How FloQast are streamlining testing workflows and
providing actionable reporting for their
developers.
FloQast offers accounting software to provide workflow automation and close management. We caught up with Owen about his pains when pentesting, and how Burp helps streamline his workflow.
Key highlights
Using Burp to map an application’s full attack surface. Supercharging testing workflows with Burp’s community-powered extensibility. Providing valuable, actionable insight for developers with Burp’s custom issue creation.
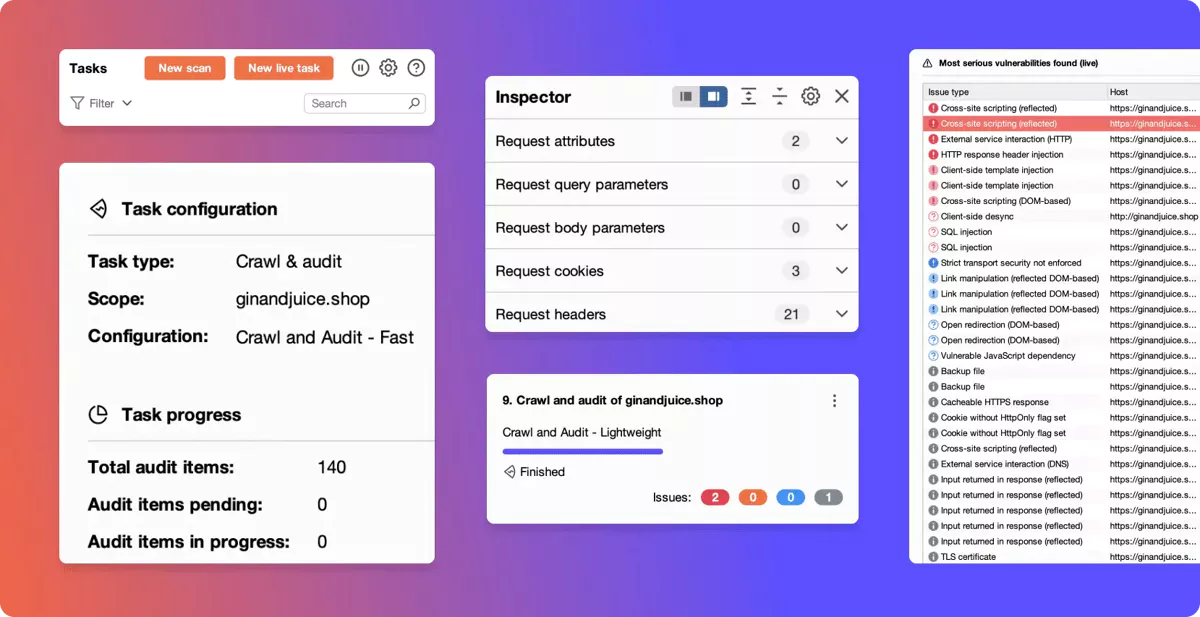
Owen’s workflow in Burp Suite
Professional
Throughout the Discovery, Attack, and Reporting phases of his pentesting workflow, Owen regularly uses a range of Burp Suite Professional’s built-in features and community-created extensions to help overcome these challenges.
Mapping attack surface and API request
structures
Organizing and prioritizing findings for
further investigation
He takes advantage of the built-in note-taking functionality to record what it is he wants to look into so that he can come back to it later, without needing to context-switch from what he's doing currently.
Speeding up the process of probing for
vulnerabilities and catching low-hanging
fruit
Unrivalled features for performing detailed
manual analysis
Fuzzing at scale, without writing a single
line of code
Out-of-the-box detection of otherwise
'invisible' vulnerabilities
Customizable extensibility, powered by the
community
Automated report generation to help present
findings to development teams
A comprehensive toolkit designed to work with
complex applications
80,000 pentesters worldwide, like Owen, are currently using Burp Suite Professional to optimize their security testing. Join them by requesting a fully-featured free trial of the web security tester's toolkit of choice.