
Published: 23 August 2017 at 14:47 UTC
Updated: 12 July 2018 at 14:13 UTC
Burp Suite is privileged to serve as a platform for numerous extensions developed and shared by our community of users. These expand Burp’s capabilities in a range of intriguing ways. That said, many extensions were built to solve a very specific problem, and you might have ideas for how to adapt an extension to better fulfil your needs.
Altering third party Burp extensions used to be pretty difficult, but we’ve recently made sure all Burp extensions are open source and share a similar build process. In this post, I’ll show you just how easy it’s become to customize an extension and build a bespoke Burp environment for effective and efficient audits.
I’ll personalize the Collaborator Everywhere extension by making it inject extra query parameters that are frequently vulnerable to SSRF, as identified by Bugcrowd for their excellent HUNT extension.
Development Environment Prerequisites
First, create your development environment. To edit an extension written in Java, you’ll need to install the Java JDK and Gradle. Extensions written in Python and Ruby don’t have any equivalent requirements, but Git is always useful. This is all you’ll need to build the majority of Burp extensions - Gradle will automatically handle any extension-specific dependencies for you. I’ll use Windows because it’s reliably the most awkward development environment.
Obtain code
The next step is to obtain the code you want to hack up. Find your target extension on https://portswigger.net/bappstore and click the ‘View Source Code’ button. This will land you on a GitHub Page something like https://github.com/portswigger/collaborator-everywhere. To get the code, either click download to get a zip or open a terminal, type git clone https://github.com/portswigger/collaborator-everywhere, and cd into the new folder.
Verify environment (Java only)
Before you make any changes, ensure you can successfully build the jar and load it into Burp. To find out how to build the jar, look for the BuildCommand line in the BappManifest.bmf file. For Collaborator Everywhere, it’s simply gradle fatJar. The EntryPoint line shows where the resulting jar will appear.
Apply & test changes
If you can load the freshly built jar into Burp and it works as expected, you’re ready to make your changes and rebuild.
Collaborator Everywhere reads its payloads from resources/injections, so I’ve simply added an extra line for each parameter I want to inject. For example, the following line adds a GET parameter called 'feed', formatted as a HTTP URL:
param,feed,http://%s/If a particular payload is causing you grief, you can comment it out using a #.
The extension Flow may come in useful for verifying your modifications work as expected - it shows requests made by all Burp components, including the scanner. Here, we can see our modified extension is working as intended:
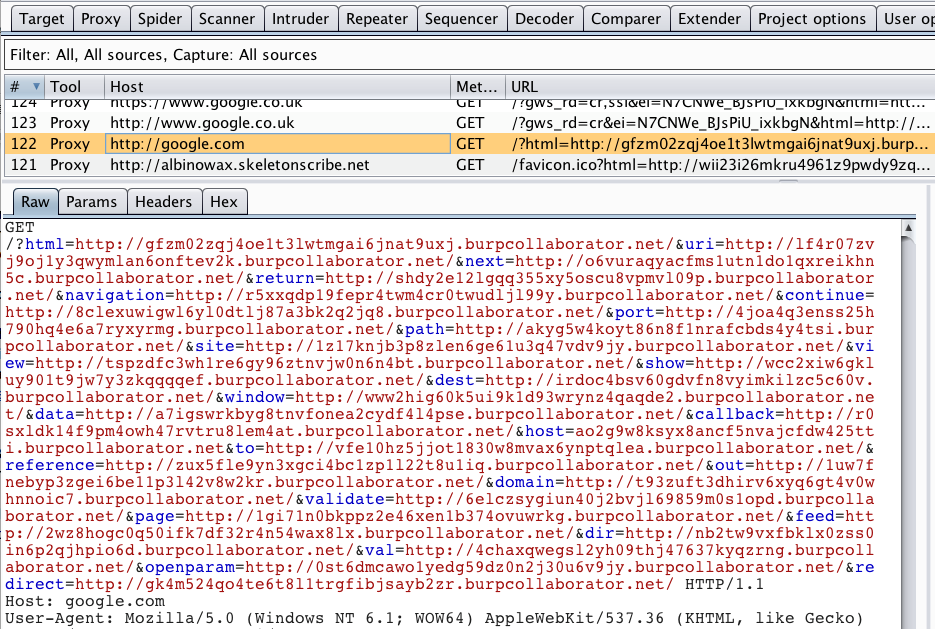
Finally, be aware that innocuous changes may have unexpected side effects.
Conclusion
If you feel like sharing your enhanced extension with the community, feel free to submit your changes back to the PortSwigger repository as a pull request, or release them as a fork. I haven’t pushed my Collaborator Everywhere tweak into an official release because the extra parameters unfortunately upset quite a few websites.
Some extensions may be more difficult to modify than others, but we’ve seen that with a little environment setup, you can modify Burp extensions with impunity.