Flagrant tales of epic (security) fails

Stupid criminals, careless politicians, inept bug handling, and more slapdash – or just plain stupid behavior – were abundant in the arena of cybersecurity over the past 12 months.
Everyone involved in this year's #StupidSecurity run-down ought to resolve to do better in 2020, perhaps by starting to cast an eye over examples of the people and organizations who’ve handled infosec problems with a bit more grace, preparation, and better passwords. Sounds familiar..
Inept bug handling
Bug bounties and ethical hacking – particularly in the field of web security – are a major topic of interest for The Daily Swig.
Vendor missteps are legion but sometimes it’s the bug hunters who get it wrong.
Back in July, developers of the VLC media player were able to debunk widely covered reports of a ‘critical security issue’ in their popular open source software.
Jean-Baptiste Kempf, president of VLC owner VideoLAN, told The Daily Swig that the exploit did not work on the latest VLC build. In fact, it turned out that any potential issues related to the vulnerability were patched more than a year ago.
CERT-Bund – which initially flagged the issue as critical - downgraded the vulnerability to ‘low’ impact after we challenged the organization on its originally published classification, which was based largely on a public ticket.
Missteps in bug handling are more common on the vendor rather than researcher side, of course.
July brought the discovery of a Zoom client bug that allowed any site to force Mac users into video chat.
Security researcher Jonathan Leitschuh went public with a vulnerability in the Mac version of the Zoom video conferencing app that could allow a malicious site to auto-join Mac users to a video call and enable their webcam without permission.
Security researchers faulted Zoom for its initially dismissive response to the issue.
Check out the latest bug bounty and security news
Data breaches
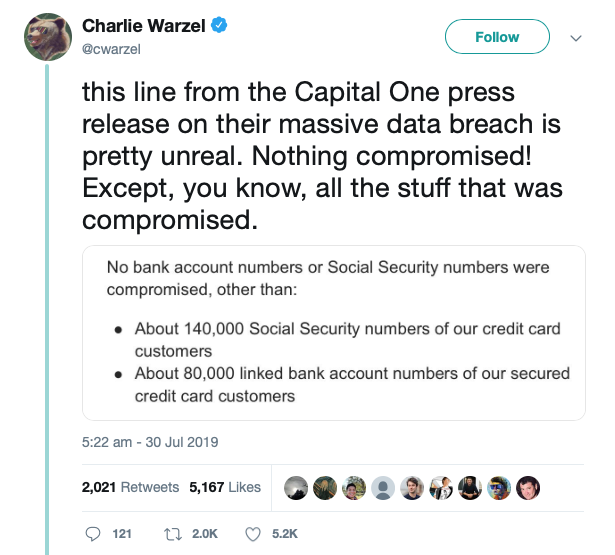
Capital One grabbed news headlines in July when the US financial services company announced that some information of approximately 106 million people residing in the US and Canada had been exposed.
The criminal breach also compromised more sensitive information on a smaller number of customers: 140,000 Social Security numbers, 1 million Canadian Social Insurance numbers, and 80,000 bank account numbers.
Capital One tried to deflect attention from this aspect of the problem, much to the derision of the security community.
The alleged perpetrator, Paige A. Thompson, gained access through a misconfiguration of a cloud-hosted web application, according to prosecutors.
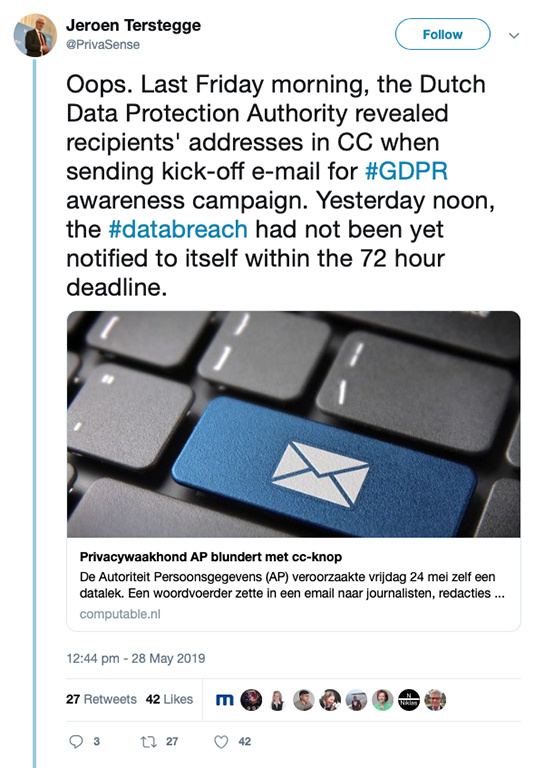
On a much smaller scale, the Dutch Data Protection Authority was left red-faced back in May after it failed to report itself on time over a minor data breach, caused by one of its own employees.
