We take a look at the latest additions to security researchers’ armory

After our recent end-of-year retrospectives, it’s time to look back again – this time at some of the most compelling open source hacking tools released during the final quarter of 2021.
The arsenals of pen testers, researchers, and bug hunters have been bolstered for 2022 by new tools for detecting dependency confusion attacks, finding novel HTTP request smuggling techniques, and uncovering leaked, paired private and public keys that are potentially dangerous.
Read on to discover some of the best hacking tools that were launched at the tail end of last year.
Google-backed ‘Pip-audit’ probes Python environments for vulnerable packages

The developers of a Google-backed tool that scans Python environments for packages with known vulnerabilities “wanted to build a tool that didn’t have any financial or licensing strings attached”.
William Woodruff, project lead at New York-based cybersecurity firm Trail of Bits, told The Daily Swig they also “wanted something that works well for both humans and machines: a lot of tools (like Dependabot, which is also great) lock tightly into either user or automated workflows”.
‘Pip-audit’ leverages the PyPI JSON API to compare dependencies against the Python Packaging Advisory Database or alternatively the Open Source Vulnerabilities (OSV) database.
Read more about the pip-audit tool
Sandbox helps ascertain whether OWASP ModSecurity CRS can ‘buy time’ in face of new CVEs

The new sandbox for testing payloads against the OWASP ModSecurity Core Rule Set (CRS) requires no ModSecurity box installation.
It can help people facing a new CVE find out whether CRS – a set of generic attack detection rules for use with ModSecurity or compatible web application firewalls (WAFs) – “could buy them time”, according to the project maintainers.
They also said the CRS Sandbox can help to secure the CRS project itself, “since we can quickly test payloads against various versions and backends to confirm GitHub issues (false negatives, false positives).”
Read more about the CRS Sandbox
Differential fuzzing tool uncovers novel HTTP request smuggling techniques
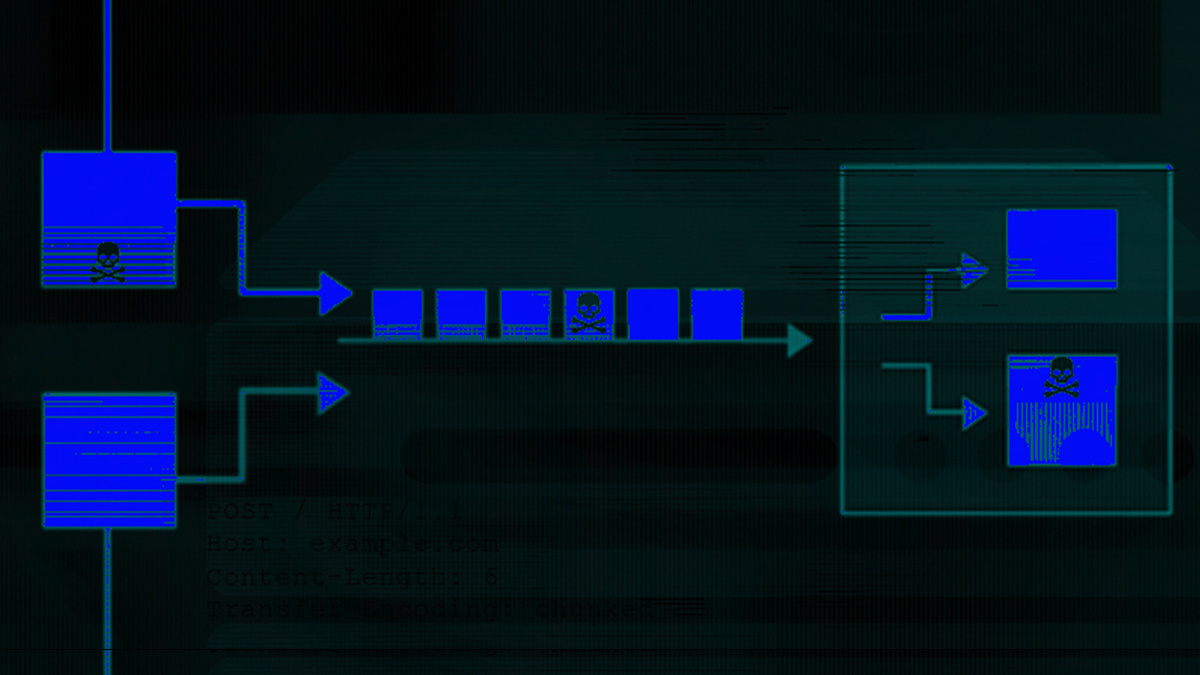
A new grammar-based HTTP fuzzer unearths novel HTTP request smuggling techniques by generating HTTP requests and applying mutations in order to trigger potential server processing quirks.
Researchers from Northeastern University, Boston, developed ‘T-Reqs’ with the help of Akamai and said they soon discovered a wealth of new vulnerabilities with the tool.
Their research focused on HTTP request smuggling as a system interaction problem involving at least two HTTP processors on the traffic path.
Read more about the T-Reqs fuzzing tool
Driftwood detects potentially harmful encryption keys

‘Driftwood’ is used to discover leaked, paired private and public keys that are potentially harmful.
Truffle Security developed the tool to let “security professionals immediately know if an identified encryption key is a sensitive key” across online repositories.
“The first step to remediating vulnerabilities is knowing about them,” Truffle Security co-founder Dylan Ayrey told The Daily Swig.
“If people commit SSL keys today, it’s hard to know about it. This tool helps infosec professionals quickly find these vulnerabilities so they can get the affected certificates revoked asap.”
Read more about the Driftwood tool
Dependency Combobulator combats namespace confusion attacks

Dependency Combobulator detects dependency confusion attacks, which have plagued the open source software ecosystem since the technique was disclosed in February 2021.
Unveiled at Black Hat Europe 2021, the modular, Python-based framework can be embedded within the software development lifecycle (SDLC) and CI/CD workflows, detecting malicious packages at the SDLC’s commit, build, or release phases.
Moshe Zioni, VP of security research at DevSecOps vendor Apiiro, which developed the toolkit, said Dependency Combobulator can “tackle common scenarios, which can be diverse”, and be adapted to detect emerging attack variations.
Read more about Dependency Combobulator
Venerable password auditing tool L0phtCrack is open sourced

Windows system password auditing tool L0phtCrack was open sourced in October after the venerable utility fell back into the hands of the original owners in June following the collapse of its acquisition by Terahash.
L0phtCrack, which was launched more than 20 years ago, can audit Active Directory passwords and import and crack passwords from Linux, BSD, Solaris, and AIX (Unix-based systems).
Chris Wysopal, a former member of hacker collective L0pht Heavy Industries, which built the tool, told The Daily Swig: “I think this could be a framework for more than just password cracking eventually, rather the general automation of commonly performed ‘security audit’ tasks.”
Read more about the L0phtCrack utility






