For Pro users, Burp now includes a function to analyse a target web application and tell you how many static and dynamic URLs it contains, and how many parameters each URL takes. This can help you assess how much effort a penetration testing engagement is likely to involve, and can help you decide where to focus your attention during the test itself.
To access this feature, you select one or more hosts or branches within the site map, and launch it using the context menu. The summarised information looks like this:
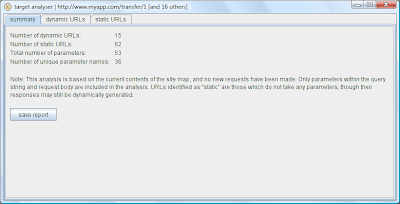
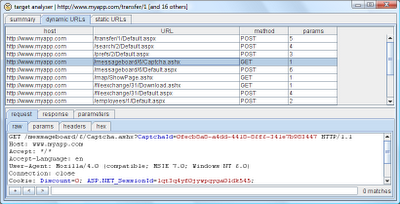
And you can drill down into more detail about individual URLs:
You can also export all of this information as an HTML report, which you can attach to client proposals and reports to show the attack surface you have covered.
A couple of caveats should be noted. Firstly, this function only analyses the content already captured within the site map, so you should ensure that you have fully browsed or spidered all of the application's content and functionality before running it. Secondly, URLs are deemed to be "static" if they no not take any parameters in the URL or message body; however the responses from these URLs may still be dynamically generated by the application.