Tools, techniques, and (hybrid) procedures

Hacker Summer Camp 2021 adopted a hybrid format this year, as the restrictions imposed by the ongoing coronavirus epidemic meant that the majority of participants to Black Hat and DEF CON tuned in online rather than turning up in Las Vegas.
CATCH UP Black Hat 2021: Zero-days, ransoms, supply chains, oh my!
Security researchers made up for the lack of audience interaction by showing that – like the athletes competing at this month’s Olympics and Paralympics – they could go faster, higher, and stronger together.
Still catching up on the proceedings? Look no further:
Attacking Let’s Encrypt

At Black Hat, researchers from the Fraunhofer Institute for Secure Information Technology showed how the security controls introduced with Let’s Encrypt’s multi-perspective validation feature might be abused.
Circumventing these controls, which were introduced in February 2020 in response to earlier attacks, makes it possible for attackers to get digital certificates for web domains they do now own, offering a springboard for phishing attacks or other scams.
By introducing packet loss or latency to connections to some of the nameservers, an attacker could force the system to rely on a nameserver of their choice – downgrading the security offered by multiperspective validation.
The work shows that domain validation, though it enjoys advantages because it is low cost and lends itself to automation, is not yet secure and needs to be refined in order to become more effective as a barrier to fraud.
Pulling the pin on FragAttacks
At Black Hat, security researcher Mathy Vanhoef shared his impressive work on FragAttacks fragmentation and aggregation attacks) and – with the help of Tom Van Goethem – timing attacks.
For the former, he described how implementation flaws and design vulnerabilities in WiFi’s frame aggregation and fragmentation features affect all protected WiFi networks, and even the WEP protocol dating back to 1997.
Certain implementation bugs were particularly widespread and trivial to exploit, he warned.
The gradual adoption of ‘operating channel validation’ (PDF) and ‘beacon protection’ (PDF) will eventually offer a degree of protection from FragAttacks, he said.
In a separate presentation last week, Vanhoef and Van Goethem elevated timing attacks to fresh heights, after surmounting a challenge that previously complicated remote assaults.
Timing attacks, which infer secrets by measuring the execution time of cryptographic algorithms, have led to vulnerabilities surfacing in applications and cryptosystems that lack constant-time execution.
While these side-channel exploits are possible over modern internet connections, “network jitter” has forced adversaries to collect thousands or millions of measurements to infer just a single bit of information.
However, ‘timeless timing attacks’ are unaffected by network jitter because “two requests arrive in the same packets at the exact same time at the server”, explained Van Goethem.
As a result, timing differences as small as 100ns can be detected over any internet connection – an accuracy comparable to attacks on local systems.
Attacks can be launched against protocols that enable multiplexing or by leveraging a transport protocol that enables encapsulation, with the researchers successfully mounting attacks against HTTP/2 webservers and EAP-PWD, a popular Wi-Fi authentication protocol.
Check out our previous coverage for more on this hacking technique.
Request smuggling redux
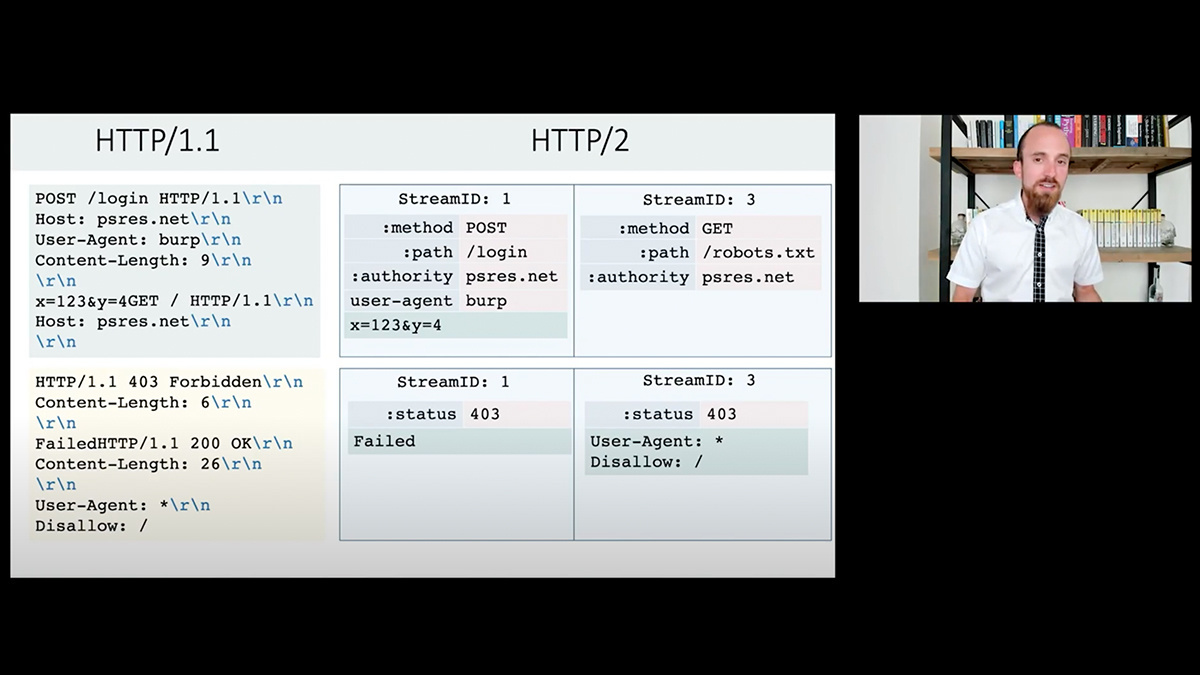
PortSwigger security researcher James Kettle was back with a fresh perspective into how request smuggling can impact HTTP/2 infrastructure.
