Efficient discovery, comprehensive application mapping,
and advanced extensibility.
We interviewed a pentester from this organization, who is part of an ethical hacking red team. We spoke to them about their challenges, workflow, and how Burp helps them achieve their goals.
Key highlights
Using the complete toolkit in Burp to streamline all phases of the pentesting workflow. Burp Scanner allows for multi-tasking - capturing low-hanging fruit, while they explore other vulnerabilities manually. Adding extensions to Burp helps them gain even more value from the tools.
Building the sitemap and beginning
recon
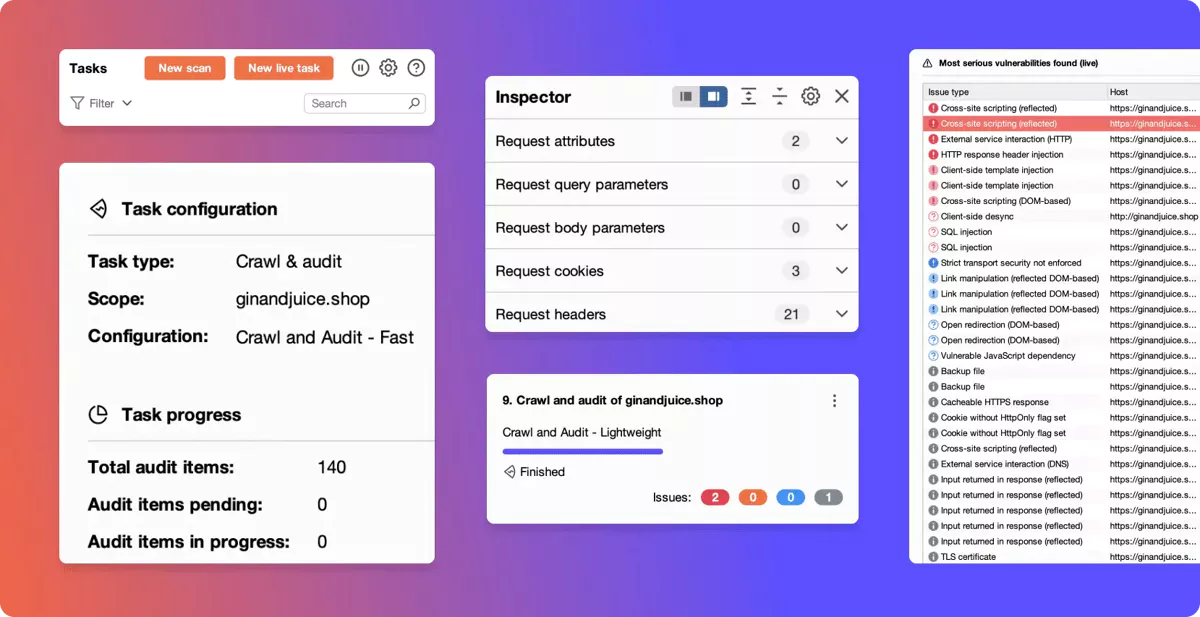
While their focused on exploring high-value vulnerabilities with Proxy and Repeater, they leverage automation through the Scanner.
Identifying vulnerabilities through
automation and manual testing
This is where the Scanner delivers real value for this pentester.
Any potential issues found in the Scanner (and elsewhere) are then sent to Repeater, where they can test different avenues and begin building his POC.
Distilling the results into an actionable
POC
While they don't use Burp’s built-in report generation, they do utilise Repeater to compile reports.
Focus on the vulnerabilities that matter most
Burp Suite Professional is indispensable in their workflow. From the Scanner, to Proxy, Repeater, and more - Burp enables them to focus on finding the vulnerabilities that matter most.
Join over 80,000 security professionals using Burp Suite Professional. Request a fully-featured free trial of the web security tester's toolkit of choice.