To find many types of vulnerabilities, Burp performs active scanning, this involves sending requests to an application to probe for vulnerabilities. When a vulnerability is reported you may want to perform a manual verification.
Burp is designed to support the activities of a hands-on web application tester. It lets you combine manual and automated techniques effectively. You can use this functionality to easily repeat or modify requests generated by Burp Scanner.
In this example we'll be manually verifying a XSS (cross-site scripting vulnerability found in the WebGoat training application. The example uses a version of “WebGoat” taken from OWASP’s Broken Web Application Project. Find out how to download, install and use this project.
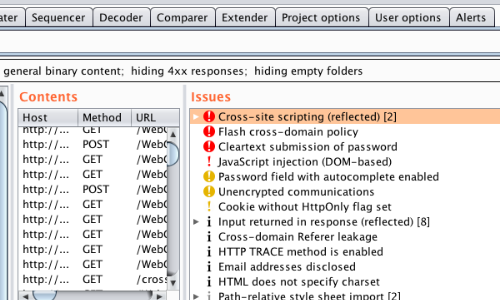
Having run Burp Scanner, Issues can be viewed in the Target > Site map tab.
To help you understand and verify an issue, Burp provides a customized vulnerability advisory containing:
A standard description of the issue type and its remediation.
A description of any specific features that apply to the issue and affect its remediation.
The full requests and responses that were the basis for reporting the issue.
Details of any interactions with the Burp Collaborator server that were the basis for reporting the issue.
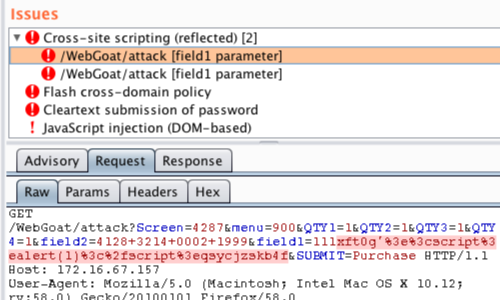
If a payload has been used to trigger an issue it will be highlighted in the request tab.
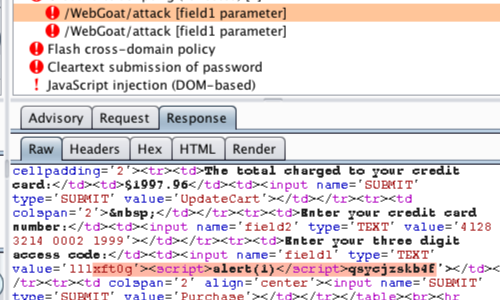
If a payload has been reflected in the response, it is highlighted in the Response tab.
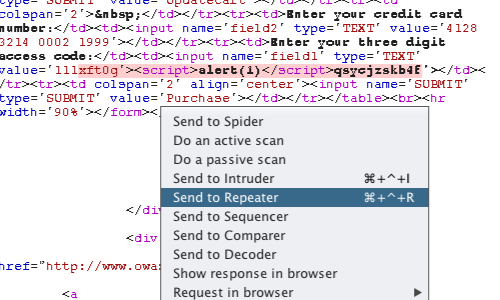
Right clicking on the request / response will bring up the context menu.
You can use the context to send the request to other tools within Burp Suite.
Burp Repeater is a simple tool for manually manipulating and reissuing individual HTTP requests, and analyzing the application's responses.
This functionality is ideal for verifying issues.
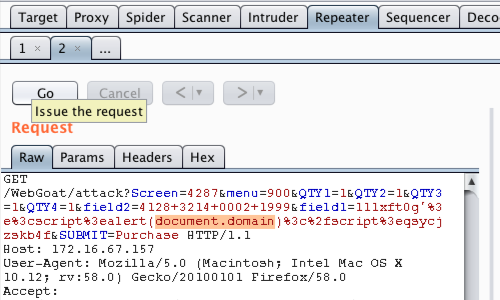
Each tab contains the controls to issue requests and navigate the request history. The target server to which the request will be sent is shown - you can click on the target details to change these.
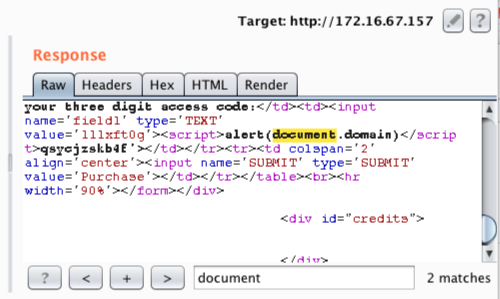
In this example we can confirm the payload is reflected in the response using the search function.
For other vulnerabilities we might search the response for error messages, response differences, leaked data etc.
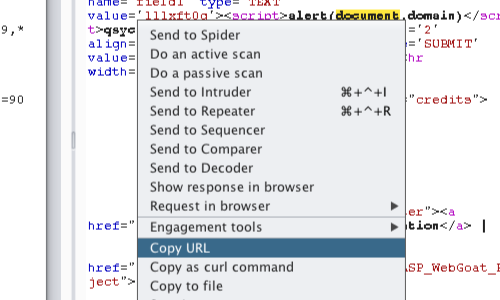
Additionally, the context menu has various options that allow you to check that the vulnerability executes in your browser.
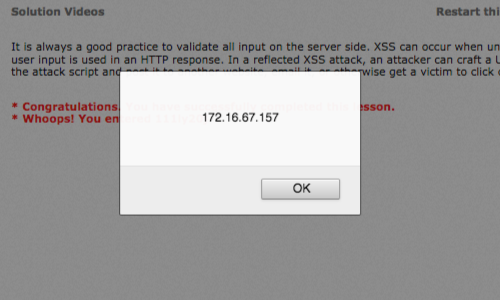
In this example we're able to produce a working POC in the browser.

This article provides an example of verifying one vulnerability. The Burp Methodology provides step-by-step examples of manual testing for numerous issues.