Oops.
Policy Fubars
DNS-over-HTTPS (DoH) – an emerging web protocol that aims to protect online privacy online – became the arena for policy controversies this year.
The technology is supported by browser makers including Google and Mozilla but criticized by some because of its reliance on third-party DNS providers, among other reasons.
The Internet Service Providers Association (ISPA) controversially argued that DoH impedes web blocking programs going as far as nominating Mozilla as an “internet villain” over its support of the technology.
The ISPA trade association was obliged to backtrack and pull the nomination after a backlash from sections of the internet security community.
What could be a more awkward – if not plain ridiculous – situation than to be arrested while doing your job?
But that’s what happened to two staff at US security consultancy Coalfire, who were arrested during late night physical pen tests at a courthouse in Dallas County, Iowa, back in September.
Dallas County Iowa Sheriff Chad Leonard told The Daily Swig that he acted properly in arresting the two infosec workers who “went outside the scope of their contract”.
PINdown
In August, digital bank Monzo told hundreds of thousands of customers to change their PINs after it realized it was accidentally storing sensitive customer data in log files.
Monzo isn’t alone when it comes to slip ups in this area.
For example, back in March it was revealed that Facebook had been logging web requests containing clear-text passwords for years.
Facebook came under fire once again months later, in September, over a data leak that exposed the phone numbers of “hundreds of millions” of its users.
Having had its share of privacy scandals, Facebook's all-caps rebrand in November – to FACEBOOK – was also widely mocked as tone deaf. A design that said ‘reflective repentance’ may have been viewed as more appropriate.
Check out the latest data breach and security news
Password gaffes
Last year in Stupid Security, Kanye West infamously exposed the PIN code of his phone in front of the spectating press corps during an Oval Office meeting with President Trump. The rapper was captured tapping in ‘000000’ to unlock his iPhone.
But 2019 showed us that it's not only rappers who fall victim to easy to guess PIN codes.
In October Congressman Lance Gooden made much the same security slip up in revealing his phone password was ‘111111’ by entering the code during a filmed Congressional session.
Gooden made light of his faux pas, choosing to disregard the part that hacking played in the 2016 US presidential election cycle or the sensitivity of the communications the first-term congressman handles.
The Republican congressman isn’t alone in being captured by cameras in making a questionable security trade-offs.
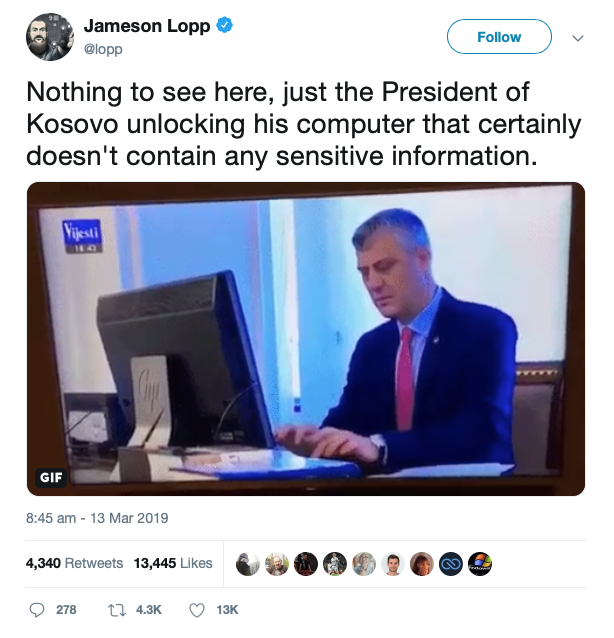
Back in March, a video surfaced on Twitter that appeared to show Hashim Thaçi, the President of Kosovo, logging into his computer using an all-too-simple password.
Passwords remain a necessary evil despite predictions that we’re moving towards a passwordless future, a warm future that’s perennially two or three years away..
One online resource, a Dumb Password Rules tool, spotlights firms that take an ‘idiosyncratic’ approach to password policy.
Examples of curious policies include those of the BMO (Bank of Montreal), where users’ passwords must be exactly six characters long and include no special characters..
Entropy, they’ve heard of it. Or perhaps they haven’t?!
