This release adds some new options to Burp Proxy for configuring the server SSL certificates that are presented to your browser. Use of these options can eliminate some SSL issues that arise when using an intercepting proxy:
You can eliminate SSL alerts in your browser, and the need to create SSL exceptions in Firefox.
Where web pages load SSL-protected items from other domains, you can ensure that these are properly loaded by the browser, without the need to first manually accept the proxy's SSL certificate for each referenced domain.
You can work with thick client applications that refuse to connect to the server if an invalid SSL certificate is received.
The new options for handling server certificates can be configured individually for each proxy listener, and look like this:
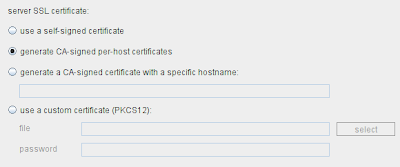
These options are explained more fully below:
use a self-signed certificate - This is the default option in previous releases of Burp. A simple self-signed SSL certificate is presented to your browser, which always causes an SSL alert.
generate CA-signed per-host certificates - This is the new default option. Upon installation, Burp creates a unique, self-signed CA certificate, and stores this on your computer to use every time Burp is run. Each time you connect to an SSL-protected website, Burp generates a server certificate for that host, signed by the CA certificate. You can install Burp's CA certificate as a trusted root in your browser (see instructions below), so that the per-host certificates are accepted without any alerts.
generate a CA-signed certificate with a specific hostname - This is similar to the preceding option, however Burp will generate a single host certificate to use with every SSL connection, using the hostname you specify. You should use this option if you are using invisible proxy mode with SSL connections - in this scenario, per-host certificates cannot be generated because the browser does not send a CONNECT request, and so the SSL negotiation precedes the receipt of the host information from the browser. The fixed host certificate is signed by Burp's CA certificate, which you can install in your browser (see instructions below), so that the host certificate is accepted without any alerts (provided you specify the correct hostname).
use a custom certificate - This option was supported previously, and enables you to configure a specific certificate to present to your browser. This option should be used if the application uses a client which requires a specific server certificate (e.g. with a given serial number or certification chain). If the client simply requires a valid server certificate for the application domain, it is normally easier and quicker to use auto-generation of per-host certificates, as described above.
To make full use of Burp's CA-signed host certificates, you will need to install Burp's CA certificate as a trusted root in your browser. Note: If you install a trusted root certificate in your browser, then an attacker who has the private key for that certificate may be able to man-in-the-middle your SSL connections without obvious detection, even when you are not using an intercepting proxy. To protect against this, Burp generates a unique CA certificate for each installation, and the private key for this certificate is stored on your computer, in a platform-dependent location. If untrusted people can read local data on your computer, you may not wish to install Burp's CA certificate.
To install Burp's CA certificate on IE, perform the following steps:
If you have previously installed a different CA certificate generated by Burp, you should first remove it (see instructions below).
Configure your browser to use Burp as its proxy, and configure Burp's proxy listener to generate CA-signed per-host certificates.
Visit any SSL-protected URL. If you receive a warning, click "Continue to this website (not recommended)".
Click on the "Certificate error" button in the address bar.
Click "View certificates".
Go to the "Certification Path" tab.
Select the root certificate in the tree (PortSwigger CA).
Click "View Certificate".
Click "Install Certificate".
In the Certificate Import Wizard, select "Place all certificates in the following store".
Click "Browse".
Select "Trusted Root Certification Authorities".
Click "OK".
Complete the wizard.
Click "Yes" on the security warning.
Close all dialogs and restart IE.
If everything has worked, when you visit SSL-protected URLs using Burp you should see a valid certificate chain:

To remove a Burp CA certificate which you have previously installed on IE, perform the following steps:
Go to Tools Internet Options.
Go to the Content tab.
Click "Certificates".
Go to the Trusted Root Certification Authorities tab.
Select the PortSwigger CA entry in the list.
Click "Remove".
Click "Yes" in each confirmation dialog.
Confirm that the PortSwigger CA entry has been removed.
Restart IE.
To install Burp's CA certificate on Firefox, perform the following steps:
If you have previously installed a different CA certificate generated by Burp, you should first remove it (see instructions below).
Configure your browser to use Burp as its proxy, and configure Burp's proxy listener to generate CA-signed per-host certificates.
Visit any SSL-protected URL.
On the "Secure Connection Failed" screen, click on "Or you can add an exception", and then click "Add Exception".
Click "Get Certificate", then click "View".
Select the root certificate in the tree (PortSwigger CA).
Click "Export" and save the certificate somewhere.
Click "Close" on the Certificate Viewer dialog, and "Cancel" on the "Add Security Exception" dialog.
Go to Tools Options.
Click "Advanced".
Go to the Encryption tab.
Click "View Certificates".
Go to the Authorities tab.
Click "Import" and select the certificate file that you previously saved.
On the "Downloading Certificate" dialog, check the box "Trust this CA to identify web sites", and click "OK".
Close all dialogs and restart Firefox.
If everything has worked, when you visit SSL-protected URLs using Burp you should see a valid certificate chain:

To remove a Burp CA certificate which you have previously installed on Firefox, perform the following steps:
Go to Tools Options.
Click "Advanced".
Go to the Encryption tab.
Click "View Certificates".
Go to the Authorities tab.
Select the PortSwigger CA entry in the list (this is a sub-entry under PortSwigger).
Click "Delete".
Click "OK" in the confirmation dialog.
Confirm that the PortSwigger CA entry has been removed.
Restart Firefox.
Thanks are due to Rogan Dawes of WebScarab fame for prompting me to add this feature and sharing some sample code for implementing it.


