Burp Suite Professional now has a powerful yet simple scripting language that allows you to quickly build on our world class scanning engine (see our Burp Suite Shorts videos) to create checks for anything your imagination envisages. This is much quicker than writing a BApp extension just to add a scan check.
So we have just released BChecks into beta, and this is a quick look at the language, how it can be used and what for.
BChecks can be used for a variety of different solutions (and this list isn't comprehensive):
... and then all the finds we didn't envisage, but you will.
To give you a flavor of what the language is capable of:
... and more.
As a bit of nostalgia we will revisit a vulnerability which is 22 years old - the indeed infamous CVE-2001-0537 or otherwise known as Cisco level router authentication bypass. This vulnerability was legendary at the time as it allowed you to bypass authentication and execute commands with the highest level of privilege over HTTP for Cisco IOS 11.3 to 12.2 .
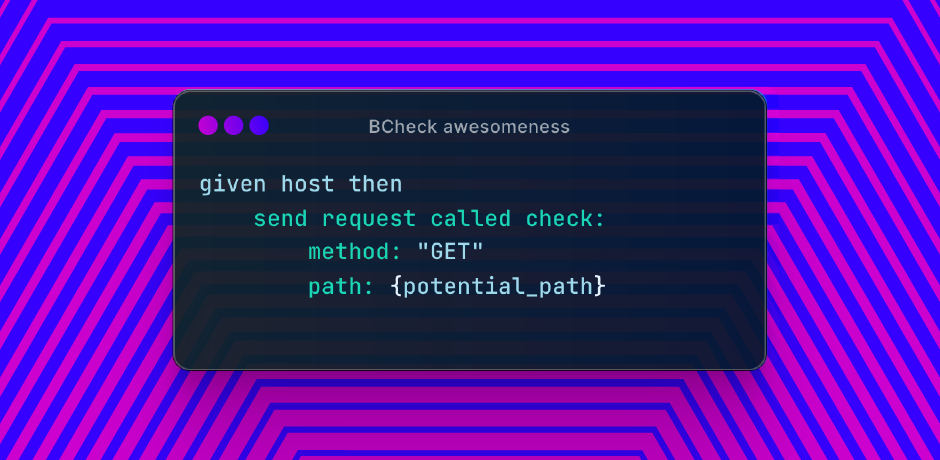
The example BCheck for this issue is below:
metadata:
language: v1-beta
name: "CVE-2001-0537 CISCO Authentication Bypass"
description: "Checks for CVE-2001-0537"
author: "Ollie Whitehouse"
tags: "CVE-2001-0537 CVE"
define:
potential_path =
"/level/16/exec/show%20privilege"
given host then
send request called check:
method: "GET"
path: {potential_path}
# Checks that we get a 200 AND that the output we expect in the result
if {check.response.status_code} is "200" and "Current privilege level is" in {check.response.body} then
report issue:
severity: high
confidence: certain
detail: "Router is vulnerable to the authentication bypass vulnerability CVE-2001-0537"
remediation: "Patch to a non vulnerable version"
end ifWe have a number of other examples over in the BChecks GitHub repo.
These cover:
These cover the various bits of the language's functionality discussed at the top of this post.
To use BChecks (and only BChecks) in a Burp Suite Professional audit, we can configure a custom scan configuration. The important part being the Issues Reported, as shown in the image below. Set this to BCheck generated issue:
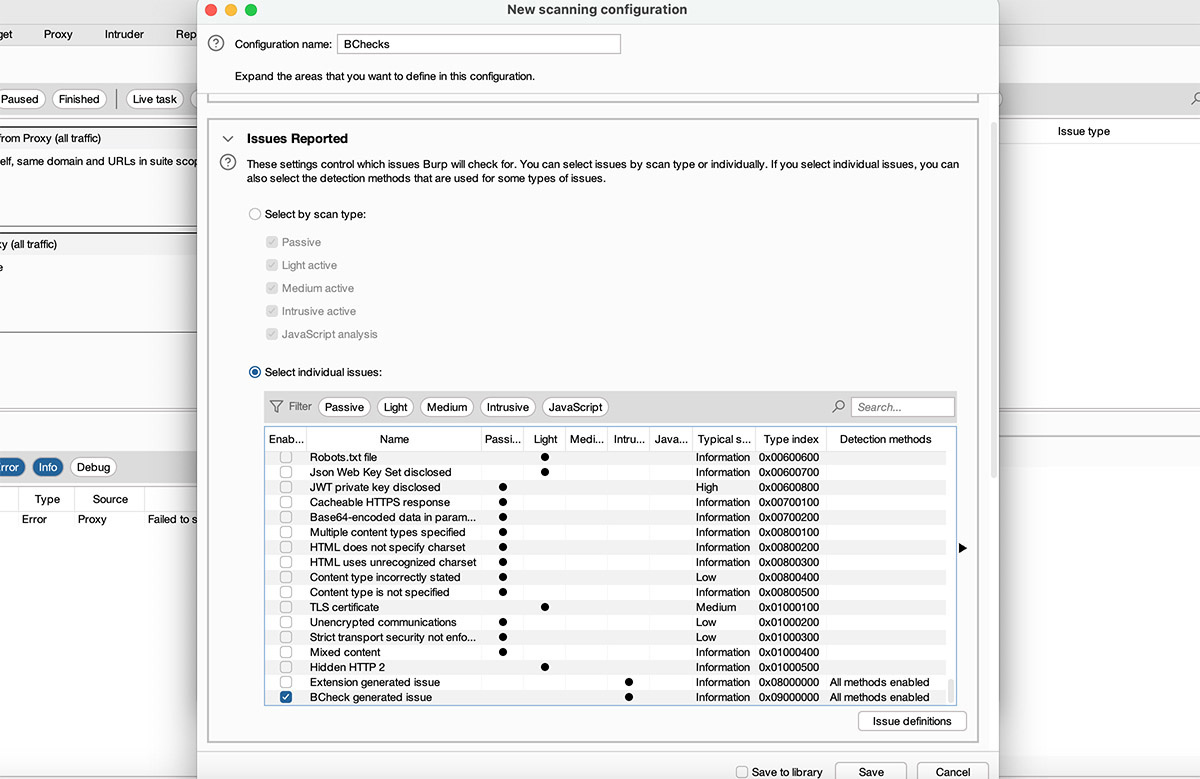
You can create a custom scan configuration that uses only BChecks.
Configuring the scanner in this way will mean that only the BChecks will be executed during the audit phase - expediting the discovery of any vulnerabilities.
We have created a BChecks GitHub repository. This includes example BChecks from PortSwigger, as well as BChecks developed by the Burp Suite community. You'll also find full documentation on our website.
We look forward to accepting pull requests and celebrating your awesome work.