The latest release of Burp includes a new engine for static analysis of JavaScript code. This enables Burp Scanner to report a range of new vulnerabilities, including:
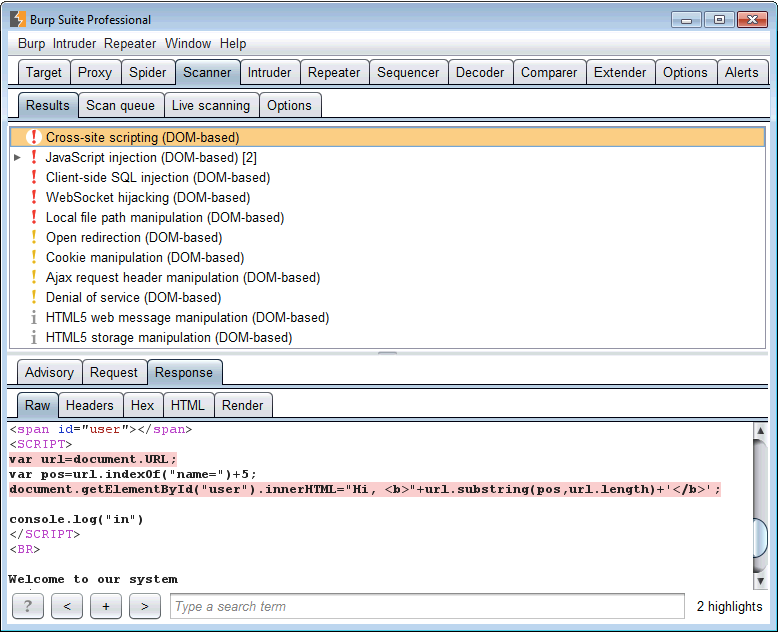
In the initial release, the new functionality is officially experimental, and will be enhanced in future releases based on user feedback. The key areas for further enhancement are as follows:
Despite the above opportunities for enhancement, the current functionality is sufficiently powerful that it would be wrong for us to sit on it any longer, and it's time for users to try it out in real-world situations. Feedback is actively welcomed about the new capabilities, to help drive the above and other improvements.
How does Burp's code analysis work? We don't simply match suspicious code based on patterns, which is too error-prone and only finds the simplest bugs. We don't execute the code, or fuzz the DOM in an instrumented browser, as this can lead to worse performance problems, many missed vulnerabilities, and poor code coverage due to missed execution branches. We don't employ any external dependencies as these can be brittle and a pain for users to set up.
Rather, Burp contains a home-grown language parser and dataflow analysis engine. We identify places in the code where data is read from potentially tainted sources within the DOM, and trace this data through possible execution paths in the code. If the data can reach a dangerous sink, then a potential vulnerability is reported. This is not, of course, a new approach to static code analysis, but there are many challenges in the details that we believe we have solved in novel and effective ways.
Have fun!