept incident response, pig-headed handling of bug reports, and general dumbness in the field of cybersecurity.
Some vendors have gone out of their way to double down on questionable marketing claims. Elsewhere other organizations have stuck their head in the sand when confronted with a bug report. And users have joined in with dumb decisions, particularly in the arena of password security.
Bitfi is iffy: The John McAfee-backed cryptocurrency wallet raised the hackles of security researchers with claims that it was “unhackable”. Security researchers decried its bounty as a sham before going on to hack the device multiple times.
City of York app flap: Municipal authorities in the UK City of York went out of their way to mishandle a bug report. Rather than fix a flaw in a mobile recycling app, the City of York decided the best course of action was to report the bug discovery to the police and pull the app.
The council claimed it was forced into this course of action due to failures to respond to its follow-up questions by the bug hunters. This version of events was undermined days later when the researchers from went public with their notification email and other correspondence.
Police said the researchers had acted correctly, implicitly chastising the council for an erroneous crime report.
UK infosec pro Paul Moore followed up with a Freedom of Information request to the council demanding more info on its handling of the incident. He described the council’s response as “error-ridden, inaccurate and hilarious”.
The funnies centred on the City of York’s assertion that disclosing the hashing algorithm it used would constitute a national security threat.
Que?

TV wipe: Back in September, the UK’s TV licensing agency preferentially directed those looking to set up direct debit mandates to the insecure (http only) version of its site rather than the secure (https) alternative.
This threw up browser warnings which, scarcely believably, the social media team at TV Licensing told customers to ignore. It was only after a security researcher went public with his concerns, and other security experts such as Scott Helme, backed this assessment, that the agency backtracked.
There’s a hole in my bucket: Plenty of examples of leaky Amazon S3 buckets sprung up this year. Amazon responded in April with the release of new guidance that set privacy/security as standard. Good move – even if it failed to do much (at least initially) to stem the tide.
The Daily Swig reported on a particularly extravagant example of this problem in July. More than 6,000 job applications, including scans of passports, identification cards, and visas, were publicly available for months after a global recruitment agency misconfigured its Amazon S3 cloud storage setup.
The company in question, which we decided not to name due to ongoing data security issues at the time, went out of its way not to follow industry best practice in cloud administration, security controls and much more besides.

Unfair dinkum: The Australian government recently passed a law allowing the authorities to levy fines of up to A$10 million ($7.54 million) against companies that thwart demands to supply encrypted data.
By design, providers of end-to-end encryption software have no access to their users’ data. This might appear awkward if you’re Apple (iMessage), Facebook (WhatsApp), and/or another of the firms supplying mobile messaging apps that come with end-to-end encryption as standard, an increasingly popular choice by developers the really picked up traction following the revelations of US government spying, courtesy of Edward Snowden back in 2013.
Developers of Signal characterized Australian efforts to erect local barriers against the use of Signal and other encryption apps as a “disappointing development” that was doomed to failure – not least because it will be difficult to enforce.
For one thing, users keen to get secure mobile messaging can download them directly from vendors’ sites even if they get pulled from local (Australian) app stores.

