Top infosec trends in the social media spotlight this week

Cryptocurrency enthusiasts were once again put through the wringer this week, as news emerged of a hack against South Korean exchange, Bithumb.
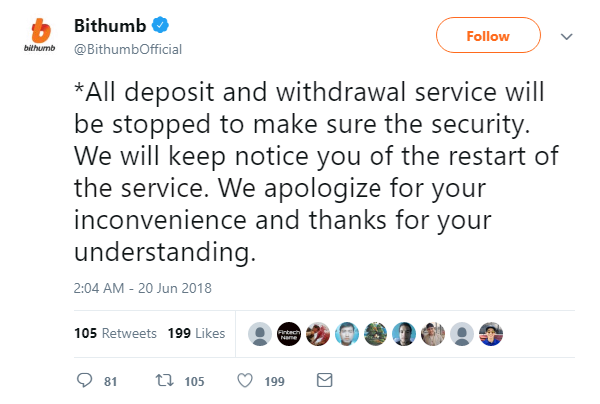
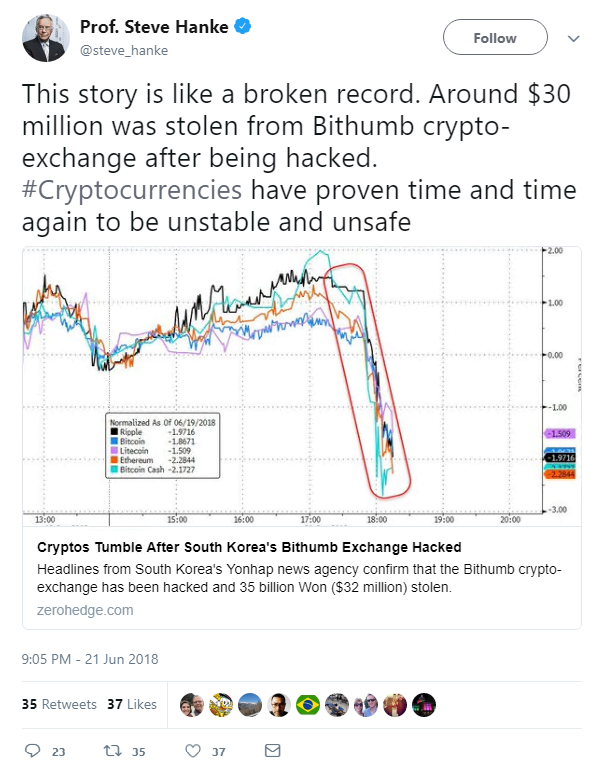
The Seoul-based operator – one of Asia’s biggest crypto-exchanges – said on Wednesday that hackers had seized KRW35 billion ($31 million) in virtual currency from its hot wallet.
Bithumb has suspended deposits and withdrawals until further notice, and said it was working to reimburse affected users. Many, however, were less than impressed:
News of the breach comes just days after Coinrail, another South Korean crypto-exchange, provided details of a hack that resulted in a loss of around 30% of the coins traded on the platform.
While the organization said the exact value of the stolen currency is yet to be confirmed, South Korean news agency Yonhap said this could be in the region of KRW40 billion ($37 million).
In business news, F-Secure has acquired MWR InfoSecurity, a UK-based cybersecurity firm, for £80 million ($106 million).
The transaction will bolster F-Secure’s active defense capabilities through the addition of MWR’s flagship threat hunting platform, Countercept.
According to F-Secure, security perimeters are no longer enough to protect organizations. The Finnish company said the acquisition will help businesses to be more proactive in the fight against increasingly advanced cyber-attacks.
“Their threat hunting platform is one of the most advanced in the market and is an excellent complement to our existing technologies,” said F-Secure CEO, Samu Konttinen. “We will have unparalleled visibility into real-life cyber-attacks, 24/7.”
Phishing scams hit the headlines once again this week, as researchers found an age-old font-manipulation technique was now being used to bypass Office 365 security scans.
The attack – dubbed ‘ZeroFont’ – involves inserting hidden words and letters into an email, which can trick Microsoft and are also invisible to the reader.
The ZeroFont study was followed by separate reports that the Oregon.gov domain has been blacklisted by email services run by Microsoft, after an employee for the state was duped by a phishing scam.
The incident saw more than eight million spam emails being sent from an Orgeon.gov email address, resulting in the domain’s reputation score being downgraded by the software giant.
The problem still doesn’t appear to have been fixed as of this morning. A statement on Oregon Governor Kate Brown’s website reads: “Issues with the Oregon.gov domain are preventing communication from state employees with an Oregon.gov email address sent to members of the public who use the following email providers: Outlook.com, Msn.com, Hotmail.com, and Live.com.”
And finally, a recent US court case has brought a whole new meaning to the phrase ‘domain hijacking’, after a man was convicted for breaking into someone’s home and physically forcing them to transfer ownership of their website.
According to the Department of Justice, Sherman Hopkins, 43, admitted to entering a property in Iowa last year and “pistol-whipping” the victim in an attempt to obtain the domain doitforstate.com.
“Hopkins pulled out a piece of paper from his pocket, which contained a series of directions on how to change an internet domain name from one GoDaddy account to another GoDaddy account,” the DoJ said in a filing.
“Hopkins put the firearm against the victim’s head and ordered him to follow the directions on the piece of paper.”
The court heard how the victim eventually managed to gain control of the gun and shot Hopkins “multiple times” in the chest.
The would-be domain thief survived the shots and has now been sentenced to 20 years in prison.