In our article "Exploiting XSS - Injecting in to Direct HTML" we started to explore the concept of exploiting XSS in various contexts by identifying the syntactic context of the response. In this article we demonstrate some methods of modifying your input when injecting in to various Tag Attributes.
By modifying your input appropriately, you can help ensure that the JavaScript included in your payload is executed as intended.
The example uses a version of "Mutillidae" taken from OWASP's Broken Web Application Project. Find out how to download, install and use this project. The page used is the XSS Document view page; you can access this page from the vulnerabilities console.
Tag Attribute
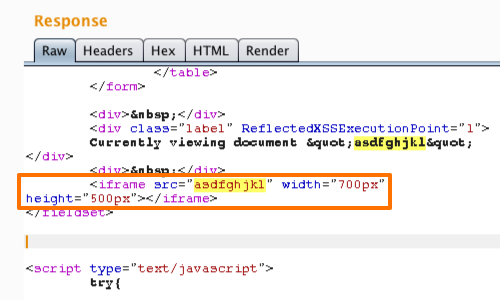
Suppose that after inputting a benign string (asdfghjkl) to each entry point in an application, the returned page contains the following:
<tag attribute="asdfghjkl" name="example" value="1">
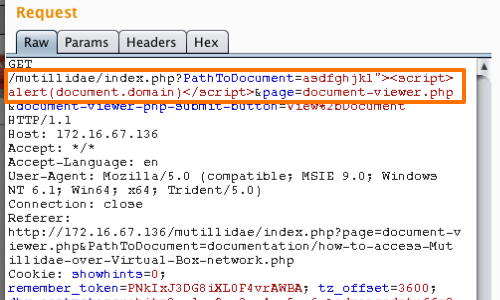
One obvious way to craft an XSS exploit is to terminate the double quotation marks that enclose the attribute value, close the attribute tag, and then employ some means of introducing JavaScript, such as a script tag. For example:
"><script>alert(document.domain)</script>
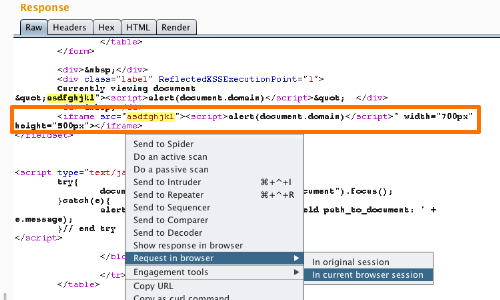
Check that the payload appears unmodified in the response, before testing the exploit in your browser.
You can use Burp's "Request in browser" function to perform this check.
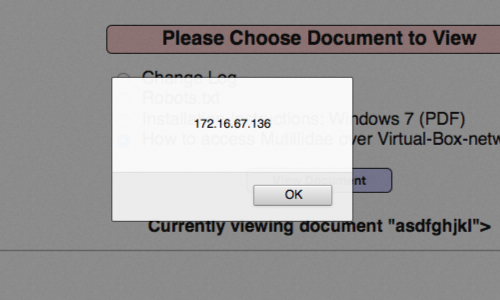
If your exploit has executed correctly your browser should render a pop-up alert.
Event Handlers
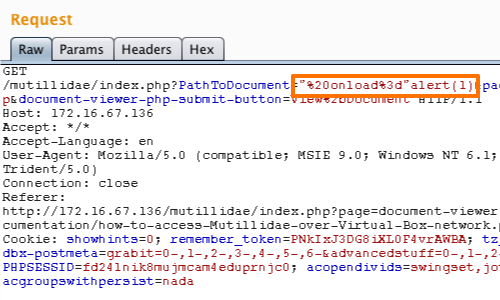
An alternative method in this situation, which may bypass certain input filters, is to remain within the attribute tag itself but inject an event handler containing JavaScript. For example:
" onload="alert(1)
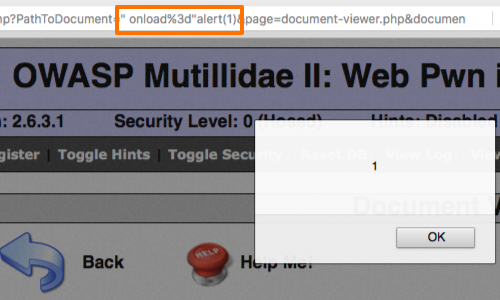
In this example we can see that the JavaScript executes without requiring any user interaction.
Numerous event handlers can be used with various tags to cause a script to execute. Another example that requires no user interaction is:
<xml onreadystatechange=alert(1)>
Hidden Input
XSS in hidden inputs is frequently very difficult to exploit because typical JavaScript events like onmouseover and onfocus can't be triggered due to the element being invisible.
However, with some user interaction it is possible to execute an XSS payload. You can read more about this technique on our blog post - XSS in Hidden Input Fields.
Related articles:


