
What are the best bug bounty hunting tools for you?
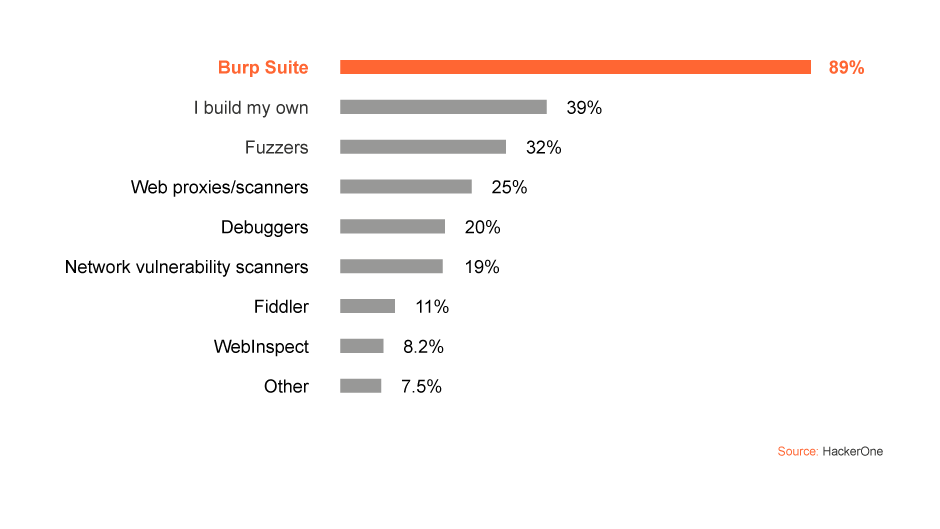
In a 2020 HackerOne report based on the views of over 3,000 respondents, Burp Suite was voted the tool that "helps you most when you're hacking" by 89% of hackers. This was ahead of other bug bounty tools, such as Fiddler (11%) and WebInspect (8.2%).
Are you a beginner just learning the tricks of the trade? Or a seasoned expert looking for a toolkit to take your skills to the next level? Whether you want an accessible gateway to the Burp Suite family, or access to all of the bug bounty tools mentioned on this page, we've got the right solution for you.
Find out more
Burp Suite is made up of many interlinked tools, but a bug bounty hunting workflow will generally start with Burp Proxy. Proxying web traffic allows you to select individual components of a web app for further testing. These items can then be sent to other bug hunting tools within Burp Suite to check for vulnerabilities.
The diagram above shows some of Burp Suite's major components, and where they might sit within different types of workflow. Whether you prefer automated bug bounty tools, a fully manual approach, or a mixture of the two, Burp Suite has you covered. Let's have a closer look at how some of Burp's popular functions work on an individual basis:
We'll admit to a little bias when talking about bug bounty tools. We are, after all, the makers of Burp Suite. So what should you look for when considering which hacking tools to use?
Firstly, we'd recommend choosing a tool with a good community around it - especially if you're just starting out bug bounty hunting. If a tool has a good userbase, you'll be able to pick their brains when you occasionally get stuck.
With this in mind, support from a tool's creator is invaluable if you have a deeper query the user community can't help with. In the case of Burp Suite, customer support is something PortSwigger takes pride in.
Finally, flexibility is a great quality to have in your tools. Flexibility saves having to launch multiple applications to complete a task - streamlining your workflow.
It's important to remember at this point that the hacking tools on this page are by no means the limit of what Burp Suite can do. In fact, we've barely scratched the surface here. Burp Suite isn't called the hacker's Swiss Army knife for nothing. Happy hunting.
Take your skills to the next level with free, online web security training from the creators of Burp Suite.
See the full range of web security solutions provided by PortSwigger.
PortSwigger interviews "hackfluencer" - and Burp Suite power user - Stök.