When you send a request to Intruder to perform custom automated attacks, it makes a guess at where you will want to place your attack payloads. By default, it places payload markers around the values of each URL and body parameter, and each cookie value. If you've ever tried to attack a SOAP request using Intruder, you'll know that this auto-placement doesn't help you very much.
In the new release, auto-placement also supports XML request bodies, and by default places payload markers around the values of each XML element and attribute. If you need to fuzz several SOAP requests, this will now be a simple task of sending each request to Intruder, and starting an attack using the default payload positions:
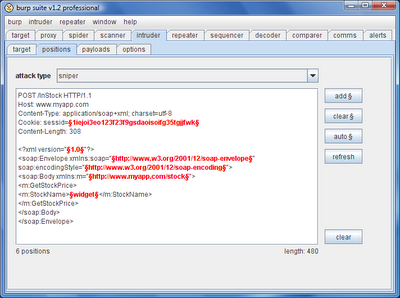
The new support for parameters in XML request bodies is used elsewhere within the new release, including automated vulnerability scanning, of which more shortly.