The researcher demonstrated how attacks levied against HTTP/2 systems enabled him to steal secrets from websites running Amazon’s Application Load Balancer, poison every page on Bitbucket, and forced Atlassian to sign every single one of its users out of Jira.
“If you take your frontend server, turn on HTTP/2 support and do downgrading, congratulations: you have just doubled the number of ways that you may be vulnerable to request smuggling,” Kettle warns.
Check out our earlier coverage for full details on this latest web security research, which was presented at both Black Hat USA and DEF CON this year.
Microsoft Exchange findings create ‘new paradigm for vulnerability research’
Hacking whizz Orange Tsai lifted the lid on what he described as potentially “the most severe vulnerability in the history of Microsoft Exchange”.
Fresh from his recent Pwn2Own and Pwnie Awards triumphs, the researcher recounted his discovery of a pre-authenticated remote code execution (RCE) flaw that was involved in the compromise of hundreds of thousands of enterprise messaging servers worldwide.
But this was more than just another, albeit serious security flaw; it created a “new paradigm for vulnerability research”, no less.
Tsai, principal security researcher at Devcore, discovered server-side, client-side, and cryptographic bugs on this “new attack surface” and corralled them into pre-auth RCE chains known as ProxyLogon and ProxyShell, along with ProxyOracle, a plaintext password recovery combo.
The implications are serious: Microsoft Exchange Server is widely used by enterprise organizations and government agencies and Tsai found 400,000 internet-facing instances.
The researcher said his investigations, which centered on a major architectural change made to Client Access services (CAS) in 2013, was so fruitful because he surveyed the target application from a high-level architectural perspective rather than simply hunting for particular vulnerability types.
Despite Microsoft’s best efforts to bolster security, Microsoft Exchange remains “a buried treasure with more bugs” lying in wait, Tsai concluded.
Hacking humans using AI as a service
A potential future of AI-assisted social engineering was mapped out during a forward-looking talk at DEF CON.
Artificial Intelligence as a Service (AIaaS) products such as OpenAI's GPT-3 API have made advanced technologies more easily available at a modest cost.
Three Singapore-based researchers were able to repurpose personality analysis AIaaS products to generate convincing phishing emails that were based on a target’s social media profile. The task played to the strengths of natural language generators bundled with AIaaS products.
For mass targeted phishing emails, human-created content attracted more interaction. But in targeted spear phishing exercises, carried out as part of authorised pen testing exercise, responses to AI-generated phishing emails were higher.
It’s not all bad bad news.
The researchers outline techniques that might be applied to detecting synthetic texts as well as governance principles AIaaS providers ought to consider adopting.
IPVSee you
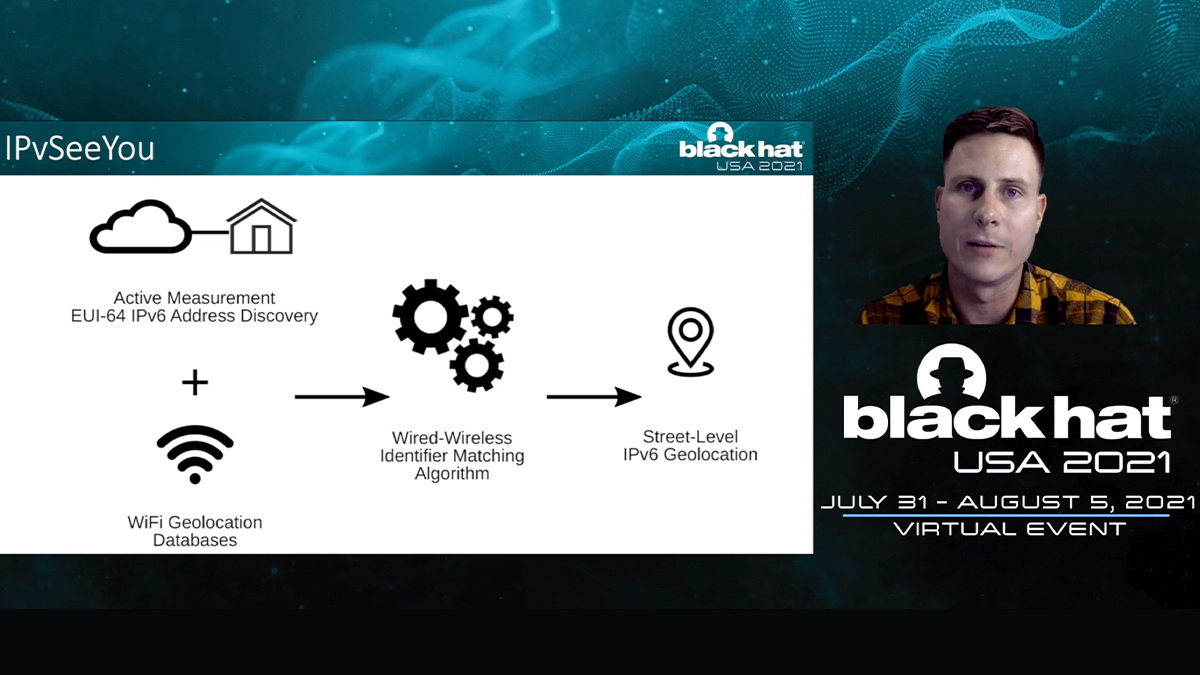
During Black Hat, researchers from the Center for Measurement and Analysis of Network Data (CMAND) demonstrated IPVSee You, a privacy disrupting attack that can discover and precisely locate millions of home routers in use across the world.
