The web vulnerability scanner behind Burp Suite's popularity has more to it than most. Burp Scanner uses PortSwigger's world-leading research to help its users find a wide range of vulnerabilities in web applications, automatically.
Sitting at the core of both Burp Suite DAST and Burp Suite Professional, Burp Scanner is the weapon of choice for over 70,000 users across more than 16,000 organizations.
See more customer stories
of surveyed penetration testers agree that Burp Suite is "best in class" software. Source: TechValidate survey of PortSwigger customers
Burp Scanner's crawl engine cuts through obstacles like CSRF tokens, stateful functionality, and overloaded or volatile URLs like they aren't even there. And with its embedded Chromium browser, it will render and crawl even the JavaScript-heavy applications other web vulnerability scanners struggle with.
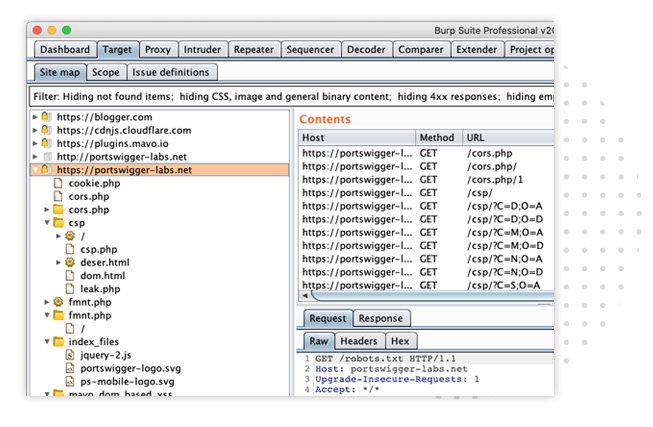
The advanced crawling algorithm used by Burp Scanner builds up a profile of its target in a similar way to a tester. It's designed to handle dynamic content, unstable internet connections, many API definitions, and the vast scale of modern web applications. This means far fewer failed scans - and more attack surface to exploit.
"From the start, Burp Scanner was built to replicate the actions of a skilled manual tester. That approach continues today, and Burp Scanner is powered by the world's leading web security research team."

Burp Scanner saves a huge amount of time and wasted effort. The architecture of modern web applications can create sinkholes that will eat up requests if your web vulnerability scanner isn't prepared. Burp Scanner uses location fingerprinting techniques to identify these areas - dramatically cutting down the number of requests made while testing.

PortSwigger champions innovation. We pride ourselves on having the best security research team in the world. Burp Suite's creator wrote the book that educated a generation of pentesters. And because we regularly unearth new vulnerabilities (like HTTP desync attacks), Burp Scanner users are first to be protected against them - before hackers have a chance to strike.
"Burp Scanner is capable of finding many critical vulnerabilities that even an expert manual tester could easily miss - like deferred asynchronous command injection."

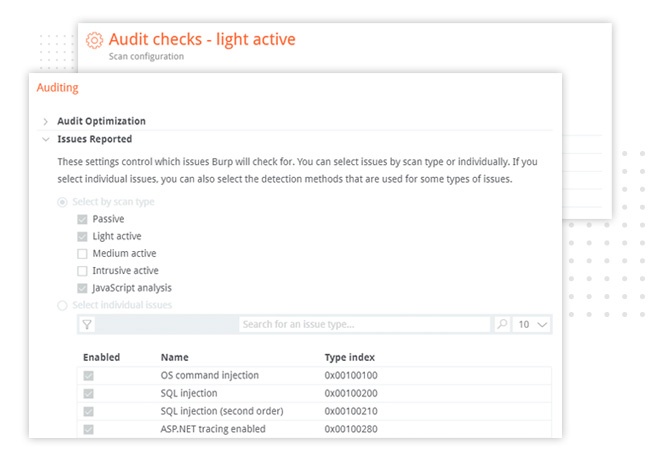
In addition to receiving regular updates, Burp Scanner is capable of exposing a huge list of existing vulnerabilities in web applications. Scan checks can be selected individually or by group, and custom configurations can be saved. For example, a scan configuration could be created to report only vulnerabilities appearing in the OWASP Top 10.
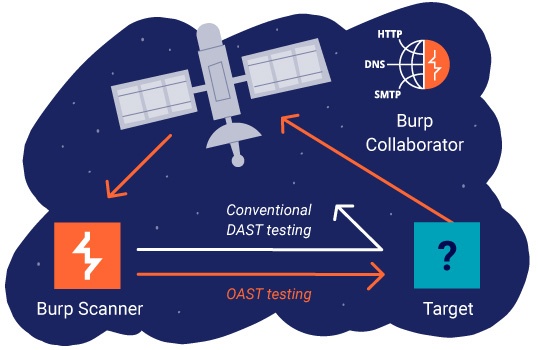
Automated OAST (out-of-band application security testing) was pioneered by PortSwigger. Burp Collaborator identifies interactions between its target and an external server. This allows it to check for bugs invisible to conventional scanners - including asynchronous SQL injection and blind SSRF. Results then appear as standard in Burp Scanner's reports.
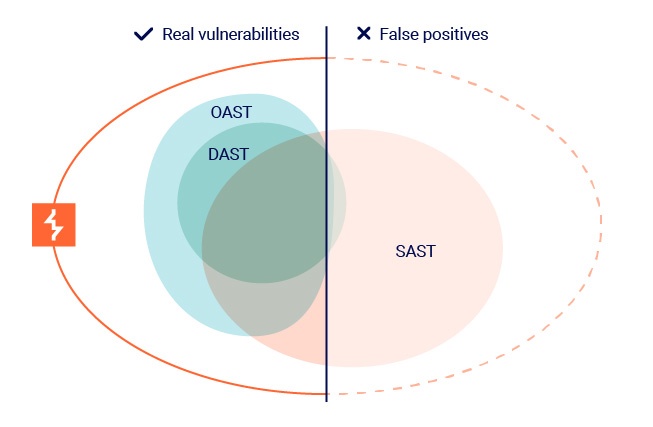
Burp Scanner utilizes a mixed methodology, designed with signal-to-noise ratio in mind. This maximizes coverage, while minimizing the number of false positives returned to the user. OAST testing in particular, produces an extremely low rate of false positives, while opening up new horizons in terms of the types of vulnerabilities it can find.
See more customer stories
Given that Burp Scanner detects the latest web vulnerability types, discovered by PortSwigger Research, eTrends s.r.o. said that it has been critical to their ability to catch vulnerabilities that they cannot with other tools. Source: TechValidate survey of PortSwigger customers
Radek Smolik
Penetration Tester
Sitting at the heart of both Burp Suite Professional and Burp Suite DAST, Burp Scanner is available to suit the needs of both individual pentesters, and whole DevSecOps or security teams.
Automate Burp Scanner. Integrate with CI/CD and enable DevSecOps. Indefinite scalability.
Integrate Burp Scanner with manual pentesting workflows, apply custom scan checks, and much more.
Learn more about web vulnerability scanners. What they are, how they work, and what to look out for.