Kudos to Tonga’s ccTLD, the US Supreme Court, and others…
Infosec headlines are typically dominated by data breaches, cyber-attacks, vulnerabilities, and other threats or incidents where human error often has a part to play.
The Daily Swig has decided to redress the balance by spotlighting some positive news stories highlighting commendable actions by cybersecurity professionals and organizations, developers and open source maintainers, and even journalists and judges.
(We haven’t included any ground-breaking security research that came out during 2021 – we’ll leave that to Portswigger researcher James Kettle’s forthcoming annual roundup of top web hacking techniques, a follow-up to the 2020 round-up.)
First website dedicated to revealing vulnerabilities in malware
The year kicked off with the launch of a pioneering database that indexes exploit code for security flaws in malware.
Founder John Page told The Daily Swig that the repository might be “useful for incident response teams to eradicate a malware without touching the machine”, and “may eventually pit a malware vs. malware situation, who knows.”
Similarly, Abuse.ch unveiled a platform for sharing and requesting indicators of compromise (IoCs) associated with various malware strains in March.
SolarWinds blow away US government cybersecurity complacency
The SolarWinds attack that hit federal agencies and blue chip companies alike at the end of 2020 served as a wake-up call for the White House.
An Executive Order signed by newly elected President Biden in May set the tone for a busy year on the cybersecurity front.
There followed new rules on reporting ransomware payments and securing critical transport infrastructure; an overhaul of federal government software procurement practices; a series of 60-day ‘sprints’ aimed at building cyber resilience; plans for US federal agencies to establish a system for rapidly patching hundreds of known, exploited flaws; a ‘Hack the DHS’ bug bounty program; and a first-ever vulnerability disclosure program for federal civilian agencies.
“The administration is making good steps insofar as bringing it to light, starting initiatives, hiring a new CISA director, and getting a conversation started with various other nation states about what we’re going to do about this,” Aaron Portnoy, principal scientist at attack surface management specialists Randori, told The Daily Swig in July.
US Supreme Court liberates security research
The US Supreme Court tilted the scales of justice decisively in favor of ethical hackers, after issuing a ruling in June that effectively narrowed the scope of what constitutes ‘unauthorized access’ under the Computer Fraud and Abuse Act (CFAA).
Infosec experts have long criticised a chilling effect the CFAA’s ambiguity over what constitutes good-faith hacking has had on security research.
The ruling should reassure the likes of the civic-minded journalist who was threatened with legal action by Missouri governor Mike Parson – to widespread ridicule – after he responsibly reported a severe vulnerability in a state government website.
Nevertheless, many think the law, which dates back to 1986, should be replaced altogether.
The UK announced a review of its own, equivalent legislation, the Computer Misuse Act, in May, following an industry-led campaign.
OWASP Top 10 gets long-overdue refresh
The Open Web Application Security Project (OWASP) updated its Top 10 web app threat categories in September for the first time since 2017.
There were three new categories – ‘Insecure Design’, ‘Software and Data Integrity Failures’, and a designation for ‘Server-Side Request Forgery (SSRF)’ attacks – along with name changes for several other categories.
The revamp reflects the software industry’s “‘shift left’ towards putting more focus on secure design and architecture as well as threat modeling,” Tom Eston, practice director of application security at Bishop Fox, told The Daily Swig.
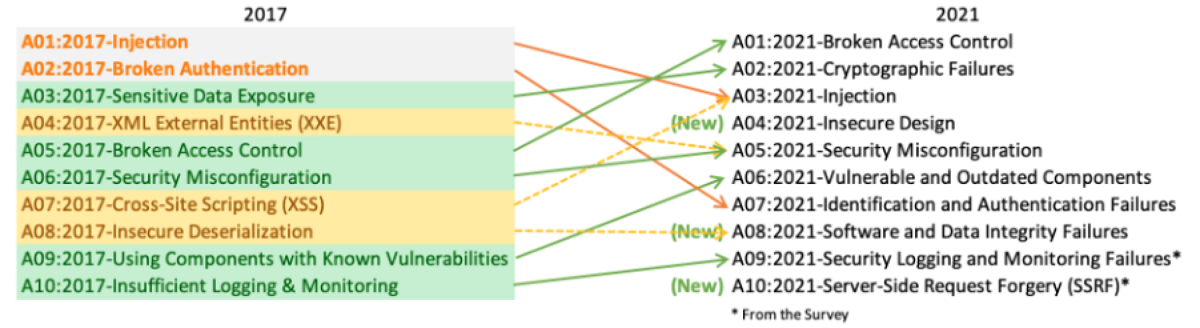 The refreshed OWASP top 10
The refreshed OWASP top 10
HTTPS finally nearly everywhere
The deprecation of the HTTPS Everywhere browser extension, announced in September, is a case of ‘mission accomplished’ in the view of its developer, The Electronic Frontier Foundation (EFF).
Launched in 2010, the plugin automatically switched web connections from HTTP to HTTPS, if the latter was available, and accrued more than two million users in the absence of similar, in-built functionality in popular browsers.
The open source extension will go into ‘maintenance mode’ in 2022 amid widespread HTTPS adoption, and after Google and Firefox’s enforcement of HTTPS by default made the plugin mostly redundant.
The changes are among a raft of other browser security developments The Daily Swig has spotlighted throughout 2021.
Google offers defensive shield against surveillance
October saw Google use some of its vast resources to protect journalists, elected officials, and human rights activists from surveillance, persecution, and imprisonment.
The tech giant partnered with human rights and pro-democracy organizations to distribute free physical security keys to more than 10,000 vulnerable individuals at high risk of being targeted by nation-state backed hackers under its Advanced Protection Program (APP).
Record bug bounty payout demonstrates value for money
A record bug bounty payout in October starkly demonstrated the worthwhile return on investment that can come from crowdsourced security.
For all that the $2 million paid out by blockchain tech company Polygon to ethical hacker Gerhard Wagner for a ‘double spend’ vulnerability was an eye-watering sum, this figure should be compared against the losses potentially averted.
The flaw effectively meant an attacker could increase their cryptocurrency withdrawals by a factor of up to 233, with $3.8 million potentially turning into $850 million for instance.
Acknowledging, and learning from, mistakes
A severe, longstanding vulnerability in the OWASP ModSecurity Core Rule Set (CRS) was a “bang on the ear” for the project’s maintainers when it was discovered, OWASP CRS co-lead Christian Folini told The Daily Swig in November.
Now patched, the critical, complete rule set bypass prompted the ModSec team to implement new practices, guidelines, and a bug bounty program to further secure the technology.
To his credit, Folini took the blame for inadvertently introducing two bugs after his team took over the dormant project in 2016, and resolved to “look at it as a chance for growth and development”.
Quick-fire fixes
With the time between vulnerability disclosure and in-the-wild exploitation narrowing to a matter of days or even hours, credit is due to the vendors, maintainers, and end users who quickly released or applied patches throughout 2021.
This includes Tonic, the registrar for Tonga’s country code top-level domain (ccTLD), which in December patched in under 24 hours a critical vulnerability in their website that opened the door to potential attacks against.to domains operated by Google, Amazon, and many others.
Well done also to the maintainers of ubiquitous Java logging library Apache Log4j for rushing out a patch against the potentially ruinous Log4Shell vulnerability in Dacember, and, for its transparency in communicating high severity security vulnerabilities, VMWare.
A commendation is also warranted for two eagle-eyed Irish citizens who denied scammers a golden phishing opportunity in July after spotting a typo in the URL for Ireland’s new Covid-19 recovery certificate portal and registering the correctly spelled domain.