It is described as a “large-scale data fusion attack” that combines EUI-64 IPv6 addresses with Wi-Fi and geolocation data in order to produce IPv6 street-level geolocations.
While EUI-64 IPv6 addresses are no longer used by most operating systems, they are commonly found in legacy and low-profit-margin customer premises equipment (CPE), for example commodity routers connecting home and business subscribers.
“Because IPv6 CPE are routed hops (as opposed to IPv4 NATs), we can discover their MAC address via traceroute if they use EUI-64,” the researchers explained.
Anyone using a ping6 or traceroute6 can find a router’s location with “street-level” precision – aka pinpointing the exact home.
Erik Rye, researcher at CMAND, said that they encrypt all of the data that they receive, and publish only the aggregate data analysis rather than the underlying data itself.
He added: “It’s worth remembering that our goal here is ultimately to improve privacy protections by highlighting this location.”
Sleepless
Hacking IoT devices was the theme of several talks across Black Hat and DEF CON. For example, researcher Kya Supa discovered a way to hack the room controls in a capsule hotel.
The exploit he developed – which relied in part on weak WEP wireless encryption, default credentials on networking kit, and low entropy passwords – allowed him to control the lights, fan, and raise or lower the sofa/bed in other capsule units in a hotel.
By programming the changes, Supa was able to turn off and on the lights and turn the bed into a sofa every two hours in a capsule occupied by another (inconsiderate) guest (who had reportedly insisted on talking loudly on his phone at night and ignored requests to be more considerate).
The moral? Don’t mess with the sleep of hackers.
Over at DEF CON, robot vacuum cleaners were rooted by Dennis Giese. Giese’s hack enabled owners to use their devices safely with open source home automation, avoiding built-in features that automatically uploaded data to the cloud. Hacker Joseph Gabay presented his research on hacking shopping cart immobilisers, a topic he got into basically out of love for a technical challenge and locksmithing.
Returning closer to the mainstream, and of particular relevance with more people working from home, hacker Matthew Bryant offered a talk at DEF CON on using Apps Script to exploit G Suite (AKA Google Workspace).
Apps Script payloads can be developed to bypass protective controls such as U2F and OAuth app allowlisting. App Scripts run on Google’s infrastructure and therefore present a way to backdoor compromised accounts even if a target changes their machine.
Do you like to read? I know how to take over your Kindle with an e-book
Over at DEF CON, Checkpoint researcher Slava Makkaveev demonstrated how he was able to takeover a victim’s Kindle e-reader via a malicious e-book.
Kindle, which is made by Amazon, enables users to download books and other documents onto a portable device.
Makkaveev showed how he was able to create a malicious book which could be published and made available for free access in any virtual library, including the official Kindle Store, or sent directly to the end-user device via Amazon services.
When a Kindle user opens the e-book on their device, hidden code is executed that has root rights.
“From this moment on, you [have] lost your e-reader, account, and more,” the researcher commented.
Once an attacker has this access, they are able to execute further attacks including by turning the device into a bot to attack other local networks.
Tooling upgrade
As ever, the Arsenal track at Black Hat was replete with dozens of new hacking tools and frameworks. Here are some highlights from this year:
- WARCannon – Open source tool makes grepping the internet for web vulnerabilities simpler, faster, and cheaper. Read more.
- Enfilade – Open source tool that flags ransomware and bot infections in MongoDB instances. Read more.
- USBsamurai – Malicious USB cable leaves air-gapped networks open to attack. Read more.
- Scrapesy – Credential leak detection tool aims to reduce incident response times. Read more
Check out our regular Latest Web Hacking Tools column for more offensive and defensive tooling.
Additional reporting by James Walker, Adam Bannister, and Jessica Haworth.
RECOMMENDED Black Hat Briefings: Hosted DNS configuration flaws risk leaking corporate network topologies






