The latest version of Burp has a new feature: SSL pass through. You can use this feature to specify destination web servers for which Burp Proxy will directly pass through SSL connections:
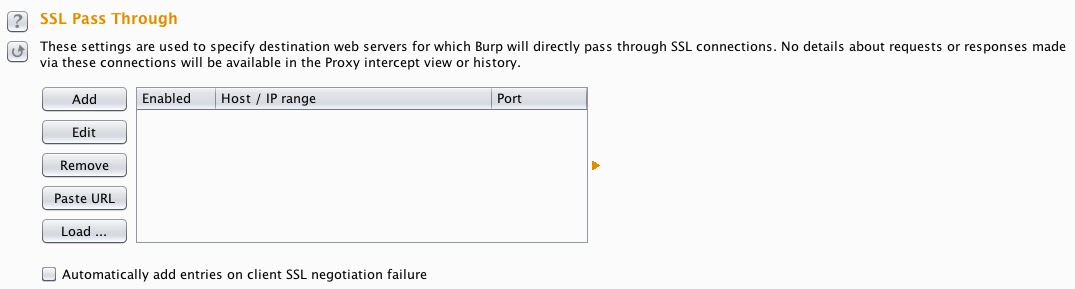
This feature can be useful in cases where it is not straightforward to eliminate SSL errors on the client - for example, in mobile applications that perform SSL certificate pinning. Of course, if you pass through SSL connections, then Burp will not break the SSL tunnel, and no details about requests or responses made via these connections will be available in the Proxy intercept view or history. Nonetheless, using SSL pass through can sometimes enable you to perform some limited testing. If the application uses multiple domains, or uses a mix of HTTP and HTTPS connections, then passing through SSL connections to specific problematic servers still enables you to work on other traffic using Burp in the normal way.
As an example, suppose you encounter a domain where you are not able to get your client device to negotiate SSL correctly. This should be obvious enough in the client, and Burp will also alert you:
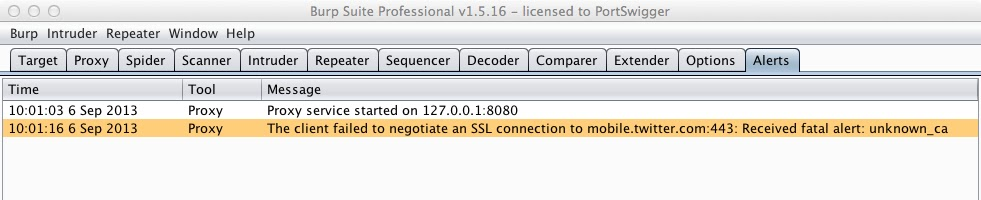
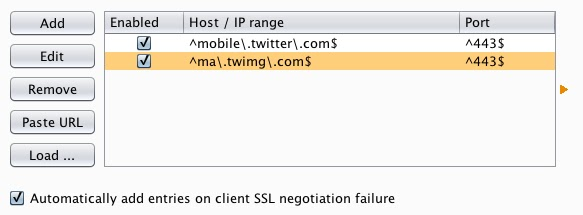
To work around this problem, you can add the problematic server to Burp's SSL pass through list:
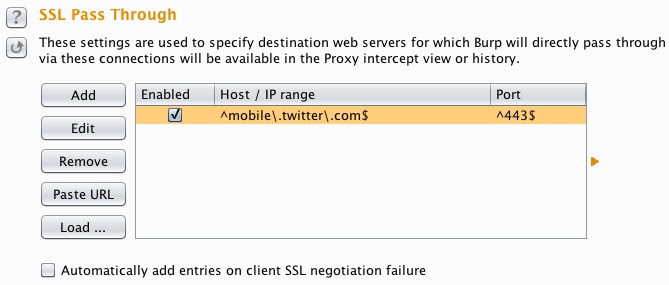
Requests to this server will now pass straight through Burp, and your client can connect in the normal way.
The option to automatically add entries to the SSL pass through list on client SSL negotiation failure can be useful if you aren't sure exactly which domains the application is using, and don't want to have to manually populate the list. If you enable this option, then if your client fails to negotiate SSL connections with any other servers, these will be automatically added to the list, and Burp will alert you:
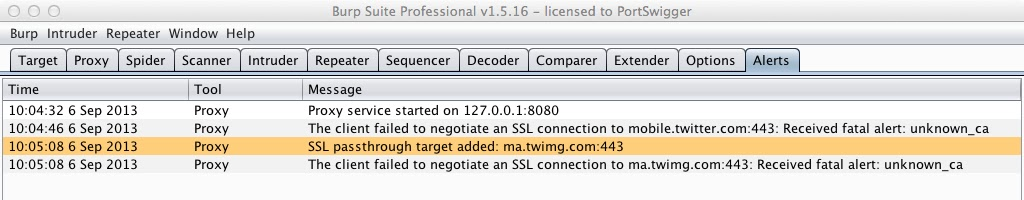
It is not recommended to generally enable the automatic addition of pass through servers automatically, because if your client happens to encounter a one-off problem that causes it to fail an negotiation, then no further SSL connections to that host will be intercepted, until you remove the server from the pass through list.