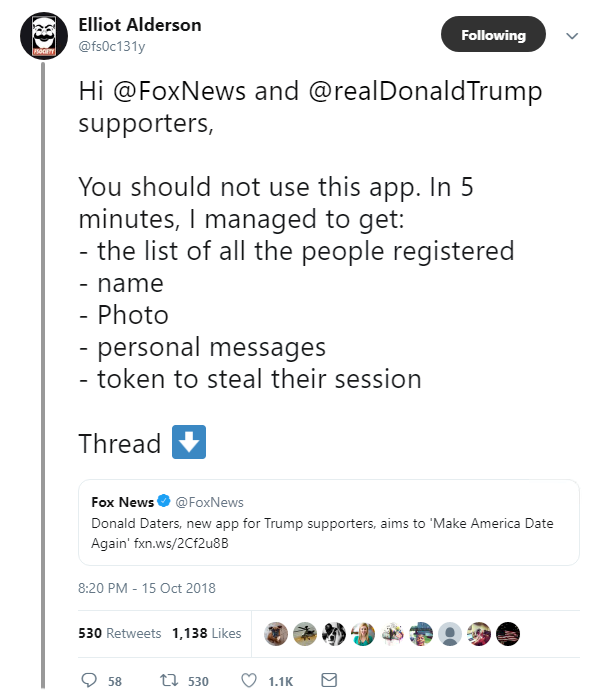
Make America date again: A new dating app aimed at Trump supporters hit the headlines for all the wrong reasons back in October after it was immediately found to be leaking its entire database of users.
Bad.
Hackity hack (don’t look back): Operational security (OpSec) mistakes have ultimately led to the identification of many hacking types over the years. Accidentally logging into a botnet command server or hacktivist chat room without the shield of anonymity offered by Tor or through a VPN allows authorities to identify a user’s real IP address, and thus their real locations.
But what happens when police and forensic examiners come knocking at a suspect’s door? Sometimes they uncover more evidence than they might plausibly have expected.
An Australian 16-year-old who broke into Apple’s network and downloaded internal files decided to store incriminating documents in a folder called ‘hacky hack hack’. That wasn’t his only OpSec mistake. He was also accused of boasting of his criminal antics on WhatsApp. Despite his various misdemeanours he avoided being sent to jail.
The teenager – whose name was withheld since he was only a juvenile at the time of his offending – hacked his way into Apple’s network multiple times during a year-long hacking spree, The Age newspaper reported.
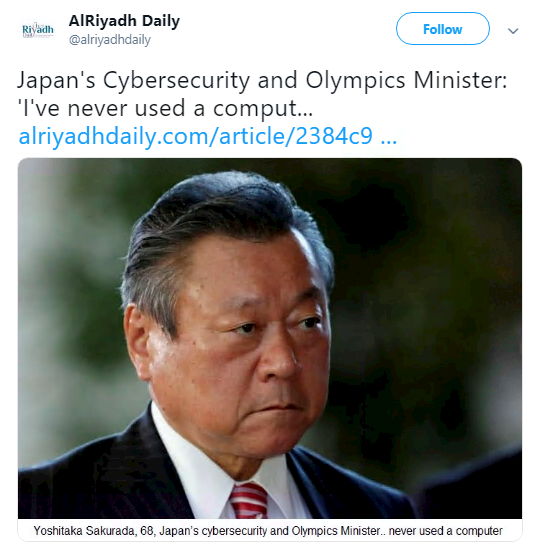
Off grid: Staying with the field of politics, Japan’s cybersecurity minister drew gasps of astonishments when he admitted that he’d “never used a computer” in November.
Yoshitaka Sakurada, 68, told a parliamentary committee that he asked his secretaries and officials to handle anything involving computers.
Appearing before a parliamentary committee, Sakurada raised eyebrows in response to a question about the vulnerability of Japan’s power distribution system to potential hacking attacks.
The minister responded that USBs were “basically never used” in the country’s utility systems, as if Stuxnet-style attacks were the only potential avenue of attack. Lawmakers laughed nervously at his replies, AP reports.
Before the flood: Security ought to extend beyond the most obvious privacy concerns to cover the integrity and availability of data and systems, as representatives of TSB might attest.
A group of software developers cracking open the champagne after completing a tough platform migration project is all very agreeable, but the act reeks of hubris when the system goes belly-up shortly after going live.
The TSB meltdown must have left software coders at Banco Sabadell, TSB’s Spanish parent firm, shamefaced. Coding flaws played an important role in April’s system meltdown that left hundreds of thousands unable to access online banking services across several days.

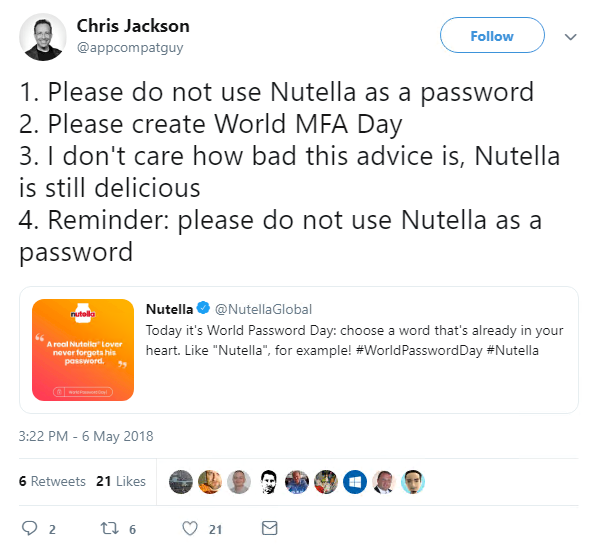
Stronger: The arena of password security, as usual, threw up all manner of gaffes.
Chocolate spread brand Nutella erred badly back in May in asking its Twitter followers to change their passwords to Nutella – on world password day, of all dates.
And Kanye West showed the PIN code on his phone to the entire world when meeting with President Trump – it was ‘000000’.
Tory boy oh boy: The Conservative party conference app went live without any authentication and security in place. As a result, people could access MPs details simply by entering an email address.
Mischief makers were able to change delegates’ profile pictures as well as leave messages on the app's internal messaging system. Cabinet minister Michael Gove’s profile picture was changed to a snap of media mogul Rupert Murdoch, among other pranks.
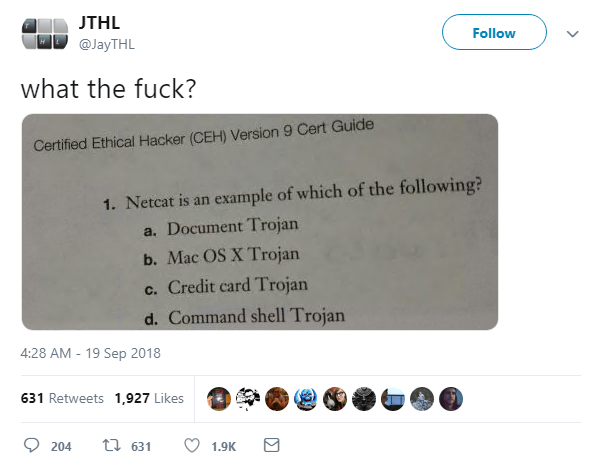
Certified Ethical Hacker cracker: Education and training aren’t immune to the occasional lapses into stupidity either. How else to explain a multiple-choice question of the popular Netcat computer networking tool in the CEH exam otherwise?
Netcat is being framed, as an old school networking engineer might joke. Packet in!