LISTEN NOW SwigCast, Episode 4: MAGECART
OpSec
John McAfee – who we sense will become a fixture of this annual list – backed up his support for a much criticised crypto-currency wallet last year with a stand-out performance in a different category, OpSec fail.
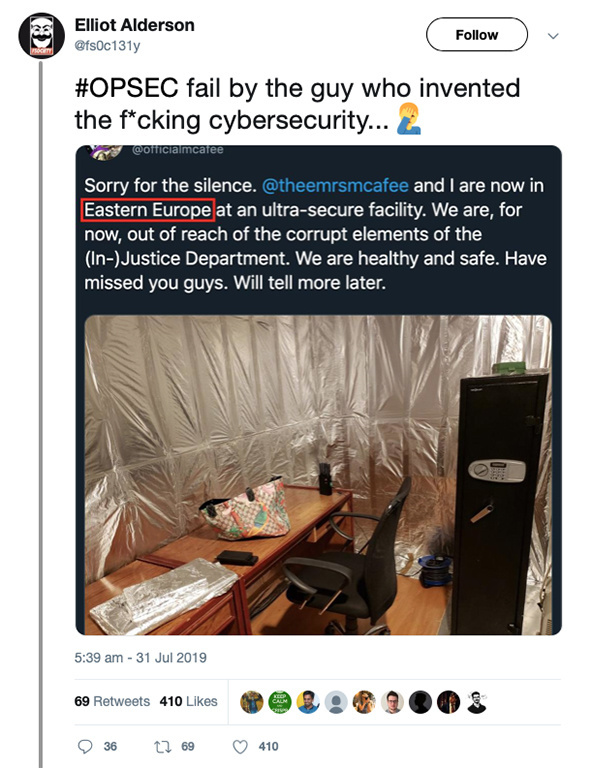
In July, McAfee posted pictures on Twitter that revealed that he was holed up in Vilnius, Lithuania, in a tin-foil lined room. The disclosure followed days after McAfee and his entourage were arrested after his yacht docked in the Dominican Republic over concerns that Army-grade weapons were on board.
The group were released without charge four days later before resurfacing in eastern Europe.
USB key(stone) cops
Criminals and police alike served up a steady diet of WTF moments in infosec over the last 12 months.
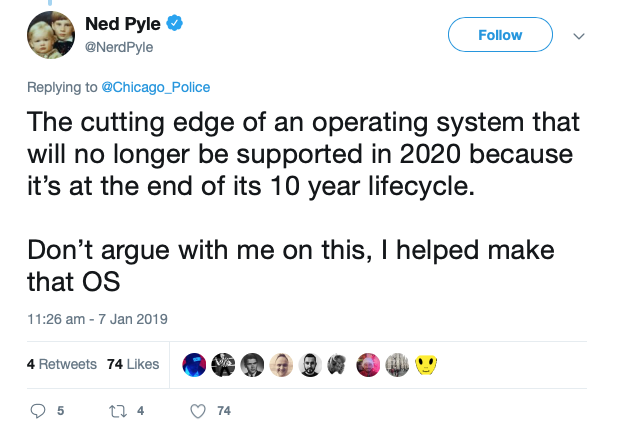
In January, a Microsoft employee chided the Chicago Police Department over claims the police force’s Windows 7 machines were at the “cutting edge of technology”.
In July somebody hijacked the Met Police’s official newsfeed and Twitter account, a small example of a wide field of slapdash security that involves what might loosely be described social media shenanigans.
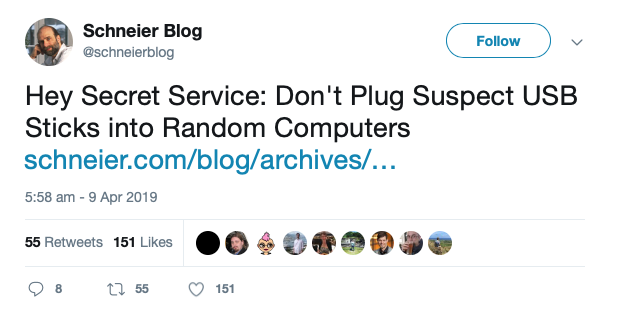
Staying with police-related security missteps, Chinese citizen Yujing Zhang was arrested at Trump’s Mar-a-Lago club in Florida with suspect items including multiple phones, two passports, and a USB stick that it turned out was stuffed full of malware.
It emerged that the US Secret Service – trained security professionals, lest we forget – plugged the suspect USB into one of their computers.
Not so much Bodyguard as the booby-trapped guards.
YOU MIGHT ALSO LIKE Swig Security Review 2019: Part II