Burp Suite Professional is the cornerstone of
Microsoft’s pentesting toolkit
We caught up with Microsoft Azure's Taylor O'Dell as he shares his insights on how Burp Suite Professional has become an indispensable tool in identifying and mitigating vulnerabilities in their web applications.
Key highlights
Using Burp Suite to help identify an application's endpoints and decide what is, and isn’t, in scope for testing. Extending Burp Suite’s capabilities with community-created BApp extensions. The prevalence of Burp Suite amongst Microsoft Azure’s Security Engineers.
Gaining visibility over complex attack
surface
At this stage, features such as the advanced filtering options and global search help him remove some of the inevitable noise that comes from testing complex applications.
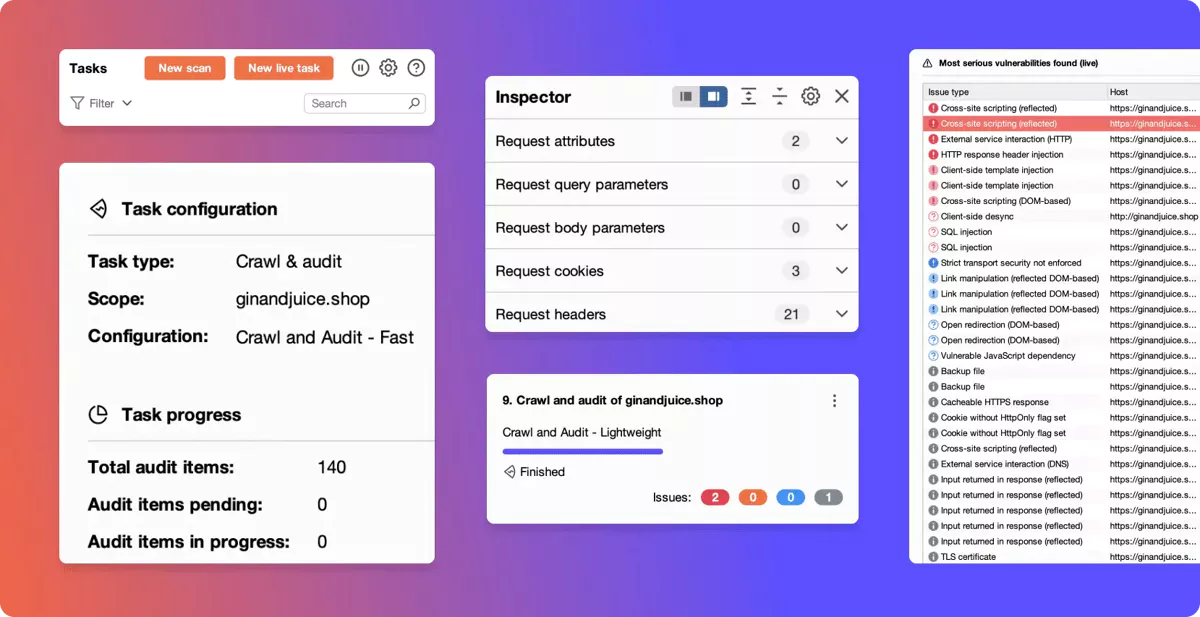
Turning scan results into actionable
insights
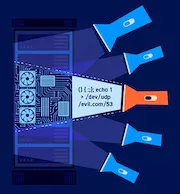
Detecting invisible, asynchronous
vulnerabilities
Harnessing the power of the community
The library of community-created extensions also allows him to add specific functionality to Burp that simplifies testing specific technologies. For example, he uses the JSON Web Tokens extension when testing applications that use JWTs as part of an authentication flow or session management mechanism. This enables him to more easily spot when the server issues JWTs and provides additional Repeater views for manipulating tokens without having to manually decode and re-encode them.
Demonstrating impact and enabling
remediation
Burp Suite provides details for any issues identified during scanning, along with evidence for the issue in the form of the request/response sequence that forms the attack vector. Taylor uses these, along with the free content on PortSwigger's Web Security Academy, to help him document his findings and create clear and detailed tickets for the developers charged with remediating the issue.